To be more specific, the application may be able to execute code with system privileges. This issue does not affect macOS users running the latest version of the system software. An out-of-bounds read issue was discovered with the Address Space Layout Randomization feature. A malicious application may be able to exploit this vulnerability to perform denial-of-service attacks. An out-of-bounds write issue was discovered with the feature called rdmsr due to the way memory is handled on some processors. This could allow a malicious application to cause a denial of service or potentially allow code execution with system privileges. An out-of-bounds write issue was discovered in the handling of memory containing the XCPMM request. This may allow a malicious application to cause a denial-of-service or potentially allow code execution with system privileges. And lastly, an out-of-bounds write issue was discovered in the handling of memory containing the XCPMM request. This may allow a malicious application to cause a denial-of-service or potentially allow code execution with system privileges. An out-of-bounds read issue was discovered in the handling of memory containing the XCPMM request. This may allow a malicious application to cause a denial-of-service or potentially allow code execution with system privileges.
macOS (OS X)
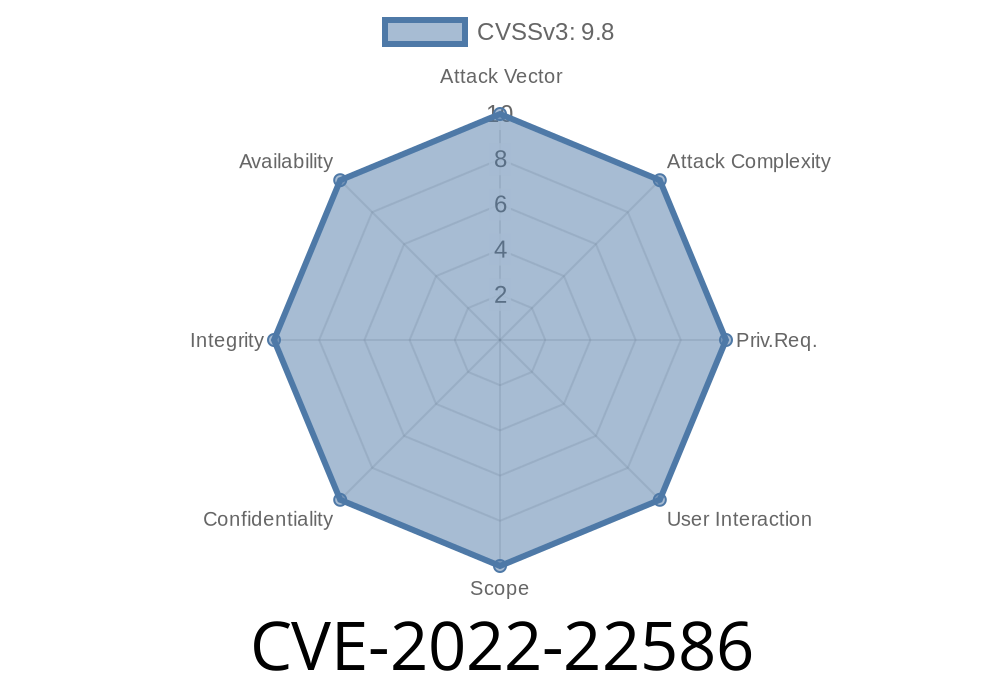
Security Update: CVE-2022-22586
An out-of-bounds read issue was discovered with the Address Space Layout Randomization feature. A malicious application may be able to exploit this vulnerability to perform denial-of-service attacks. An out-of-bounds write issue was discovered with the feature called rdmsr due to the way memory is handled on some processors. This could allow a malicious application to cause a denial of service or potentially allow code execution with system privileges. An out-of-bounds write issue was discovered in the handling of memory containing the XCPMM request. This may allow a malicious application to cause a denial-of-service or potentially allow code execution with system privileges. And lastly, an out-of-bounds write issue was discovered in the handling of memory containing the XCPMM request. This may allow a malicious application to cause a denial-of-service or potentially allow code execution with system privileges. An out-of-bounds read issue was discovered in the handling of memory containing the XCPMM request. This may allow a malicious application to cause a denial-of-service or potentially allow code execution with system privileges.
Why use Address Space Layout Randomization?
The Address Space Layout Randomization feature allows an operating system to create a different memory layout for every process. This is important as it makes exploitation more difficult by making it harder for malicious processes to find code they would like to execute.
Timeline
Published on: 03/18/2022 18:15:00 UTC
Last modified on: 03/28/2022 16:50:00 UTC