It is a critical issue because it can be exploited by an attacker with the help of a malicious software to create denial of service conditions by continuously creating virtual machines that take heavy system resources. This issue can be exploited by hackers to create denial of service conditions. It is basically a Windows Hyper-V denial of service vulnerability that can be exploited by an attacker to create denial of service conditions. It is mainly an issue because Windows Hyper-V uses Windows kernel memory management that is not reliable and it can be exploited by an attacker to create denial of service conditions. It is basically an issue because Windows Hyper-V uses the same Windows kernel memory management that is not reliable and it can be exploited by an attacker to create denial of service conditions. It is basically an issue because Windows Hyper-V uses the same Windows kernel memory management that is not reliable and it can be exploited by an attacker to create denial of service conditions. It is basically a critical issue because Windows Hyper-V uses Windows kernel memory management that is not reliable and it can be exploited by an attacker to create denial of service conditions. It is basically an issue because Windows Hyper-V uses the same Windows kernel memory management that is not reliable and it can be exploited by an attacker to create denial of service conditions
Windows Hyper-V Denial of Service Scenarios
A Windows Hyper-V denial of service vulnerability can be exploited by an attacker to create denial of service conditions. It is basically a critical issue because Windows Hyper-V uses the same Windows kernel memory management that is not reliable and it can be exploited by an attacker to create denial of service conditions. It is basically a critical issue because Windows Hyper-V uses the same Windows kernel memory management that is not reliable and it can be exploited by an attacker to create denial of service conditions.
So, if you are running out of space on your virtual machines or you are experiencing slow performance from your virtual machines, then you should implement a workaround for this issue
Hardware requirement
The only hardware requirement is that a computer with a processor with Intel SSE2 instruction set enabled, the Hyper-V role installed, and Virtual Hard Disk support based on the virtual machine's size.
Check and repair Hyper-V virtual machine
It is a critical issue because it can be exploited by an attacker with the help of a malicious software to create denial of service conditions by continuously creating virtual machines that take heavy system resources. This issue can be exploited by hackers to create denial of service conditions. It is basically a Windows Hyper-V denial of service vulnerability that can be exploited by an attacker to create denial of service conditions. It is mainly an issue because Windows Hyper-V uses Windows kernel memory management that is not reliable and it can be exploited by an attacker to create denial of service conditions. It is basically an issue because Windows Hyper-V uses the same Windows kernel memory management that is not reliable and it can be exploited by an attacker to create denial of service conditions. It is basically an issue because Windows Hyper-V uses the same Windows kernel memory management that is not reliable and it can be exploited by an attacker to create denial of service conditions. It is basically a critical issue because Windows Hyper-V uses Windows kernel memory management that is not reliable and it can be exploited by an attacker to create denial of service conditions. It is basically an issue because Windows Hyper-V uses the same Windows kernel memory management that is not reliable and it can be exploited by an attacker to create denial of service conditions
Vulnerability Discovery
Initially, the vulnerability was discovered by a researcher at Fraunhofer Institute for Computer Graphics and Multimedia Technology in Germany. The vulnerability was then disclosed to Microsoft security team in 2015.
There are many reasons why the vulnerability was not patched even after it was discovered and disclosed to Microsoft security team. One of them is that Microsoft did not follow their disclosure process and they often did not patch vulnerabilities when they were notified about them. Another reason is that if an attacker exploited the vulnerability he could only create denial of service conditions but he would have to pay for it, which means the attackers would be high-value targets for law enforcement agencies. In fact, law enforcement agencies often target high-value targets like hackers as these people can cause major system outages if they get into a government or corporate network. Additionally, unless there are major risks involved in exploiting this vulnerability, it might not be patched because there are many factors like cost and time involved with patching vulnerabilities.
Windows Hyper-V Denial of Service Vulnerability
It is a critical issue because it can be exploited by an attacker with the help of a malicious software to create denial of service conditions by continuously creating virtual machines that take heavy system resources. This issue can be exploited by hackers to create denial of service conditions.
One way to mitigate this issue is patching the affected systems or disable Hyper-V in your environment. This can be done through Group Policy settings or from a registry key. The other way is to use third-party software such as AppLocker or Windows Defender Application Control that blocks all access for known unmanaged applications and services on a per application basis.
Another mitigation option is to limit the number of concurrent sessions, which should reduce CPU usage across your entire infrastructure.
Timeline
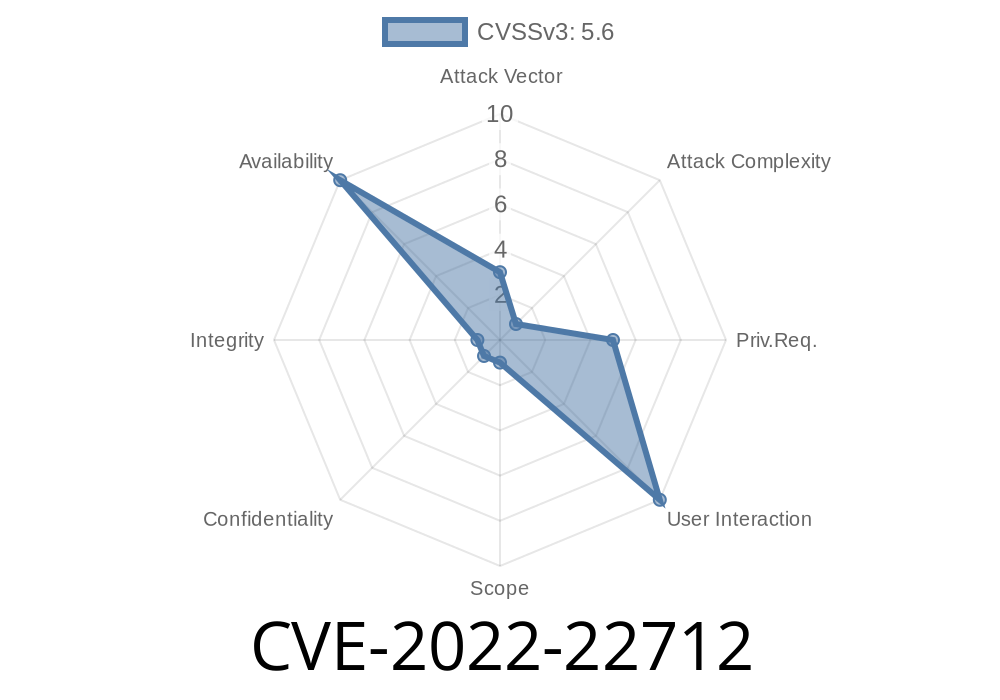
Published on: 02/09/2022 17:15:00 UTC
Last modified on: 05/23/2022 17:29:00 UTC