This vulnerability can be exploited by local attackers through the insecure printing of malicious documents on a vulnerable system. By sending malicious print jobs to an affected system, an attacker may be able to execute arbitrary code and gain access to the system. A low privileged user may be able to execute a remote code and gain elevated privileges. Additionally, a remote attacker may be able to send a specially crafted print job to an affected system and exploit the vulnerability to execute arbitrary code and gain access to the system. An attacker may leverage this vulnerability to run a malicious code on a low privileged user account and gain elevated privileges on the system. Another possible scenario is that an attacker may be able to run a specially crafted print job on an affected system and exploit the vulnerability to gain access to the system. Moreover, an attacker may be able to send a malicious print job to a vulnerable system and exploit the vulnerability to run a malicious code on the system and gain access to the system. Another possible scenario is that an attacker may be able to run a malicious print job on a vulnerable system and exploit the vulnerability to run a malicious code on the system and gain access to the system
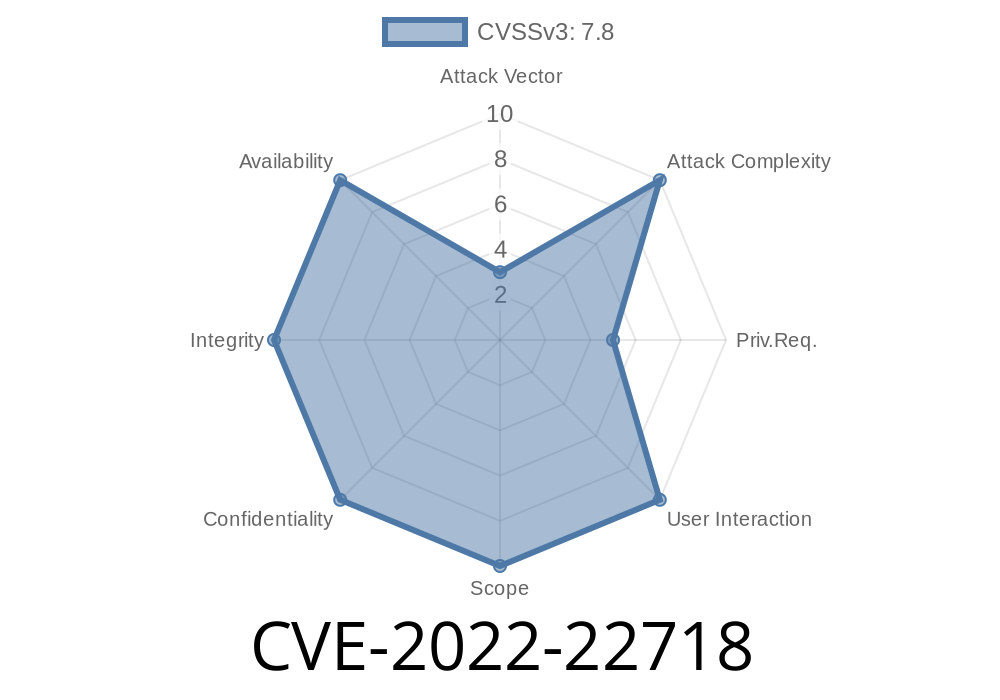
Microsoft Office CVEs CVE-2017-0199
This vulnerability can be exploited by local attackers through the insecure printing of malicious documents on a vulnerable system. By sending malicious print jobs to an affected system, an attacker may be able to execute arbitrary code and gain access to the system. A low privileged user may be able to execute a remote code and gain elevated privileges. Additionally, a remote attacker may be able to send a specially crafted print job to an affected system and exploit the vulnerability to execute arbitrary code and gain access to the system. An attacker may leverage this vulnerability to run a malicious code on a low privileged user account and gain elevated privileges on the system. Another possible scenario is that an attacker may be able to run a specially crafted print job on an affected system and exploit the vulnerability to gain access to the system. Moreover, an attacker may be able to send a malicious print job to a vulnerable system and exploit the vulnerability to run a malicious code on the system and gain access to the system. Another possible scenario is that an attacker may be able to run a malicious print job on a vulnerable system and exploit the vulnerability to run a malicious code on the system and gain access to the system
Vulnerability details
The vulnerability is caused by the improper parsing of an EPS file. The EPS file may be generated as a cross-platform format, which will make it easy for attackers to exploit this vulnerability on affected systems. An attacker may leverage this vulnerability to gain access to the system. Another possible scenario is that an attacker may be able to send a malicious print job to a vulnerable system and exploit the vulnerability to execute arbitrary code on the system and gain access to the system.
Vulnerability Scenario
A user is sending a print job to the printer. The print job includes an embedded malicious document. When the print job is displayed, the malicious document opens and executes arbitrary code on the system. The user may be able to gain access to the system or run a remote code.
#1: Remote Code Execution
An attacker can send a specially crafted print job to an affected system and exploit the vulnerability to execute arbitrary code and gain access to the system. This can also allow an attacker to run a malicious code on a low privileged user account and gain elevated privileges on the system.
#2: Elevated Privileges
An attacker can send a specially crafted print job to an affected system and exploit the vulnerability to execute arbitrary code on a low privileged user account and gain elevated privileges on the system. An attacker may leverage this vulnerability to run a malicious code on a low privileged user account and gain elevated privileges on the system.
Timeline
Published on: 02/09/2022 17:15:00 UTC
Last modified on: 05/23/2022 17:29:00 UTC