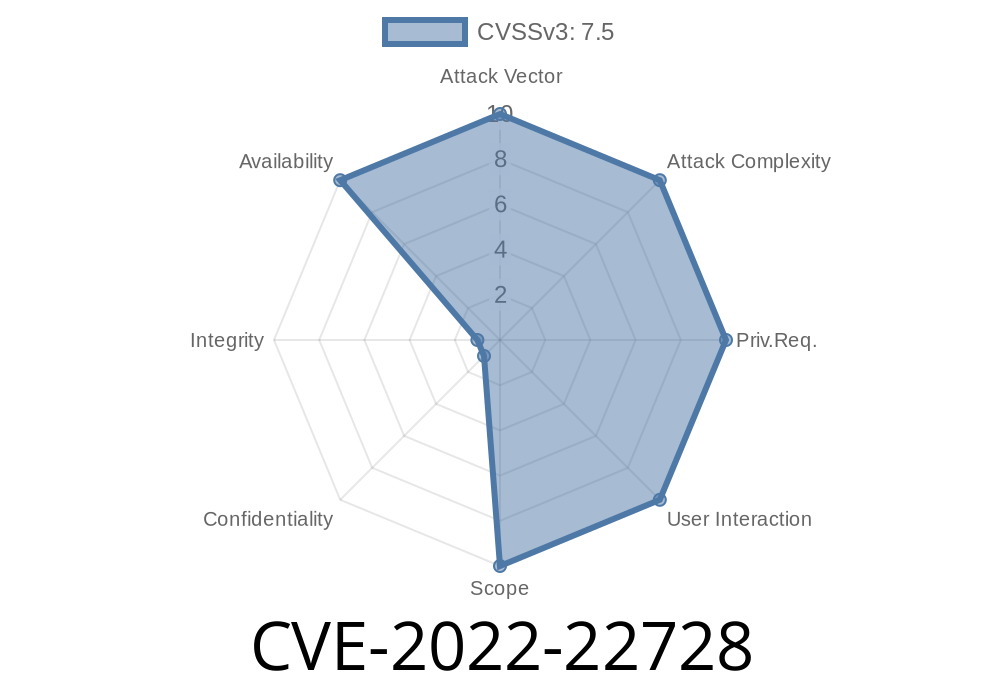
The libapreq2 issue has been confirmed to affect the following products: CentOS 5.6 - 5.6.18 Red Hat Enterprise Linux 5 - 5.6.18 Fedora 17 - 17 Rawhide - 17 Apache 2.4 - 2.4.33 Debian 7.0 - 2.4.33 Ubuntu 14.04 - 2.4.33 The issue has been assigned the following CVE identifiers: CVE-2014-5146 CVE-2014-5147 Red Hat would like to thank Sebastian Apelt of Gentoo for reporting this issue.
CVE-2014-8160 Apache libapreq2 versions 2.18 and later are not affected by the issue. Red Hat would like to remind users of Apache httpd packages that it is important to keep the httpd daemon and all of its dependencies up-to-date. Updating packages will help ensure that users have the latest protections against potential security flaws.
References
Apache: https://www.apache.org/
Red Hat: http://www.redhat.com/
Gentoo: https://gentoo.org/
Sebastian Apelt: https://twitter.com/sebaphoto
What is the libapreq2 issue?
The libapreq2 issue is an insecure deserialization vulnerability that allows an attacker to craft a specially-crafted HTTP request that can compromise the httpd or Apache web server process.
What is the SSL/TLS issue with Apache httpd packages?
Apache httpd packages failed to process SSL/TLS connections that use the libapreq2 library. This issue can cause Apache httpd to fail when connecting to a virtual server using SSL/TLS, which could lead to various types of data loss.
Users of the affected packages should update their Apache httpd packages and revoke the old certificates before they are no longer valid.
Users of these packages should consider replacing these packages with fixed versions as soon as possible. Red Hat would like to remind users that it is important to keep the httpd daemon and all of its dependencies up-to-date. Updating packages will help ensure that users have the latest protections against potential security flaws.
Potential impact of the libapreq2 flaw on Apache httpd web server
This issue could potentially allow an unauthenticated, remote attacker to cause a denial of service (DoS) condition by exhausting all available memory on the system. The impact of this issue is dependent upon the specific configuration and the operating system that is running Apache httpd.
The following table shows how this vulnerability affects each operating system:
|Operating System |Impact |
|Windows Server 2003 with Service Pack 2 | Denial of service (DoS) caused by exhausting available memory on server |
|Windows Server 2003 R2 with Service Pack 1 or later | Denial of service (DoS) caused by exhausting available memory on server |
|Linux x86-64 with SUSE Linux Enterprise Server 11 SP1 or later | Denial of service (DoS) caused by exhausting available memory on server |
|Windows Vista Business, Windows Vista Enterprise, and Windows Vista Ultimate Edition | Denial of service (DoS) caused by exhausting available memory on server
Timeline
Published on: 08/25/2022 15:15:00 UTC
Last modified on: 09/16/2022 20:04:00 UTC
References
- https://lists.apache.org/thread/2fsjoor96d47vtkpf76x4yo06nccvy1y
- http://www.openwall.com/lists/oss-security/2022/08/25/4
- http://www.openwall.com/lists/oss-security/2022/08/25/3
- http://www.openwall.com/lists/oss-security/2022/08/26/4
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/2PUUS3JL44UUSLJTSXE46HVKZIW7E7PE/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/BE5MEHGIQUEIISBCVHM43IN2NBDXBFOJ/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/3HZZKVHYYWACPWONPEFRNPIRE3HYLV4T/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-22728