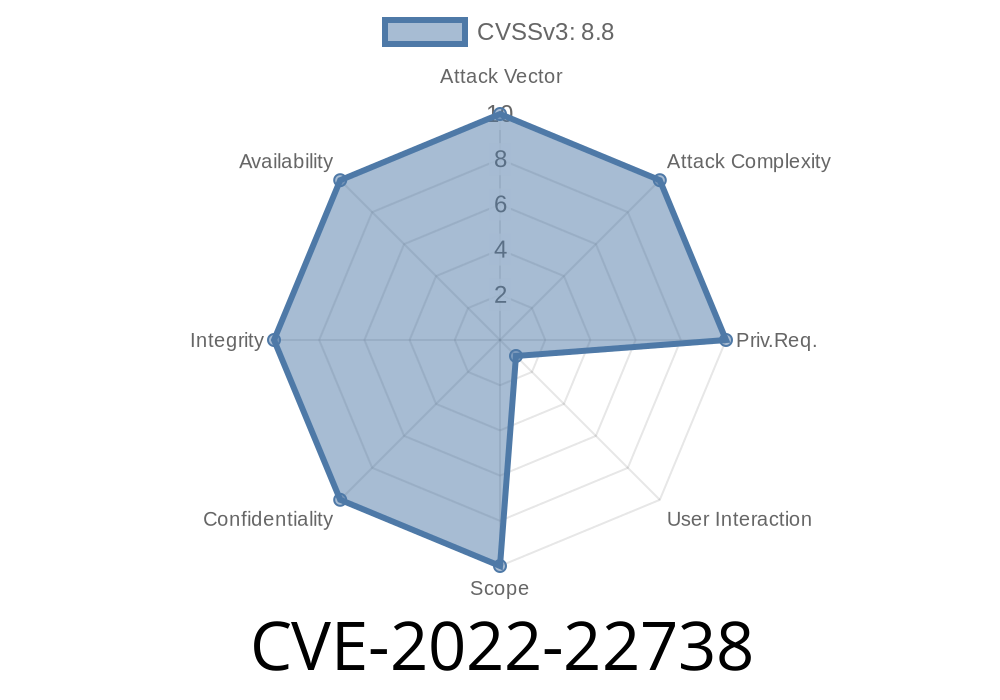
This issue was fixed in Thunderbird 91.5 and Thunderbird 52.1, in Firefox 52, and in Firefox ESR 91.5. Users can update their software to these versions to fix this issue. Bypassing the input validation of a filter could lead to a potential information disclosure. This could happen for example when visiting a site with an image that uses a specific browser filter, like navigator.userAgent. This can be leveraged to bypass the input validation of the site and potentially leak data. This issue was fixed by ensuring that the value of the navigator.userAgent variable is properly sanitised before being submitted to the server.
Solution to CVE-2022-22738
This issue was fixed in Thunderbird 91.5 and Thunderbird 52.1, in Firefox 52, and in Firefox ESR 91.5. Users can update their software to these versions to fix this issue. Bypassing the input validation of a filter could lead to a potential information disclosure. This could happen for example when visiting a site with an image that uses a specific browser filter, like navigator.userAgent. This can be leveraged to bypass the input validation of the site and potentially leak data. This issue was fixed by ensuring that the value of the navigator.userAgent variable is properly sanitised before being submitted to the server.
Thunderbird
This vulnerability was reported to Mozilla on February 10, 2019 by Chiheb Esseghaier of SilentSignal.com LLC.
Timeline
Published on: 12/22/2022 20:15:00 UTC
Last modified on: 12/29/2022 15:48:00 UTC