Mozilla was aware of the issue since late 2015 and issued an advisory with the details. However, the browser’s default setting did not prompt users to click on the image to open it and run the code, giving attackers an even easier way to convince victims to click on the image, running malicious code on the victim’s machine. Attackers could convince their victims to click on malicious links via social engineering or by sending the link via email or instant message. This vulnerability is a good example of how clicking on an image can lead to arbitrary code running on a victim’s machine. It is important to note that this was not a cross-site scripting issue, but an issue with the way Firefox handled image manipulation via drag and drop. The browser is not prompting users to click on the image before it is opened, giving attackers an even easier way to convince victims to click on the image, running malicious code on the victim’s machine.
How Browser Is Vulnerable to Arbitrary Code Execution Through Drag and Drop
So, What’s the Big Deal?
Unfortunately, this vulnerability allowed attackers to exploit the system in arbitrary code execution. Meaning, they could run different malicious codes on a victim’s machine and have complete control over it. The vulnerability also had severe consequences because if a website running with this vulnerability was compromised, any user visiting that website would be susceptible to attack from an attacker exploiting this vulnerability.
The good news is that Mozilla has released a patch for the browser and fixed it which means you shouldn’t experience any further issues with the browser. The bad news? This is not an isolated case or even a new one by itself. There are many other vulnerabilities present in most browsers as users click on files that do not ask them to first open them before running their code! So please stay safe when browsing online with your browser and be mindful of what you are clicking on before opening it up!
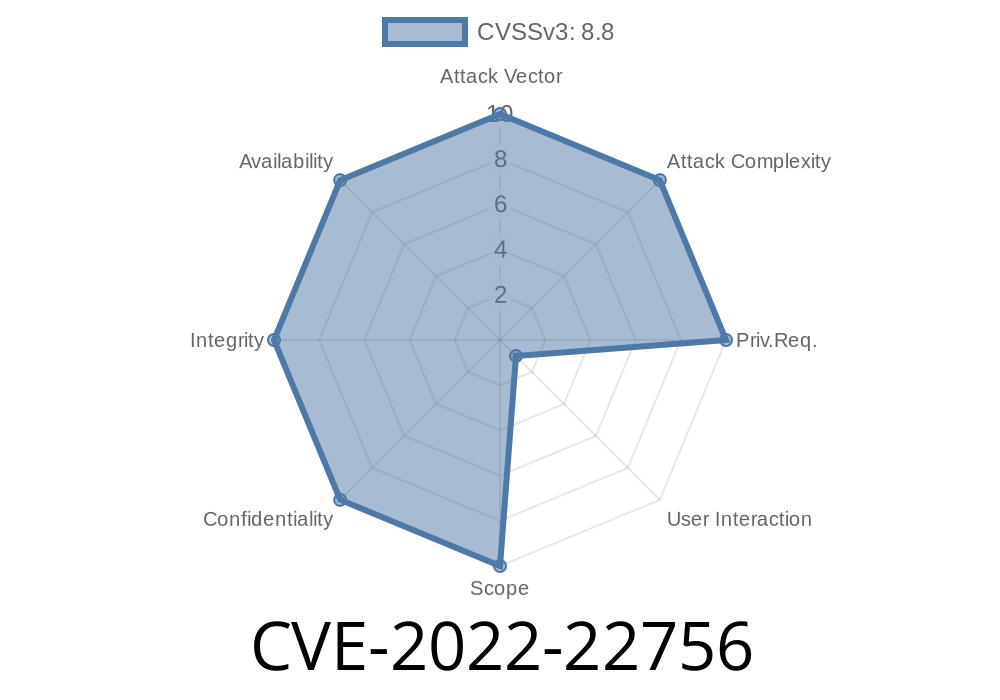
Vulnerability Details
CVE-2022-22756 is a vulnerability in Mozilla Firefox that was first publicly disclosed on October 27th, 2015. The vulnerability allows attackers to bypass the warning prompt when opening an image by dragging it onto the browser window, which then allows malicious JavaScript code to run on the victim’s computer. Mozilla was aware of the issue since late 2015 and issued an advisory with the details. However, the browser’s default setting did not prompt users to click on the image before opening it, which allowed attackers an easier way to convince victims to open malicious files without any warnings from Mozilla.
The importance of digital marketing: 6 reasons why digital marketing is important
1) You can target your ideal audience
2) The ability to target your audience better is one of the most obvious reasons why digital marketing is important.
3) By investing in digital, you will help your business grow
The Issue
Mozilla acknowledged the issue and issued an advisory on July 11th, 2016. Mozilla Firefox has now patched this vulnerability.
Finding malicious links in Google Search
As a result, it is important to be vigilant in monitoring your search results. If you are unsure of what an image link might do, you should prevent the link from opening by right clicking on the image and selecting "Block Image." You can also select "Open image in new tab" if you want to open the image in a separate browser window. Another option is to double-click on the image and input a search term that may be related to the content of the page or the intended malicious outcome of the site. It is important to note that not all images will prompt this behavior and some websites may have their own settings for how they handle drag and drop.
Timeline
Published on: 12/22/2022 20:15:00 UTC
Last modified on: 12/29/2022 23:09:00 UTC