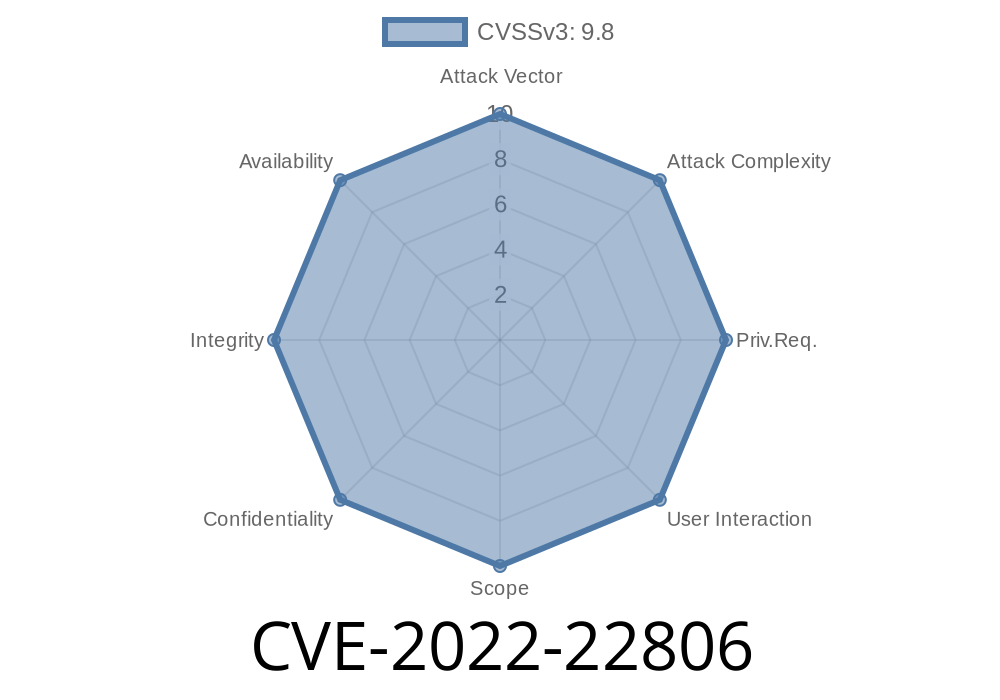
Security Risk: An attacker could send a malformed packet that would be accepted by the UPS. The attacker could then connect to the UPS and perform actions without being authenticated. This may lead to sensitive information being compromised, among other things. Fix/Upgrade recommendation: Customers should upgrade to the latest software version. In addition, users should make sure that their devices are not accepting incoming connections with an IP address outside of their expected range. End-users can change the device’s connected IP address in the router or use a different device for remote management. For software upgrade information, see https://support.citrix.com/article/CTX236287.
Vulnerability Scenario
The vulnerability could be exploited by an attacker who would send a malformed packet to the UPS that is accepted. The attacker could then connect to the server without being authenticated, leading to sensitive information potentially being compromised.
Vulnerabilities and Exposures
The Citrix Connected Pre-Boot Execution Environment (PXE) is designed to be a lightweight, secure, and reliable service that enables computers, which are not connected to a network or cannot boot into a local operating system, to access the network and receive instructions. This document discusses vulnerabilities and exposures in PXE.
Credential Re-use and Insecure Storage
When credentials are stored in the clear, it is easy for attackers to gain access to them. This could lead to a loss of sensitive information such as passwords, certificates, or other sensitive data.
A recent vulnerability allows an attacker to perform actions on servers after receiving a malformed packet from their UPS. This may lead to sensitive information being compromised or the unauthorized modification or deletion of data. End-users that have devices connected with their UPS can mitigate these risks by upgrading software and changing their connected IP address. For software upgrade information, see https://support.citrix.com/article/CTX236287
Vulnerability Description
A vulnerability was recently discovered in Citrix’s remote access management product, XenMobile. A malicious individual could send a malformed packet that would be accepted by the UPS. The attacker could then connect to the UPS and perform actions without being authenticated. This may lead to sensitive information being compromised, among other things.
Timeline
Published on: 03/09/2022 20:15:00 UTC
Last modified on: 05/12/2022 20:42:00 UTC