This vulnerability is currently being exploited in the wild. Due to the critical nature of this issue, we would like to release a security bulletin before the end of the month. An update to the VMware App Control component has been released (version 8.8.2) that resolves this issue. As a best practice, we recommend that customers update their installations as soon as possible. In addition, we also recommend that administrators limit access to the VMware App Control component to only trusted users and limit the frequency of access to the component to only when necessary. Furthermore, we recommend that administrators monitor network traffic for signs of intrusion attempts and take appropriate actions to block the malicious traffic. VMware App Control component can be downloaded from the following URL: https://my.vmware.com/appcontrol/
Vmware vRealize Operations Appliance
VMware vRealize Operations Appliance is a tool that provides central management for all of your applications, infrastructure, and virtual machines. It monitors the health of your business’s private cloud to provide early warning signs and prevent any problems from becoming out-of-control catastrophes.
To ensure that the VMware vRealize Operations Appliance is scalable enough for your organization, it includes a variety of features such as central monitoring and control (MMC) and integrated analytics. MMC can be configured to monitor the health of individual VMs, clusters, and datacenters. Integrated analytics can be used to store performance information in data warehouses in order to gain context around how individual resources work together within your organization.
Vulnerability description
VMware App Control is a deployment platform for mobile application management. VMware App Control can be installed as part of a VMware vCenter Single Sign-On (SSO) installation or on its own within a vSphere environment. An issue was identified in the handling of the /api/login endpoint which may allow an attacker to impersonate the administrator of the VMware App Control system with the rights to deploy, uninstall, update, and view apps.
Vulnerability Description
VMware App Control is a free VMware product that provides an application-focused web interface that allows IT administrators to manage and control endpoint devices with the VMware Horizon View or VMware Horizon Server desktop virtualization products. The vulnerability exists due to insufficient validation of user input to determine if a specific string is present in the URL. An attacker can exploit this issue by registering a new device on the App Control portal, submitting the malicious input, and access all endpoint devices registered on the portal.
Vulnerability Details
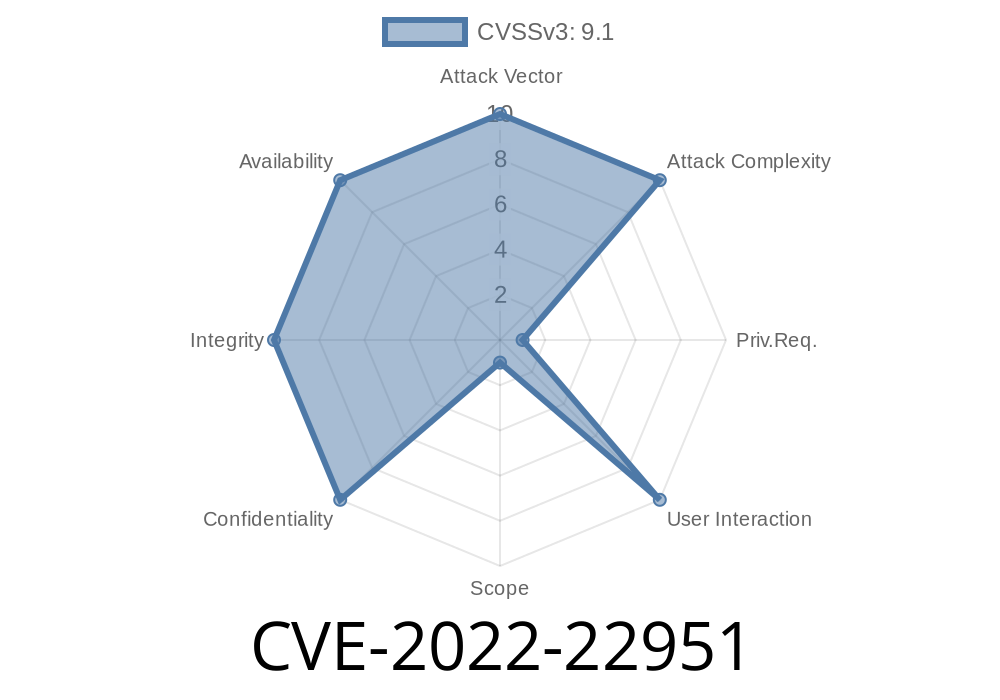
The VMware App Control component has been recently reported to be vulnerable to CVE-2022-22951. Due to the critical nature of this issue, we would like to release a security bulletin before the end of the month. An update to the VMware App Control component has been released (version 8.8.2) that resolves this issue. As a best practice, we recommend that customers update their installations as soon as possible. In addition, we also recommend that administrators limit access to the VMware App Control component to only trusted users and limit the frequency of access to the component to only when necessary. Furthermore, we recommend that administrators monitor network traffic for signs of intrusion attempts and take appropriate actions to block the malicious traffic
Timeline
Published on: 03/23/2022 20:15:00 UTC
Last modified on: 03/29/2022 18:07:00 UTC