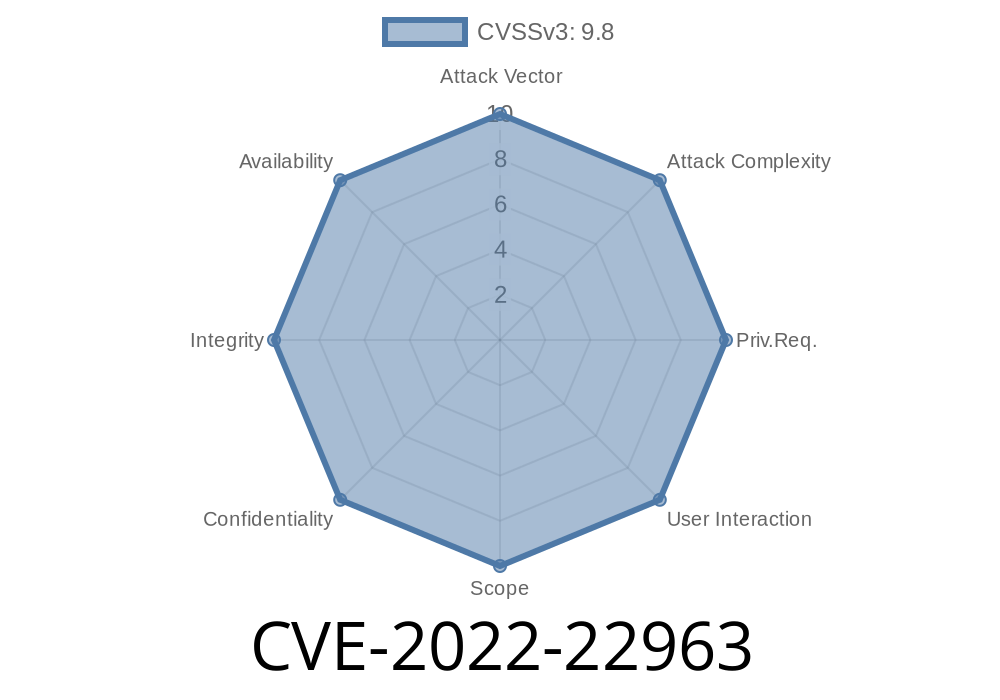
The SpEL is validated using the regular expression matching rules and malicious expressions are rejected by the validator. However, due to the fact that the validator can only check the syntax of the expression and not the intent, it is possible to craft expressions that look correct but are malicious in nature. The SpEL can be constructed in multiple ways and the most common way is to use the JSONPath syntax to access a property on an object that does not exist. In the example below, the user may be accessing a non-existent property on the object and as a result, an unauthorized remote code execution may occur. custom-route condition = " notjohn.example_service " > ! — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — —
JSONPath Condition
The JSONPath condition is formed by prepending " ! " to the property name, followed by a question mark. This is commonly seen in the form of ?x.
In the example below, the user may be accessing a non-existent property on the object and as a result, an unauthorized remote code execution may occur. custom-route condition = " notjohn.example_service " > ! — — — — — — — — — — — — — -?javax.web.server.dispatchor=?
!javax . web . server . dispatchor ?"
!javax . web . server . dispatchor ?"
"javax . web . server . dispatchor="
JSONPath Syntax
JSONPath is a JavaScript abstraction for accessing the properties of an object. It is possible to construct malicious expressions using the JSONPath syntax as it can be constructed in multiple ways. In the example below, the user may be accessing a non-existent property on the object and as a result, an unauthorized remote code execution may occur. " custom-route " if (custom-route) then { " custom-route " ; :" notjohn.example_service " };
! — — — — — — — — — — — — – !!! !!!! !!!
The SpEL can be constructed in multiple ways and the most common way is to use the JSONPath syntax to access a property on an object that does not exist. The example below shows how this may be done:
"custom-route" if (custom-route) then { "custom-route": "notjohn.example_service"; }
Alerting on invalid condition
As a result of the SpEL validation, an invalid condition is raised when an expression is constructed with an invalid property path.
There are multiple ways to construct expressions and the most common way is to use the JSONPath syntax to access a property on an object that does not exist. The example below shows a valid JSONPath expression:
custom-route condition = " notjohn.example_service " > ! — — — — — — — — — — !!!! !!! !!!! !!! !! !! !! !! !!!! !!!!! !!! !!! !!!!!!!!!!
In this expression, the first two colons are used to denote that it is using JSONPath syntax. However, due to the fact that the validator can only check the syntax of the expression and not its intent, it is possible to craft expressions that look correct but are malicious in nature. In fact, there are multiple ways to construct expressions where an invalid property path may be reached such as:
Timeline
Published on: 04/01/2022 23:15:00 UTC
Last modified on: 07/28/2022 18:26:00 UTC
References
- https://tanzu.vmware.com/security/cve-2022-22963
- https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-java-spring-scf-rce-DQrHhJxH
- https://psirt.global.sonicwall.com/vuln-detail/SNWLID-2022-0005
- https://www.oracle.com/security-alerts/cpuapr2022.html
- https://www.oracle.com/security-alerts/cpujul2022.html
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-22963