SaltStack recommends upgrading to this latest release or contacting support. A fix has been applied in version 3.0.2 and earlier releases.
A bug was discovered in SaltStack Salt in versions before 3004.4. If a malicious actor were to modify the contents of a dictionary file, it would cause an unhandled exception resulting in a Denial of Service. This affects both local shell accounts with an active session and salt-api users that authenticate via PAM eauth. SaltStack recommends upgrading to this latest release or contacting support. A fix has been applied in version 3.0.4 and earlier releases.
A bug was discovered in SaltStack Salt in versions before 3004.7. A malicious actor could cause an unhandled exception via a specially crafted Salt file. This affects both local shell accounts with an active session and salt-api users that authenticate via PAM eauth. SaltStack recommends upgrading to this latest release or contacting support. A fix has been applied in version 3.0.5 and earlier releases. A bug was discovered in SaltStack Salt in versions before 3005.x. A malicious actor could create a malicious configuration file that would cause an unhandled exception when it is loaded into Salt. This affects both local shell accounts with an active session and salt-api users that authenticate via PAM eauth. SaltStack recommends upgrading to this latest release or contacting support. A fix has been applied in version 3.0.6 and earlier
What is SaltStack?
SaltStack is a configuration management tool for Linux. It provides a mechanism for controlling the execution and deployment of large numbers of software packages on multiple systems. SaltStack can also manage configuration data, as well as orchestrate ad-hoc jobs across multiple servers and clouds. SaltStack is a scalable solution that can be used to provide visibility into the state of an infrastructure, control access to resources, automate repetitive tasks, and build high availability systems
Timeline
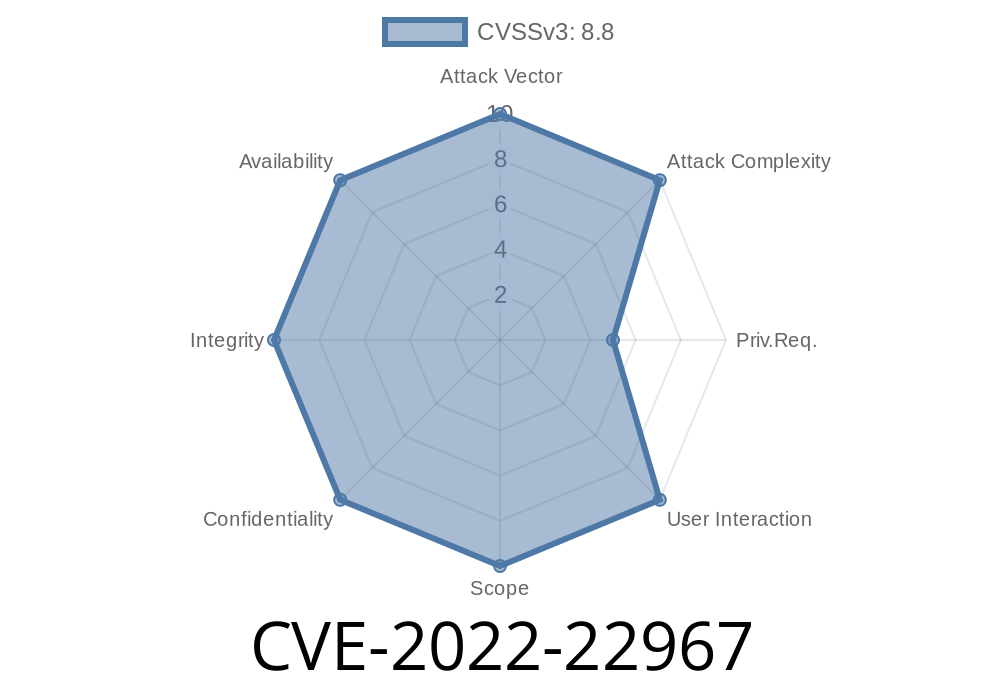
Published on: 06/23/2022 17:15:00 UTC
Last modified on: 06/30/2022 19:24:00 UTC