Access and Identity Manager is a centralized management and policy-enforcement engine for user access management and identity. The product can be used in a variety of use cases, including Internet-facing applications, remote and branch office applications, and mobile applications. Access and Identity Manager also offers support for single sign-on, and federated identity providers. ESXi hosts and virtual machines are managed by Access and Identity Manager. This makes it possible for a malicious actor to gain 'root' access on ESXi hosts and virtual machines.
Vulnerability Details
Despite reaching a high level of maturity in the market, this product still contains a vulnerability that allows for root access to ESXi hosts and virtual machines. This vulnerability is due to the fact that Access and Identity Manager does not sufficiently sanitize user input when issuing API calls. Attackers are able to obtain 'root' access on ESXi hosts and virtual machines by using a malicious API call. The vulnerability exists in the following API:
GetInstancesFromCluster
If an attacker provides invalid input in this API call, then Access and Identity Manager may return the following error message:
HTTP/1.1 400 Bad Request
The origin of this error is not known; however, it appears as though some type of validation has been performed against the input provided by the attacker. This makes it difficult to identify exactly how an attacker gains access to admin-level privileges on ESXi hosts and virtual machines. As there is no known mitigation of this vulnerability, it would be appropriate for Access and Identity Manager to release a patch or mitigate the vulnerability soon.
Vulnerability Overview
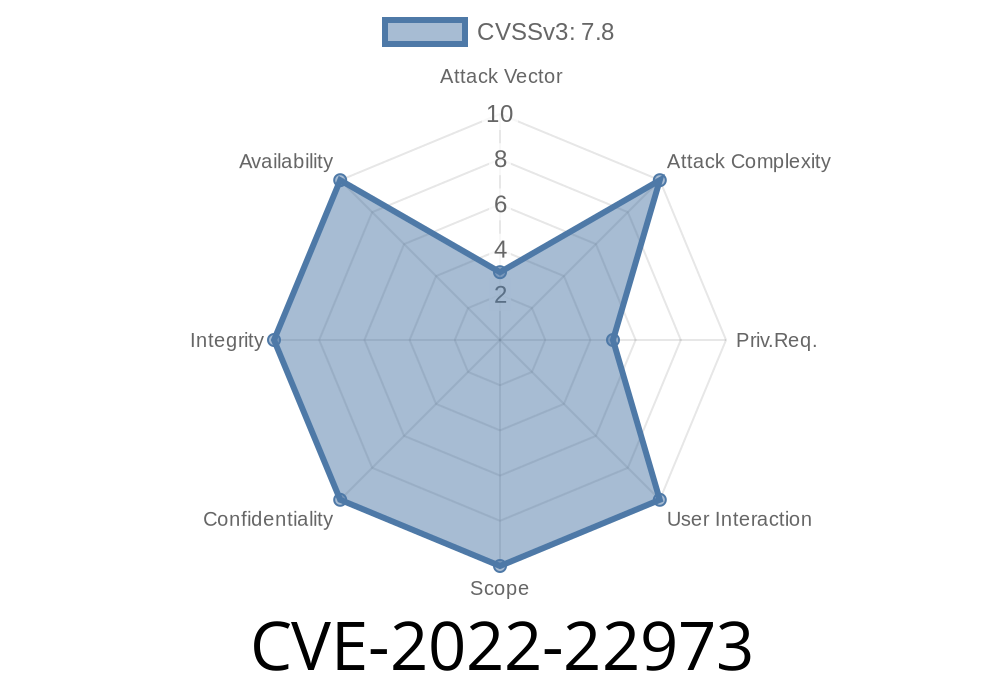
A newly discovered vulnerability, CVE-2022-22973, affects Access and Identity Manager. The vulnerability was found on the Default Web Interface of Access and Identity Manager. The vulnerability makes it possible for a malicious actor to gain 'root' access on ESXi hosts and virtual machines, which would enable them to make changes to core operating system files or inject malicious code into the host.
The vulnerability allows an attacker with direct or local physical access to the server running Access and Identity Manager to view the contents of a file that is being served by the web interface. If this file contains an unencrypted form of sensitive data, such as credentials or malware payloads, it can be stolen by an attacker if they can access and modify it. An attacker with remote access could also exploit this vulnerability in order to read sensitive data from the server that is stored in memory or on disk. This may allow a potential attacker to read password hashes, key information used for cryptography operations, cryptographic keys used for authentication purposes, or configuration settings required for authentication with other systems.
Vulnerability Description
A vulnerability in ESXi hosts and virtual machines running on them is described. The vulnerability allows malicious actors to gain 'root' access on ESXi hosts and virtual machines via a local exploit.
Vulnerability overview
The Access and Identity Manager is a product that provides centralized management and policy-enforcement for user access and identity. The product can be used in a variety of use cases, including Internet-facing applications, remote and branch office applications, and mobile applications. Access and Identity Manager also offers support for single sign-on, and federated identity providers. Several ESXi hosts and virtual machines are managed by the product.
A security vulnerability was discovered on ESXi hosts managed by the Access and Identity Manager product. The vulnerability could allow malicious actors to gain 'root' access on these hosts. This would make it possible for these malicious actors to execute arbitrary binary code on the host without being detected.
Vulnerability Summary
Vulnerability Summary:
Possibility of malicious actors gaining 'root' access on ESXi hosts and virtual machines.
Vendor Response:
VMware is working with their customers to release a patch.
Timeline
Published on: 05/20/2022 21:15:00 UTC
Last modified on: 05/27/2022 17:48:00 UTC