Published: Official NVD entry
Introduction
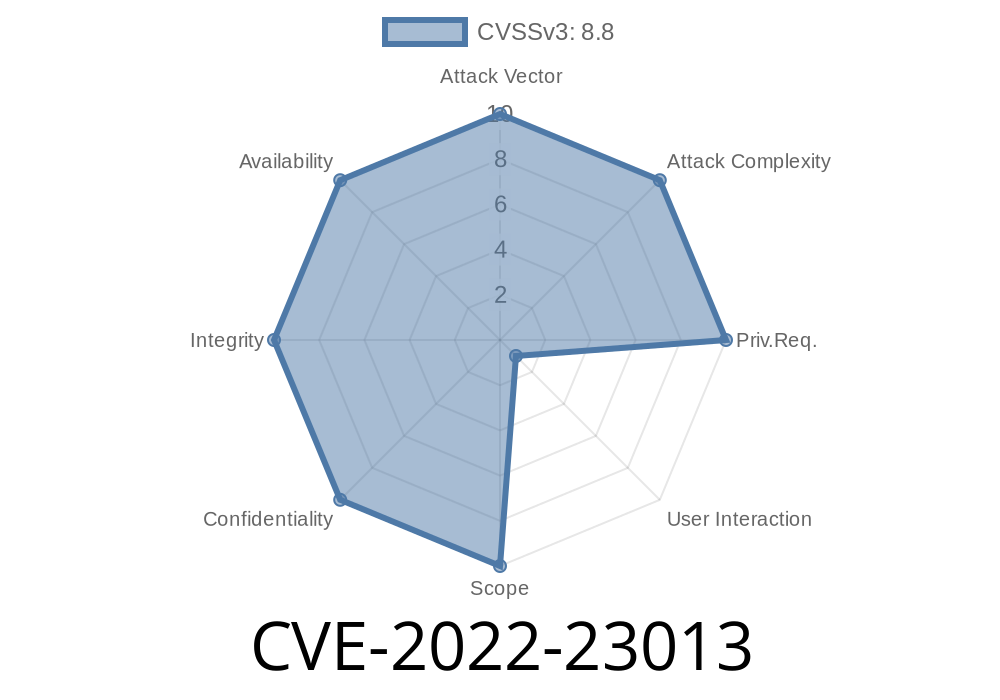
A dangerous vulnerability, CVE-2022-23013, was discovered in BIG-IP DNS & GTM systems. This bug is a DOM-based cross-site scripting (XSS) flaw found in the Configuration utility—F5’s management interface—to administrate BIG-IP devices. Successful exploitation might allow bad actors to execute arbitrary JavaScript with the permissions of the currently logged-in admin. This basically means stealing your session or running commands as you if you’re the admin logged in.
ALL versions of 13.1.x, 12.1.x, 11.6.x
*Note: Out-of-support versions are untested but likely vulnerable!*
Understanding the Vulnerability
The issue lies in a "DOM-based" XSS bug. Here, the JavaScript in the management page uses unsanitized data from the browser’s URL or state, makes unsafe DOM changes, or directly executes data with eval() or other JavaScript APIs, leading to JavaScript code running in your session without your consent.
A DOM-based XSS has the following basic flow
1. The attacker crafts a malicious URL with some JavaScript payload hidden in a query parameter, hash (#fragment), or other URL-controlled element.
2. The victim (an admin) is tricked into visiting this URL (via phishing, support tickets, internal chat, etc.)
3. When the page loads, embedded JavaScript code improperly trusts and uses the attacker’s data—making it part of the document, or executing it.
4. The attacker’s JavaScript runs as if it’s from the BIG-IP interface, letting them control the session: hijacking cookies, performing actions as the victim, or escalating privileges.
How Attackers Exploit CVE-2022-23013
While the exact vulnerable page isn’t publicly disclosed by F5, the pattern of the attack is well-known for DOM XSS. Let’s walk through a hypothetical attack scenario, including a code snippet demonstrating the kind of bug at play.
Attack Scenario
- The attacker knows the BIG-IP management portal is running on https://bigip.example.com.
They send an email to an admin, saying:
“Hey, we’ve detected a DNS issue, please log in to the management panel through this link so our script can debug:
https://bigip.example.com/tmui/login.jsp#debug=<payload>”
The link contains a malicious payload in the hash fragment (after #).
- When the admin logs in, the vulnerable script on the Configuration utility page processes the hash and inserts it into the DOM without filtering, or worse, executes it.
Here’s a simplified version of what might happen in the vulnerable application
// BAD PRACTICE - vulnerable to DOM XSS
let debugParam = window.location.hash.substring(1); // gets 'debug=<payload>'
document.getElementById('output').innerHTML = debugParam; // unsafe
If the attacker uses this payload:
#debug=<img+src=x+onerror=alert('XSS')>
It will display an image on the page, but since the source x isn’t a real image, the browser will run the onerror JavaScript -- showing an XSS popup or, in real attacks, running data-stealing code.
Worse yet – sometimes the JS evaluates the parameter
// EXTREMELY DANGEROUS
eval(window.location.hash.substring(1));
If the attacker sends:
#alert(document.cookie)//
The admin’s browser will show a popup with their session token, but an attacker can grab it instead.
Social engineering: Sending links to admins via official-looking emails.
- Internal pivoting: If an attacker phishes a low-privileged user, they can lure admins to the link.
2. Visit this URL (on your own test appliance)
https://<your-bigip-address>/tmui/login.jsp#<img src=x onerror="alert('XSS via CVE-2022-23013')">
References & Further Reading
- CVE-2022-23013 NVD Entry
- F5 Security Advisory K000130166
- OWASP DOM-based XSS explanation
- DOM XSS Cheat Sheet
Final Thoughts
CVE-2022-23013 is a classic example of why web interfaces in sensitive appliances must sanitize all user input, especially anything used in JavaScript. If you’re running an affected BIG-IP version, update immediately, and don’t ever expose your management interface to the public internet.
Have questions or need help patching? See the official F5 advisory.
Timeline
Published on: 01/25/2022 20:15:00 UTC
Last modified on: 02/02/2022 18:43:00 UTC