This vulnerability is classified as CVSS 3.0 because it can be exploited via a remote unauthenticated attack.
The ClusterON command "dsync" (Distributed SnapShottable ONTAP Data Sync) is vulnerable to a denial of service (DoS) attack where an attacker can cause excessive amounts of data to be written to the cluster. This results in the cluster running out of space and causing the dsync command to fail.
The ClusterON command "dsync" (Distributed SnapShottable ONTAP Data Sync) is vulnerable to a denial of service (DoS) attack where an attacker can cause excessive amounts of data to be written to the cluster. This results in the cluster running out of space and causing the dsync command to fail. ClusterON command "dsync" (Distributed SnapShottable ONTAP Data Sync) is vulnerable to a denial of service (DoS) attack where an attacker can cause excessive amounts of data to be written to the cluster. This results in the cluster running out of space and causing the dsync command to fail. ClusterON command "dsync" (Distributed SnapShottable ONTAP Data Sync) is vulnerable to a denial of service (DoS) attack where an attacker can cause excessive amounts of data to be written to the cluster. This results in the cluster running out of space and causing the dsync command to fail. ClusterON command "dsync" (Distributed SnapShott
CVSS Vulnerability Summary
Vulnerability Type: CVSS 3.0
CVSS Base Score: 8.6
CVSS Temporal Score: 7.8
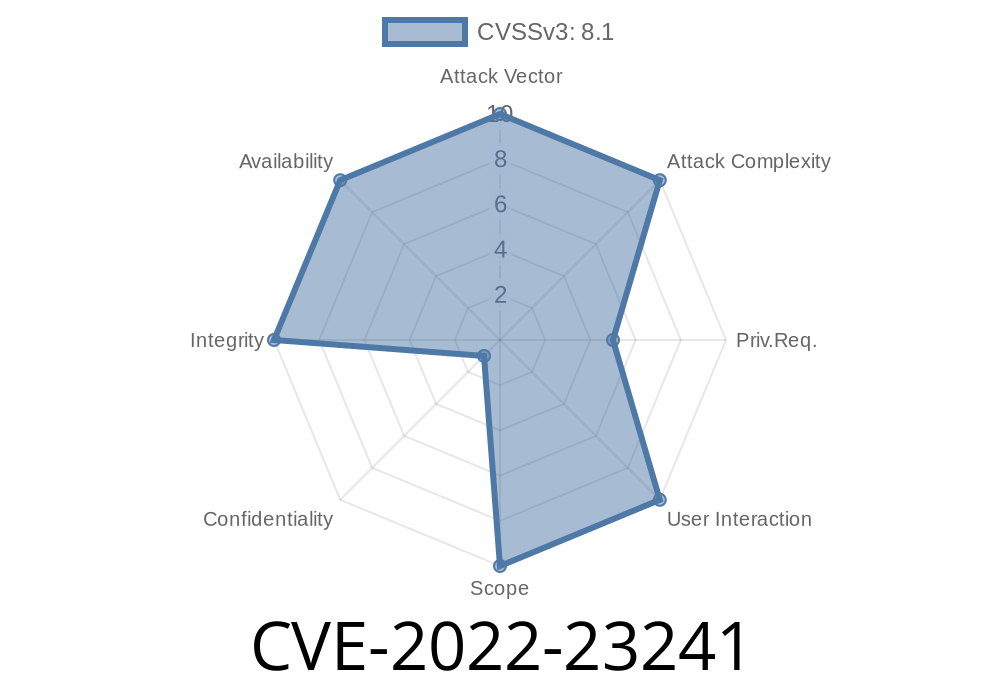
CVE ID: CVE-2022-23241
Timeline
Published on: 10/19/2022 18:15:00 UTC
Last modified on: 10/21/2022 16:39:00 UTC