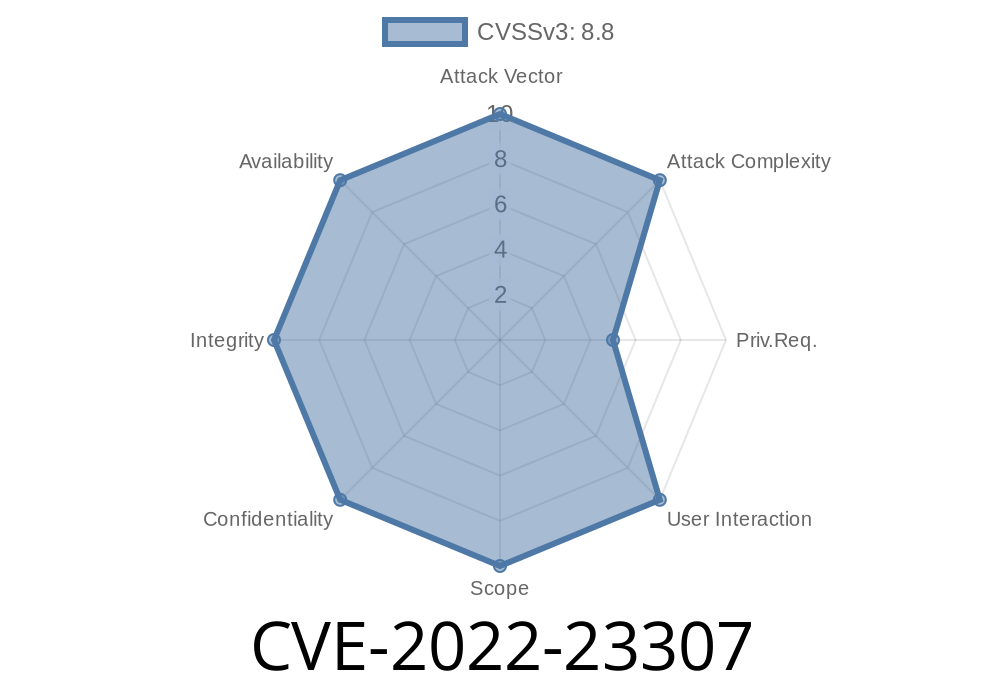
If you work with logs in Java, you've probably come across tools like Apache Chainsaw or libraries like Log4j. But what happens when these tools themselves have security flaws? In this post, we’ll take a closer look at CVE-2022-23307—a serious deserialization vulnerability in Apache Chainsaw that traces back to the heart of Log4j 1.2.x.
Overview
CVE-2022-23307 is a vulnerability rooted in how Apache Chainsaw (and Log4j 1.2.x) handled serialized Java objects, leaving systems open to remote code execution (RCE) and other attacks.
CVE-202-9493 previously revealed a similar deserialization flaw in Apache Chainsaw. What’s scary is that before Chainsaw became a standalone project (V2.+), it was bundled with Log4j 1.2.x—meaning the same weakness exists in any project still using those old Log4j versions!
What Is Deserialization, and Why Is It Dangerous?
Serialization in Java means converting an object into a byte stream, usually for storing or sending over a network. Deserialization is the reverse process—restoring the byte stream back into an object.
Problem: If user-controlled data is deserialized without proper checks, attackers can craft malicious objects. When the vulnerable tool deserializes those, it might run arbitrary code—effectively giving the hacker the keys to the kingdom.
Where's the Problem in Apache Chainsaw?
Apache Chainsaw had a feature that let users open and process log files over a network. It used Java object deserialization with little to no input validation.
Simple Example
ObjectInputStream ois = new ObjectInputStream(socket.getInputStream());
Object logEvent = ois.readObject(); // Dangerous if attacker sends crafted data
If your software is still running Log4j 1.2.x’s Chainsaw classes (often chained as part of a logging setup), it's exposed to this risk.
Example Exploit Using Ysoserial
Researchers and attackers often use the Ysoserial tool to create malicious payloads. Here’s how an attacker might leverage it:
`
If the server is listening for remote log events and uses vulnerable deserialization code, this simple attack triggers the payload.
Official CVE entries:
- CVE-2022-23307
- CVE-202-9493
- Apache Log4j Security Page
- Ysoserial Payload Generator
- Chainsaw Project
- Checkmarx Blog: Deserialization Vulnerabilities in Chainsaw
How to Fix & Mitigate
- Upgrade to Chainsaw v2.+ and/or Log4j 2.x
Disable all remote logging features if you don’t absolutely need them
If you’re stuck with older Log4j:
Final Thoughts
Deserialization flaws can lurk in the tools we trust most. CVE-2022-23307 shows that relying on outdated versions of Java tools (like Log4j 1.2.x and Chainsaw) is a recipe for disaster. Upgrading now is the only safe bet.
Stay vigilant. Patch early. Never trust serialized input without validation.
Timeline
Published on: 01/18/2022 16:15:00 UTC
Last modified on: 07/25/2022 18:21:00 UTC