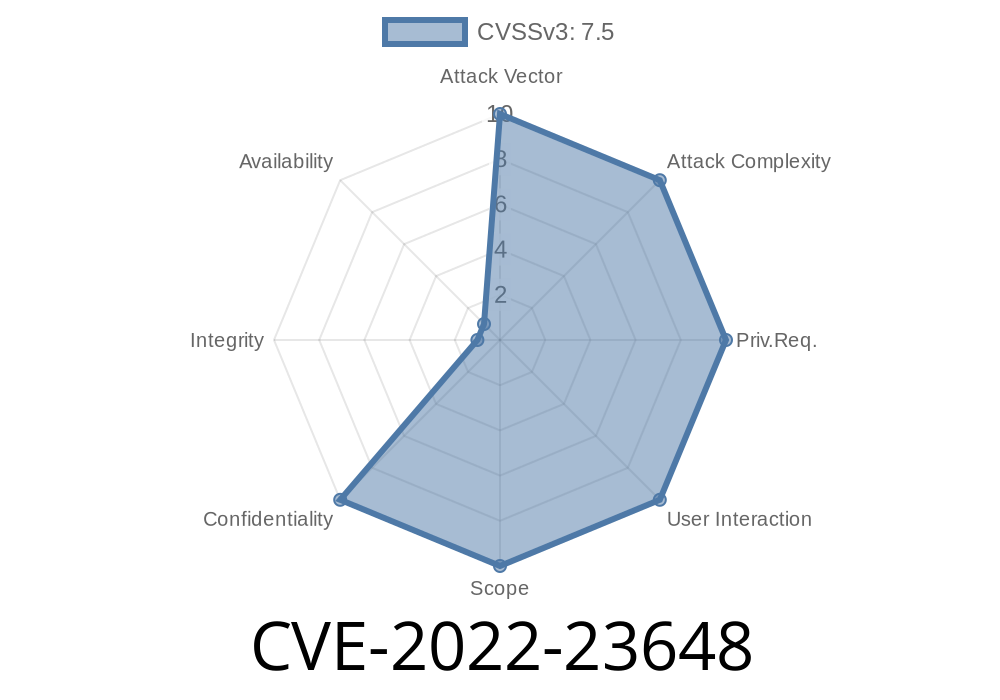
Additionally, containerd versions prior to 1.5.10 have been found to be vulnerable to a denial of service due to a NULL-pointer dereference when a small number of simultaneous connections are received. This can be mitigated by lowering the rate at which connections are processed. A mitigations for containerd users has been released and can be found here.
Container Runtime Interface A bug was discovered in the CRI implementation of containerd prior to versions 1.6.1, 1.5.10, and 1.4.12 where a malicious container could gain access to read-only copies of arbitrary files and directories on the host operating system. This may bypass any policy-based enforcement on container setup (including a Kubernetes Pod Security Policy) and expose potentially sensitive information. Kubernetes and crictl can both be configured to use containerd’s CRI implementation. This bug has been fixed in containerd 1.6.1, 1.5.10, and 1.4.12. Users should update to these versions to resolve the issue. Additionally, containerd versions prior to 1.5.10 have been found to be vulnerable to a denial of service due to a NULL-pointer dereference when a small number of simultaneous connections are received. This can be mitigated by lowering the rate at which connections are processed. A mitigations for containerd users has been released and can be found here.
Container Runtime Interface (CRI)
In this article, the authors talk about an issue with the Container Runtime Interface (CRI) implementation of containerd. In short, a bug was discovered in the CRI implementation of containerd prior to versions 1.6.1, 1.5.10, and 1.4.12 where a malicious container could gain access to read-only copies of arbitrary files and directories on the host operating system. This bug has been fixed in containerd 1.6.1, 1.5.10, and 1.4.12 and users should update to these versions to resolve the issue or risk having their data exposed by malicious containers running on their Kubernetes clusters or crictl configurations that use pre-v1.6 version of containerd
Timeline
Published on: 03/03/2022 14:15:00 UTC
Last modified on: 04/25/2022 19:21:00 UTC
References
- https://github.com/containerd/containerd/security/advisories/GHSA-crp2-qrr5-8pq7
- https://github.com/containerd/containerd/releases/tag/v1.4.13
- https://github.com/containerd/containerd/releases/tag/v1.6.1
- https://github.com/containerd/containerd/releases/tag/v1.5.10
- https://github.com/containerd/containerd/commit/10f428dac7cec44c864e1b830a4623af27a9fc70
- https://www.debian.org/security/2022/dsa-5091
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/OCCARJ6FU4MWBTXHZNMS7NELPDBIX2VO/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/AUDQUQBZJGBWJPMRVB6QCCCRF7O3O4PA/
- http://packetstormsecurity.com/files/166421/containerd-Image-Volume-Insecure-Handling.html
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/HFTS2EF3S7HNYSNZSEJZIJHPRU7OPUV3/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-23648