An attacker could potentially leverage this issue to read, write, or delete sensitive data, and/or may be able to access privileged PingID API endpoints. In order to correct this issue, an IT administrator must remove or replace these administrator privileged credentials with non-privileged credentials. For example, an administrator could modify PingID Windows Login user endpoints to use a delegated, non-admin administrator account.
Mitigation Strategies
The following mitigation strategies will help reduce the risk of exploitation of this vulnerability:
1. Restrict access to PingID administrative APIs and endpoints using an organization-wide or individual account privilege management policy that includes revoking access from any user, such as an administrator, who does not require these privileges for business needs.
2. Enable password complexity requirements for administrative accounts, such as requiring at least 8 symbols and one upper-case character in passwords.
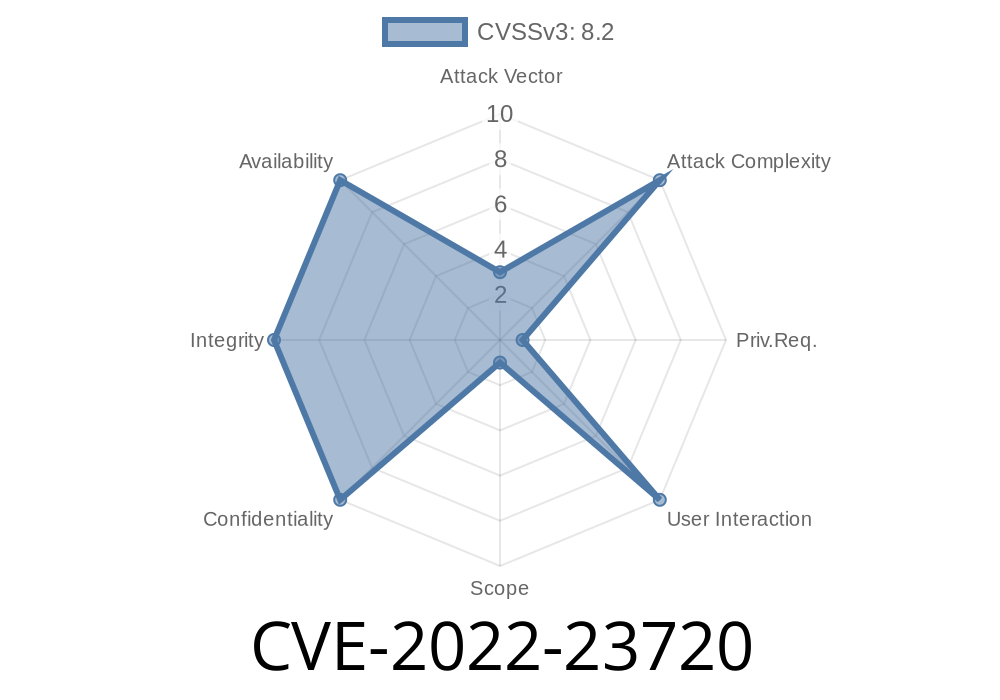
Vulnerability Description
A vulnerability was found in the PingID Windows Login application that allows users to authenticate with their administrator privileged credentials. If exploited, an attacker could potentially read, write, or delete sensitive data, and/or may be able to access privileged PingID API endpoints.
The issue could be corrected by removing or replacing the administrator privileged credentials with non-privileged credentials. For example, the user should change their password to a delegated non-admin account.
Vulnerability overview
A vulnerability in PingID Windows Login allows attackers to gain administrator privileges with a single login. By leveraging this issue, an attacker could read, write, or delete sensitive data and/or may be able to access privileged PingID API endpoints.
To correct this issue, IT administrators must remove or replace these administrator privileged credentials with non-privileged credentials. For example, an administrator could modify PingID Windows Login user endpoints to use a delegated, non-admin administrator account.
Vulnerability Description - CVE-2022-23721
If an attacker is able to find a way to send a POST request along with their username and password, they could potentially create a malicious account.
In order to correct this issue, an IT administrator must replace the privileged PingID API endpoint with the non-privileged PingID API endpoint.
Timeline
Published on: 06/30/2022 20:15:00 UTC
Last modified on: 07/13/2022 17:13:00 UTC