When accessing a malicious website or opening a malicious file, the user’s browser sends the request to the Internet server. The server receives the request, identifies that the request is from a Windows system and processes it accordingly. The server then takes the request and sends it to the web application on the Windows system where it is then processed. The web application then takes that request and sends it to the Windows application where it is then processed.
Vulnerability Overview
The vulnerability allows an attacker to execute arbitrary code on the victim's Windows system by sending a specially crafted request to a malicious website or file. The vulnerability is caused due to the way that browsers perform authentication requests to Internet servers and how the server handles them.
Although not yet confirmed, there are reports of this vulnerability being exploited in the wild.
Alert: Microsoft Office 365 Remote Code Execution Vulnerability
A vulnerability in Microsoft Office 365 has been identified that could allow remote code execution. This vulnerability is related to the way Windows handles requests from browsers and affects all versions of Microsoft Office 365 including Office 365 Home, Personal, and University editions.
A flaw in the way Windows processes HTTP requests from a user’s browser has been identified which could allow for a remote code execution exploit. The flaw exists due to how Windows manages how it handles requests from browsers and affects all versions of Microsoft Office 365 including Office 365 Home, Personal, and University editions.
The vulnerability allows an attacker to send specially crafted HTTP request that would cause the affected system to execute arbitrary code on behalf of the logged-in user when opening or navigating to a malicious website or opening a malicious file.
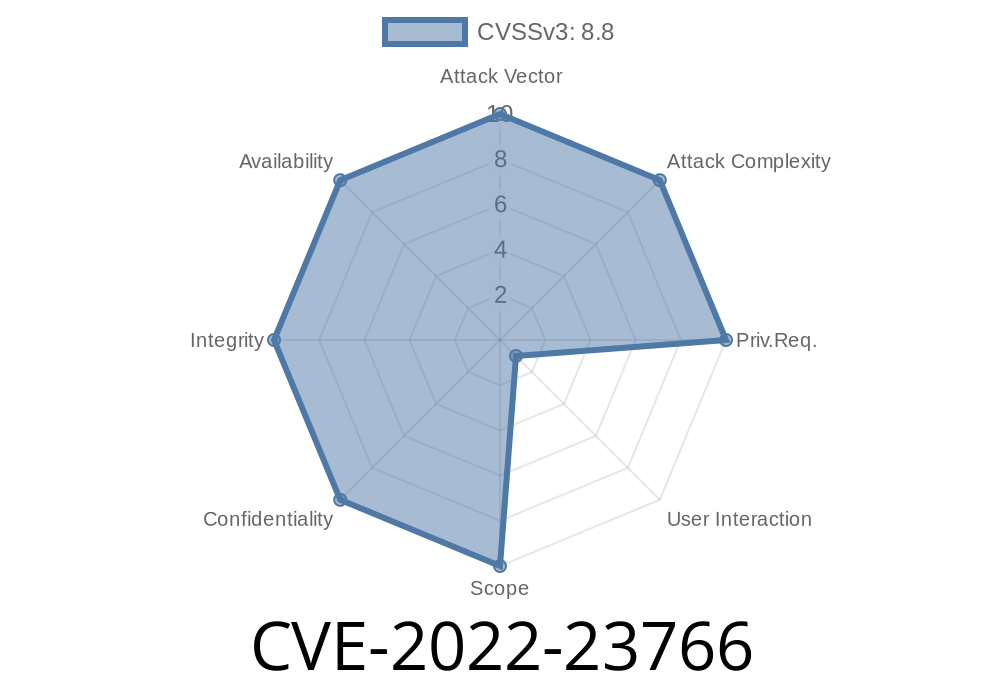
CVE-2023-23767
It is caused by a buffer overflow in the Windows Kernel. This vulnerability affects the Windows operating system via Microsoft Internet Explorer, Microsoft Edge, Microsoft Office and other affected software.
This vulnerability is caused when an application fails to properly handle a specially crafted image file that causes a buffer overflow. The attacker can make the process crash by sending an image with a carefully crafted size, which then causes code execution. When this happens, it corrupts system memory and allows for remote code execution on the computer.
The security concerns of this vulnerability are high as it can easily allow any individual to take control of a machine remotely. The exploit could allow an attacker to take control of an infected machine and run software that they have never allowed on there computer before or even download spyware onto the machine without their knowledge.
Vulnerability overview
This vulnerability affects the way that Microsoft’s web browser handles requests. This vulnerability was identified in Microsoft Edge and Internet Explorer versions 10 through 11, and is present in all Windows systems running those versions of the browser. An attacker could exploit this vulnerability by persuading a user to visit a malicious website or opening a malicious file on their system.
The vulnerability is an elevation of privilege vulnerability that could allow the attacker to take control of the system with administrator privileges.
Windows Defined
Windows is a family of graphical operating systems developed, marketed, and sold by Microsoft. It is the best-selling platform for personal computers worldwide.
The Windows family consists of multiple platforms, ranging from mobile devices to desktops. A key component of Windows is the Windows kernel, which acts as the central processing unit (CPU) of the system and allows applications to run on it. The most common variant of Windows by far is Windows 10 which has been rolled out to most users on PCs and laptops since mid-2015.
Timeline
Published on: 09/19/2022 20:15:00 UTC
Last modified on: 09/21/2022 16:28:00 UTC