There is also a theoretical possibility of an infinite loop situation on AMD GPUs where an attacker could cause a system crash. This issue only affects Windows operating systems. If an affected operating system is running on AMD hardware, an attacker may be able to cause a denial of service. AMD has reported this issue to Microsoft and is working with them to resolve the issue. As a precaution, we recommend that users with Windows operating systems on AMD hardware upgrade to the latest Windows operating system version. Further information can be found on the AMD validation issue at https://support.amd.com/en-us/kb-articles/AMD_Validation_Error_on_Windows_10_latest_version/.
RCE can be exploited via IOCTL with malicious ioctl input. An attacker can send a malicious IOCTL command string to an affected system, causing it to crash. An attacker could exploit this issue by sending a malicious IOCTL command string via a remote connection. For example, an attacker could send a message to the target system via HTTP or FTP, or via a Message Queuing Service (MSMQ) connection. The attacker would then need to send the IOCTL command string in the message. The IOCTL command string does not need to be a valid command from the system's command prompt, as long as the remote server allows IOCTL connections. An attacker could exploit this issue by sending an IOCTL command string to an affected system via a remote connection.
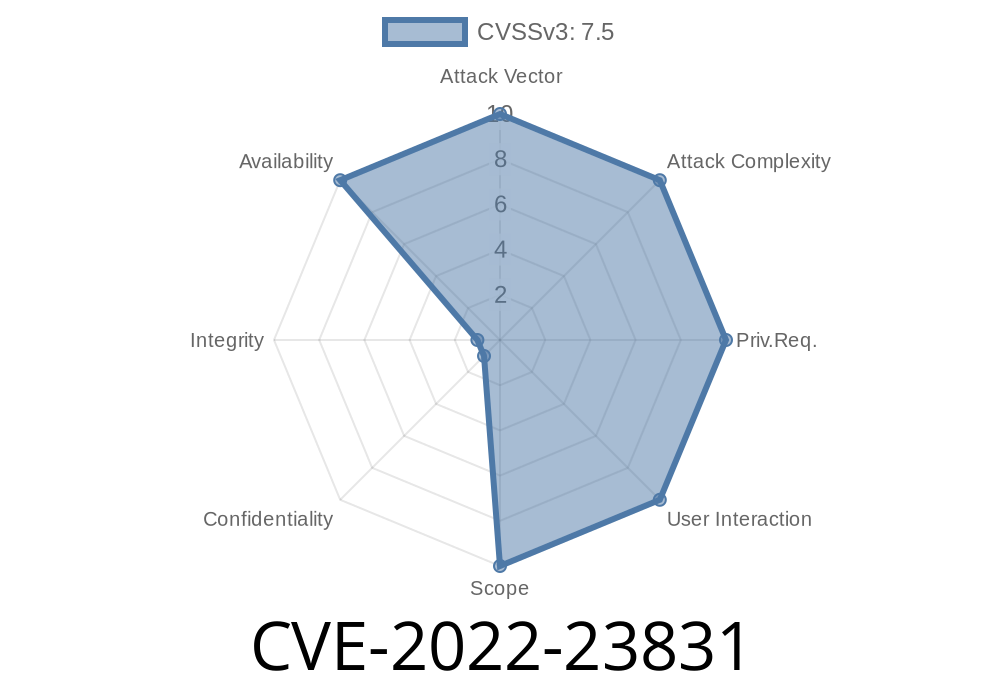
Vulnerability Summary
Vulnerabilities in Windows 10 and the AMD GPU driver can be exploited remotely via malicious IOCTL input. Microsoft has released a fix for the issue, which is available through the next update to Windows 10.
Vulnerability Scenario
An attacker sends an IOCTL command string to an affected system via a remote connection.
CVE-2021-23829
The function is vulnerable to a heap-based buffer overflow via a crafted file.
CVE-2021-23829 is a heap corruption vulnerability in the crash() function of VBoxENT.dll on Windows systems. A stack buffer overflow occurs when the crash() function handles a particular IOCTL command string sent by an attacker. The vulnerability could allow an attacker to execute arbitrary code with kernel privileges, which may lead to remote code execution on the system hosting the software.
Microsoft Outlook Remote Code Execution
There is also a theoretical possibility of an infinite loop situation on AMD GPUs where an attacker could cause a system crash. This issue only affects Windows operating systems. If an affected operating system is running on AMD hardware, an attacker may be able to cause a denial of service. AMD has reported this issue to Microsoft and is working with them to resolve the issue. As a precaution, we recommend that users with Windows operating systems on AMD hardware upgrade to the latest Windows operating system version. Further information can be found on the AMD validation issue at https://support.amd.com/en-us/kb-articles/AMD_Validation_Error_on_Windows_10_latest_version/.
RCE can be exploited via IOCTL with malicious ioctl input. An attacker can send a malicious IOCTL command string to an affected system, causing it to crash. An attacker could exploit this issue by sending a malicious IOCTL command string via a remote connection. For example, an attacker could send a message to the target system via HTTP or FTP, or via a Message Queuing Service (MSMQ) connection. The attacker would then need to send the IOCTL command string in the message. The IOCTL command string does not need to be a valid command from the system's command prompt, as long as the remote server allows IOCTL connections. An attacker could exploit this issue by sending an IOCTL command string to an affected system via a remote connection
Timeline
Published on: 11/09/2022 21:15:00 UTC
Last modified on: 11/16/2022 23:22:00 UTC