Due to the above mentioned QProcess API misunderstanding, the plugin will end up trying to run the LSP server binary located in the directory of the plugin itself, which is an untrusted directory. Due to this, the plugin will try to execute the server binary located in the directory of the plugin itself, which is an untrusted directory. This could lead to remote code execution as the plugin can run arbitrary code when opening a file of a given type. An example of this would be opening an image file and then trying to run the code that opens that image file. Code execution in such a scenario could lead to the installation of malware on the system.
To work around this issue, it is recommended to either move the LSP server binary to a trusted directory or to disable the LSP plugin.
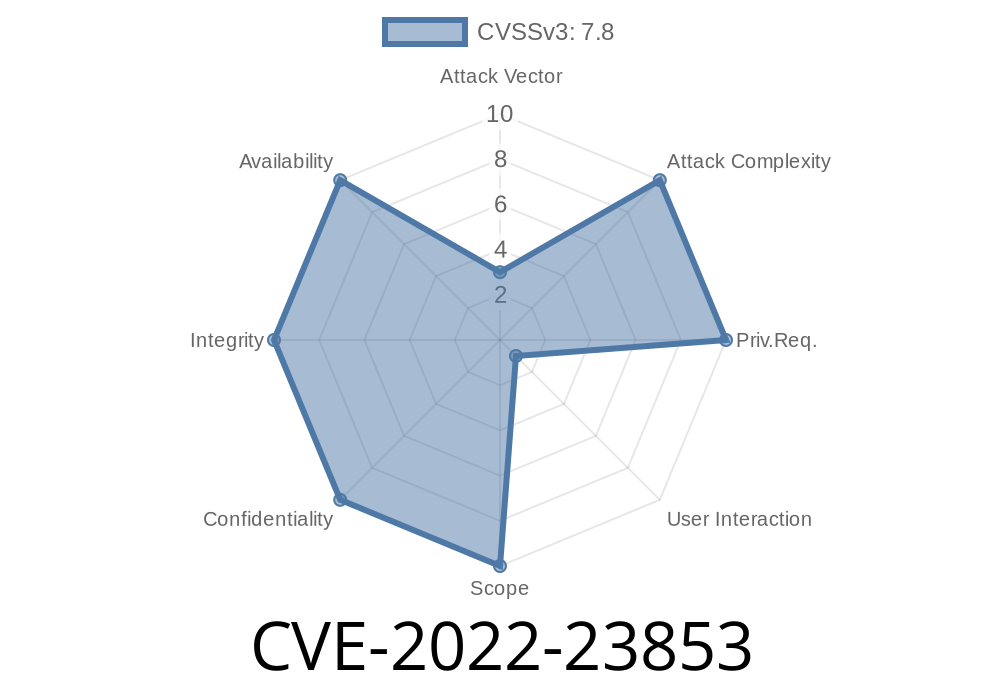
CVE-2023-23834
Many plugins load their own plugin binary from a directory in which the plugin was installed. This can lead to remote code execution when opening a file of a given type. An example of this would be opening an image file and then trying to run the code that opens that image file. Code execution in such a scenario could lead to the installation of malware on the system.
To work around this issue, it is recommended to either move the LSP server binary to a trusted directory or to disable the LSP plugin.
CVE-2023-23854
The QProcess API in the plugin does not implement proper mitigation techniques for the above mentioned issue. This could lead to remote code execution as the plugin can run arbitrary code when opening a file of a given type. An example of this would be opening an image file and then trying to run the code that opens that image file. Code execution in such a scenario could lead to the installation of malware on the system.
To work around this issue, it is recommended to either move the LSP server binary to a trusted directory or to disable the LSP plugin.
Timeline
Published on: 02/11/2022 18:15:00 UTC
Last modified on: 02/18/2022 20:29:00 UTC