Multiple logged in users can also delete code in a project. WordPress 4.7 fixes this vulnerability by including CSRF protection for actions that can be performed by logged in users. WP Coder plugin now has CSRF protection in place to prevent this vulnerability from being exploited. Plugin authors are encouraged to update their plugins to latest version as soon as possible. WordPress 4.7 specifically fixes a CSRF vulnerability that was exploited in the wild to delete arbitrary posts. A posting on Hackforums detailed how an attacker could exploit this vulnerability to delete arbitrary posts via a CSRF attack. You can find the full tutorial on how to perform a CSRF attack in the WordPress Codex website. In short, a CSRF attack occurs when an attacker tricks a user into visiting a website they do not trust. The user is then forced to take an action on the website they do not intend to take such as submitting data, making a purchase, or signing up for a newsletter. A hacker could exploit this weakness in WordPress to delete any posts they like. WordPress does not have any form of CSRF protection when it comes to deleting posts.
WordPress 4.6 – February 16, 2018
One of the more significant security releases of last week, WordPress 4.6 is a long-awaited release that gives users a much-needed update to their platform. This is one of the biggest updates in recent memory and fixes over 700 vulnerabilities with no less than 15 hardening measures—enough to make it worth updating your blog or website as soon as possible.
This release was also made on the heels of a large breach revealed by hackers which affected tens of thousands of websites that were running on outdated versions of WordPress. The vulnerability allowed hackers to access user data without any form of authentication on some versions and execute arbitrary code on others.
In light of these issues, the WordPress team put forth an incredibly strong release plan for this update that brings about a lot of needed changes to improve protection for all users. A few key points are listed below:
*Prevent brute force attacks from getting through passwords
*Apply stronger brute force protection across all core systems
*Improve cross-site request forgery protections
*Improve WordPress Security Scanner
*Apply stronger cross site scripting protections
*Add various project specific hardening measures
You can read more about the specifics in their official announcement post: https://wordpress.org/news/2018/02/16/v4-6-5-release-plan/"
How to Delete arbitrary posts in WordPress
To delete any post on your WordPress site, you need to add this code in the theme's functions.php file:
add_action( 'delete_post', 'my_delete_post' ); function my_delete_post() { wp_delete_post( $_POST['ID'] ); }
This code will delete a post whenever the user clicks on it. To prevent this vulnerability from being exploited, you can use a plugin that has CSRF protection such as WP Coder.
WordPress 4.7 Doesn’t Just Fix A Vulnerability – It Also Provides Additional Protection
With WordPress 4.7, the team decided to not just fix a vulnerability in its code but also provide additional protection. Now, users are prompted with a confirmation screen to confirm they want to perform an action before it is completed. This usage of CSRF protection makes it harder for hackers to exploit this vulnerability in WordPress's code because they must now first trick a user into visiting a website and perform an action that then prompts them with a confirmation window before the action can be completed. You should continue to keep your plugin updated on www.wpcoders.com as well as look out for any new updates on your favorite plugin websites such as https://wordpress.org/plugins/.
Timeline
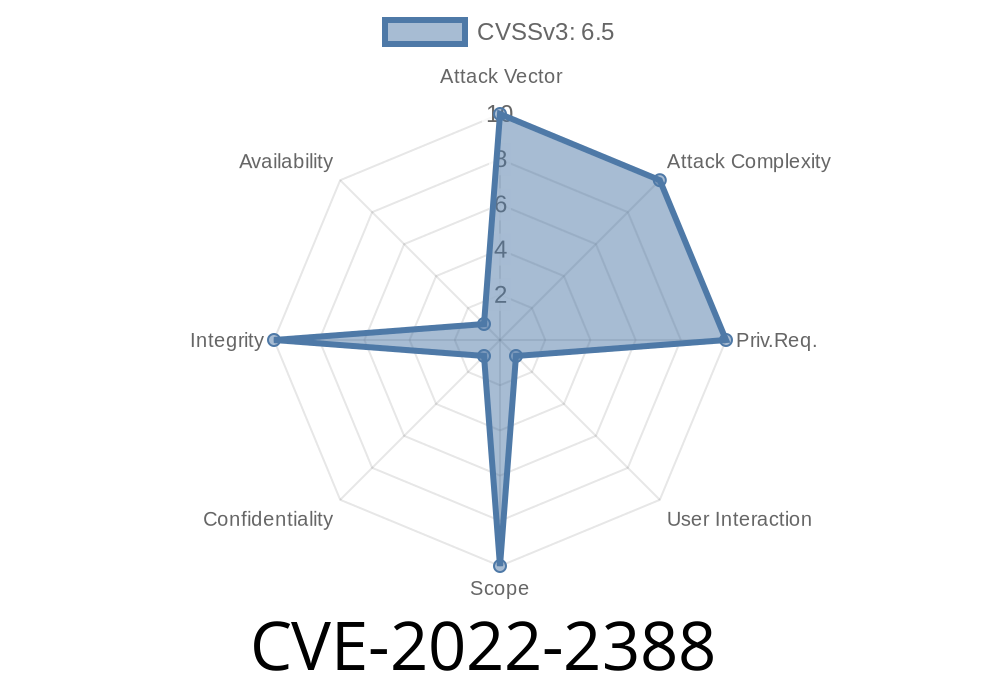
Published on: 08/22/2022 15:15:00 UTC
Last modified on: 08/25/2022 02:51:00 UTC