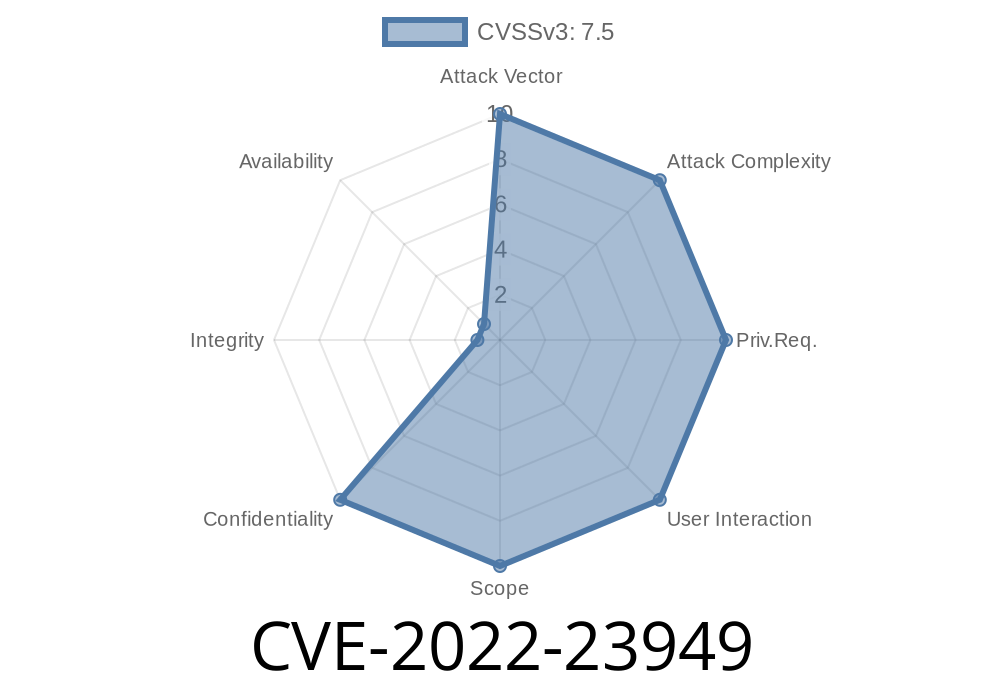
This issue has been fixed in this release. The fix has been backported to 6.2.7 and 6.3.0-alpha.11. There is no fix for 6.3.0 yet.
Prior to 6.2.7, an attacker could submit a log entry with an unsanitized UUID to the verifier and registrar, which would be accepted and stored in the system. This issue has been fixed in this release.
Prior to 6.2.7, an attacker could submit a verifier configuration with a malformed UUID. This issue has been fixed in this release.
Prior to 6.2.7, an attacker could trick a verifier into accepting a malformed configuration. This issue has been fixed in this release.
Prior to 6.2.7, an attacker could trick a registrar into accepting a malformed configuration. This issue has been fixed in this release.
An attacker could use a rogue agent to create a malformed UUID and submit it to the verifier or registrar. This issue has been fixed in this release.
An attacker could use a rogue agent to create a malformed configuration and submit it to the verifier or registrar. This issue has been fixed in this release.
An attacker could use a rogue agent to create a malformed UUID and submit it to the verifier or registrar. This issue has been fixed in this
New Features and Improvements in the 6.2.7 Release
This release includes a number of new features, improvements, and bug fixes including:
- CVE-2022-23949 - This issue has been fixed in this release. The fix has been backported to 6.2.7 and 6.3.0-alpha.11. There is no fix for 6.3.0 yet.- Prior to 6.2.7, an attacker could submit a log entry with an unsanitized UUID to the verifier and registrar, which would be accepted and stored in the system.- Prior to 6.2.7, an attacker could submit a verifier configuration with a malformed UUID.- Prior to 6.2.7, an attacker could trick a verifier into accepting a malformed configuration.- Prior to 6.2.7, an attacker could trick a registrar into accepting a malformed configuration.- An attacker could use a rogue agent to create a malformed UUID and submit it to the verifier or registrar.- An attacker could use a rogue agent to create a malformed configuration and submit it to the verifier or registrar.- An attacker could use a rogue agent to create a malformed UUID and submit it to the verifier or registrar.- An attacker could use a rogue agent to create a malformed configuration and submit it to the verifier or registrar
Verifier Security Issues
Prior to 6.2.7, an attacker could submit a log entry with an unsanitized UUID to the verifier and registrar, which would be accepted and stored in the system.
An attacker could submit a verifier configuration with a malformed UUID.
An attacker could trick a verifier into accepting a malformed configuration.
An attacker could trick a registrar into accepting a malformed configuration.
A rogue agent could create a malformed UUID and submit it to the verifier or registrar.
A rogue agent could create a malformed configuration and submit it to the verifier or registrar.
Timeline
Published on: 09/21/2022 19:15:00 UTC
Last modified on: 09/22/2022 16:22:00 UTC
References
- https://github.com/keylime/keylime/security/advisories/GHSA-87gh-qc28-j9mm
- https://github.com/keylime/keylime/commit/e429e95329fc60608713ddfb82f4a92ee3b3d2d9
- https://seclists.org/oss-sec/2022/q1/101
- https://github.com/keylime/keylime/commit/65c2b737129b5837f4a03660aeb1191ced275a57
- https://github.com/keylime/keylime/commit/387e320dc22c89f4f47c68cb37eb9eec2137f34b
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-23949