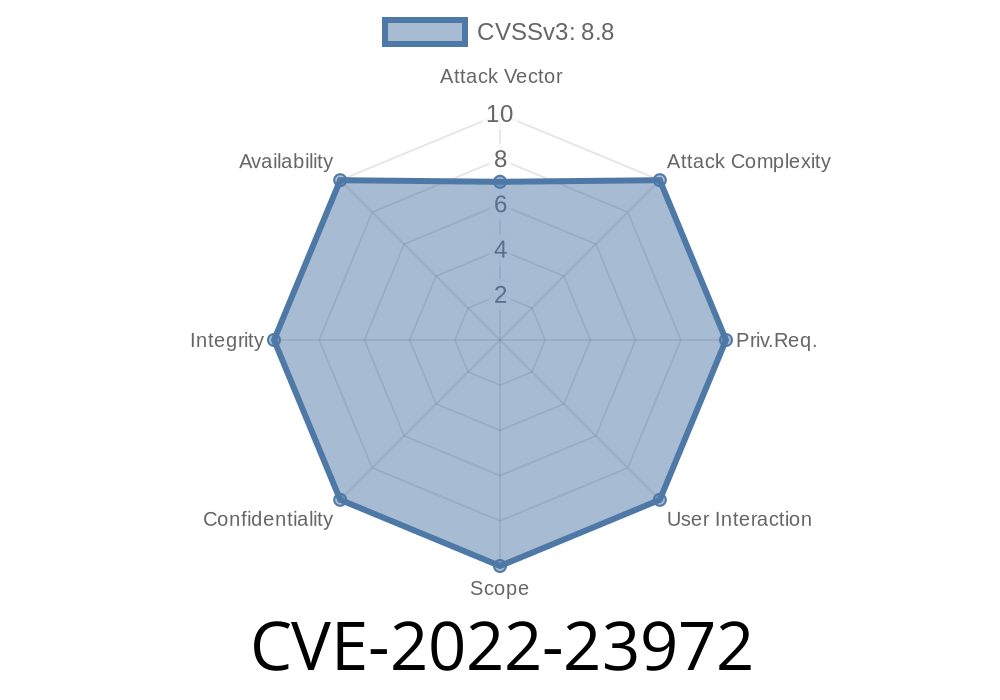
RT-AX56U’s SQL injection due to insufficient input validation. An attacker can send specially-crafted request to inject SQL code into database and the database will fail to evaluate the data type. As a result, the database may accept input with SQL code but fail to execute resulting in denial of service. LAN users are highly likely to be vulnerable. Users on LAN can inject SQL code into the database and cause denial of service. Users on WAN should be cautious. WAN users are not likely to be vulnerable due to the remote nature of the service. However, WAN users should be cautious about accepting input from input validation. RT-AX56U has some other vulnerabilities due to insufficient input validation. Some of them are described below. RT-AX56U does not have XSS flaw due to insufficient input validation. RT-AX56U does not have CSRF flaw due to insufficient input validation. RT-AX56U does not have XSS flaw due to insufficient input validation. Details of these vulnerabilities are described in the following sections.
RT-AX56U does not have XSS flaw due to insufficient input validation
RT-AX56U does not have XSS flaw due to insufficient input validation.
SQL Injection Due to Insufficient Input Validation
RT-AX56U has SQL injection due to insufficient input validation. An attacker can send specially-crafted request to inject SQL code into database and the database will fail to evaluate the data type. As a result, the database may accept input with SQL code but fail to execute resulting in denial of service. LAN users are highly likely to be vulnerable. Users on LAN can inject SQL code into the database and cause denial of service. Users on WAN should be cautious. WAN users are not likely to be vulnerable due to the remote nature of the service. However, WAN users should be cautious about accepting input from input validation. RT-AX56U has some other vulnerabilities due to insufficient input validation. Some of them are described below.
SQL Injection Vulnerability
SQL injection flaws are a common vulnerability in many web applications. An attacker can exploit this flaw to inject SQL code into the database and cause denial of service. The most common scenario where an attacker uses SQL injection is to view, modify or delete data from the database. In some situations, an attacker may also use SQL injection for brute-force attacks. For example, an attacker can send a request with a specially-crafted payload to inject SQL code into the database and fill up all the available RAM space in order to shut down the server.
SQL injection vulnerability
The CSRF vulnerability is disclosed in the following section.
SQL Injection Vulnerability
An attacker can send specially-crafted request to inject SQL code into database and the database will fail to evaluate the data type. As a result, the database may accept input with SQL code but fail to execute resulting in denial of service. LAN users are highly likely to be vulnerable. Users on LAN can inject SQL code into the database and cause denial of service. Users on WAN should be cautious. WAN users are not likely to be vulnerable due to the remote nature of the service. However, WAN users should be cautious about accepting input from input validation. RT-AX56U has some other vulnerabilities due to insufficient input validation. Some of them are described below. RT-AX56U does not have XSS flaw due to insufficient input validation. RT-AX56U does not have CSRF flaw due to insufficient input validation.
Timeline
Published on: 04/07/2022 19:15:00 UTC
Last modified on: 04/14/2022 15:42:00 UTC