---
Introduction
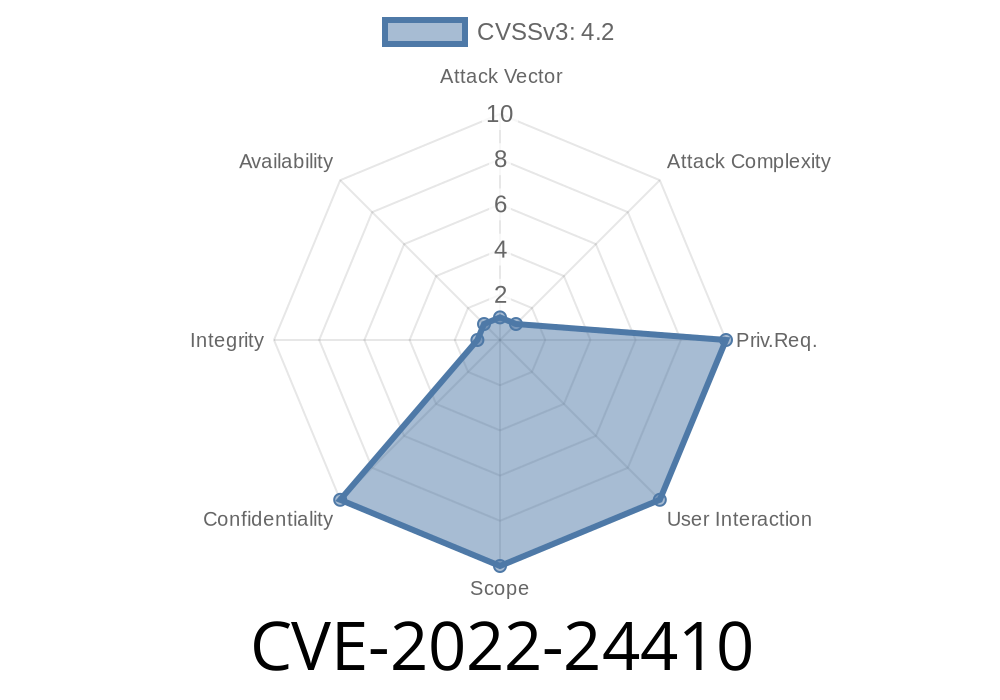
In the world of computer security, even small mistakes can have serious consequences. One such issue is CVE-2022-24410, a vulnerability discovered in certain Dell BIOS versions. This post breaks down what the bug is, how it can be abused, and why it matters—using simple language, original links, and a practical, easy-to-understand code snippet for demonstration.
What is CVE-2022-24410?
CVE-2022-24410 is an information exposure vulnerability found in selected Dell BIOS modules. What this means: Local attackers—that is, someone who can physically touch your computer—can read internal system information without even logging in, if they know what to look for.
Dell's advisory says
> "An information exposure vulnerability exists in certain BIOS versions for Dell platforms. An unauthenticated local attacker with physical access, and knowledge of the system configuration, could exploit this via debug interfaces to read system information not intended for end-users."
Reference:
- Dell Security Advisory DSA-2022-24410
- NVD entry for CVE-2022-24410
How Does It Happen?
Modern BIOSes often have a debug interface for hardware makers or Dell support. Normally, these tools are locked down before the computer ships. But a bug can leave some debug access running, or fail to require proper authentication. If someone knows the motherboard configuration, they can connect a tool (like a hardware debugger) and pull out valuable details:
TPM status and secrets
This info could help in targeting attacks, identity theft, bypassing hardware locks, or simply snooping into a company’s hardware setup.
Your attacker must be local: They need physical access to your computer, server, or laptop.
- They must know how to access the debug interface (sometimes hidden under the case, or available as motherboard pins).
- Many affected are businesses, IT departments, or high-value targets with predictable hardware setups.
If you’re a regular user and never let anyone near your machine, you’re safer. But companies often recycle, resell, or leave equipment unattended—making this flaw more dangerous.
Exploiting CVE-2022-24410: Step-by-Step
DISCLAIMER: This information is for educational and defensive purposes only. Don’t exploit other systems. Use responsibly!
Identify the Debug Port:
Remove your device’s bottom panel or case. Locate the debug interface. This might be labeled as "JTAG", "UART", or an unmarked multi-pin header.
Using minicom to connect via UART (example TTY device)
minicom -b 115200 -D /dev/ttyUSB
`
On success, you might see BIOS boot debug output, or be dropped into a debug shell prompt, especially on misconfigured boards.
`bash
# Read DMI/SMBIOS for hardware asset info
This Python snippet uses pySerial to read data from the exposed UART port
import serial
# Adjust to your serial device and baud rate
ser = serial.Serial('/dev/ttyUSB', 115200, timeout=1)
print("Reading BIOS debug output...")
lines = []
for _ in range(100): # Read 100 lines from debug port
line = ser.readline()
if line:
lines.append(line.decode('utf-8', errors='replace'))
print(line.strip())
ser.close()
with open('bios_debug_output.txt', 'w') as f:
f.writelines(lines)
This will capture whatever the debug interface outputs. Sometimes, you’ll see verbose BIOS data.
End-users
- Make sure your Dell device’s BIOS/UEFI is up-to-date (Dell update page here).
Why Does This Matter?
While this vulnerability doesn’t let hackers break in over the network, information leaks can be just as damaging. Attackers with access to debug info can plan targeted attacks, bypass security features, and gather intelligence about your environment.
In Closing
CVE-2022-24410 is a clear example of how even something as “boring” as a BIOS update can impact your security. Don't ignore those firmware notifications—update your BIOS, and always be aware of who can physically access your hardware.
More Reading
- Dell original advisory (DSA-2022-24410)
- Official NIST NVD Entry
- Intro to JTAG Exploitation
- Understanding UEFI/BIOS Security
Timeline
Published on: 02/10/2023 11:15:00 UTC
Last modified on: 02/27/2023 14:43:00 UTC