This vulnerability may be exploited by a local user or remote attacker by sending an SMI to the system. To exploit the issue, an attacker must be logged in as an administrator, be able to send messages to the affected system, and have permissions to install SMI packages. End users and remote attackers cannot exploit this issue. To correct this issue, update your system’s BIOS to the latest version. Note: It may take up to 90 days for all systems with an older BIOS to be updated. Dell has provided updated instructions on how to update the BIOS on your system.
Vulnerability details
The vulnerability may be exploited by a local user or remote attacker by sending an SMI to the system. To exploit the issue, an attacker must be logged in as an administrator, be able to send messages to the affected system, and have permissions to install SMI packages. End users and remote attackers cannot exploit this issue. To correct this issue, update your system’s BIOS to the latest version. Note: It may take up to 90 days for all systems with an older BIOS to be updated. Dell has provided updated instructions on how to update the BIOS on your system
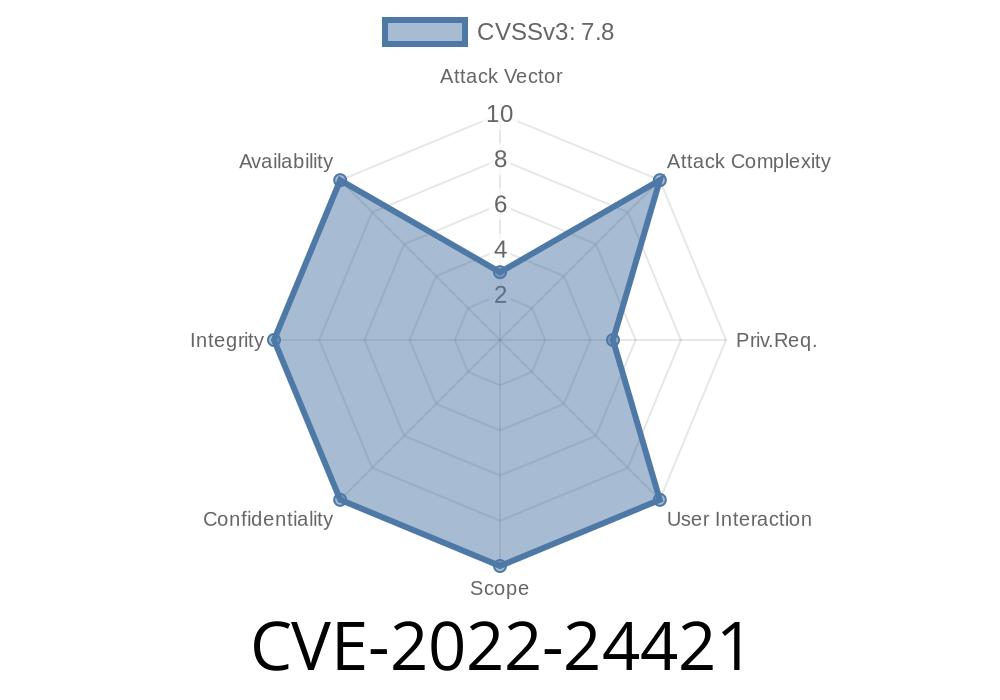
This vulnerability was disclosed on October 25th, 2017 and is CVE-2022-24421
Vulnerability Details
This vulnerability may be exploited by a local user or remote attacker by sending an SMI to the system. To exploit the issue, an attacker must be logged in as an administrator, be able to send messages to the affected system, and have permissions to install SMI packages. End users and remote attackers cannot exploit this issue. To correct this issue, update your system’s BIOS to the latest version. Note: It may take up to 90 days for all systems with an older BIOS to be updated. Dell has provided updated instructions on how to update the BIOS on your system.
Vulnerability Overview
A vulnerability has been discovered on Dell systems with BIOS version 11.3.0, which could allow an attacker to install a malicious service management interface (SMI) package.
To exploit the vulnerability, an attacker must be logged in as an administrator and have permissions to send messages to the affected system. End users and remote attackers cannot exploit this issue.
Vulnerability Overview and Technical Description
Dell has discovered a BIOS vulnerability that may be exploited by remote attackers to gain administrative access. The vulnerability is rated as CV-2022-24421, and is designated as “Low” severity.
To exploit this vulnerability, an attacker must first be able to send messages to the affected system. The attacker must also have permission to install SMI packages on the system. These permissions can only be accomplished by an administrator of the system. End users and remote attackers cannot exploit this issue. To correct this issue, update your system’s BIOS to the latest version. Note: It may take up to 90 days for all systems with an older BIOS to be updated. Dell has provided updated instructions on how to update the BIOS on your system.
Timeline
Published on: 03/11/2022 22:15:00 UTC
Last modified on: 03/18/2022 20:20:00 UTC