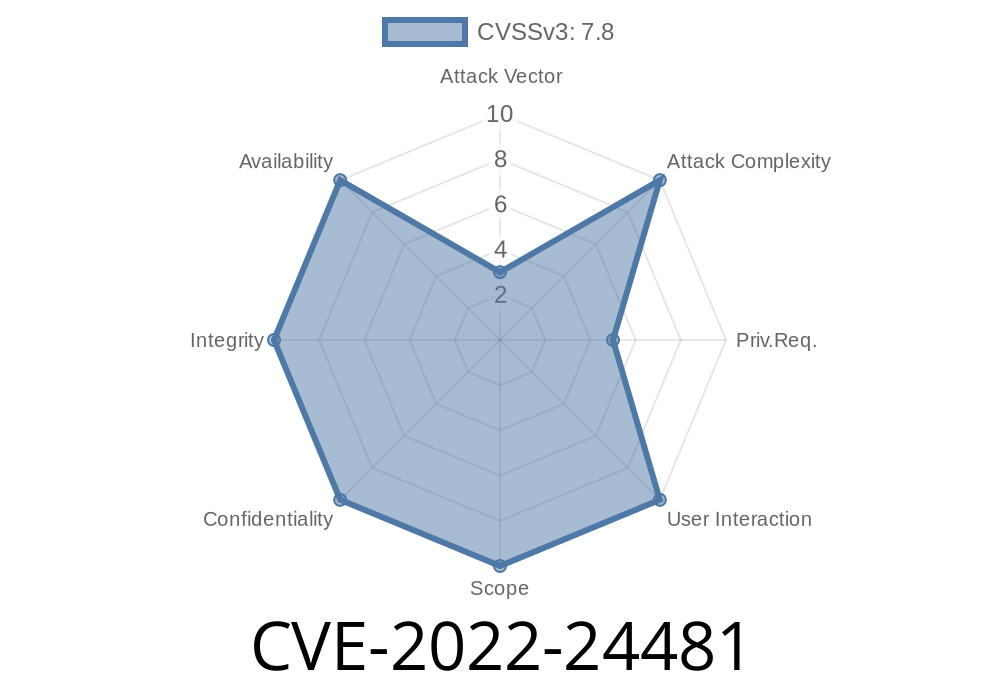
This vulnerability is caused by a bug in the way that Windows handles log files. An attacker could exploit this vulnerability by tricking a user into opening a malicious log file. The attacker could then execute code with SYSTEM privileges.
An attacker could also exploit this vulnerability by tricking an administrator into installing a malicious driver.
In the latter case, the attacker could then install a malicious driver that could then take advantage of this vulnerability.
Workaround If you are using Windows 7 or Windows 8, you can reduce the risk of being exploited by an attacker by ensuring that the user has read permission for any file before the user opens it. If you are using a version of Windows prior to Windows 7 or Windows 8, you will need to manually remove the security restrictions on the file or directory that the user is allowed to access.
Microsoft Workaround to Enable Remote Desktop in Windows 7/8
If you are running Windows 7 or Windows 8 and want to enable remote desktop in your environment, you may need to disable the security restrictions. There are two steps to this process:
- First, open the properties of the file or directory that the user should have access to. On a Windows 7 system, click on Computer from the top navigation bar. Then click Properties on the left-hand side of the screen. On a Windows 8 System, click on this application's tile from the start screen then select Properties on the right-hand side of the screen.
- Second, go to Security Settings > Advanced Tab > Run programs and scripts (Local account) then select Disable all items except signed and approved apps.
Mitigation Strategies: What You Can Do
You can mitigate this vulnerability by ensuring that the user has read permissions for any file before the user opens it.
If you are using a version of Windows prior to Windows 7 or Windows 8, you need to manually remove the security restrictions on the file or directory that the user is allowed to access.
If you are using Windows 7 or Windows 8, you can reduce the risk of being exploited by an attacker by ensuring that the user has read permission for any file before the user opens it.
Microsoft has provided a workaround for this vulnerability
Vulnerability details
This vulnerability is caused by a bug in the way that Windows handles log files. An attacker could exploit this vulnerability by tricking a user into opening a malicious log file. The attacker could then execute code with SYSTEM privileges.
An attacker could also exploit this vulnerability by tricking an administrator into installing a malicious driver.
In the latter case, the attacker could then install a malicious driver that could then take advantage of this vulnerability.
Timeline
Published on: 04/15/2022 19:15:00 UTC
Last modified on: 04/22/2022 16:46:00 UTC