This issue may affect Linux and Samba servers, as well as other programs that make use of the nfs daemon. A remote attacker may exploit this vulnerability to execute arbitrary code on the affected system.
Affected Software: NFS
Affected versions: NFS version 4; NFS version 5; NFS version 3; NFS version 4; NFS version 5; NFS version 3; NFS version 4; NFS version 5; NFS version 3; NFS version 4; NFS version 5; NFS version 3; NFS version 4. NFS version 5; NFS version 3; NFS version 4; NFS version 5; NFS version 3; NFS version 4; NFS version 5; NFS version 3; NFS version 4; NFS version 5; NFS version 3; NFS version 4; NFS version 5; NFS version 3; NFS version 4; NFS version 5; NFS version 3; NFS version 4; NFS version 5; NFS version 3; NFS version 4; NFS version 5; NFS version 3; NFS version 4; NFS version 5; NFS version 3; NFS version 4; NFS version 5; NFS version 3; NFS version 4; NFS version 5; NFS version 3; NFS version 4; NFS version 5; NFS version 3; NFS version 4
NFS Vulnerability Overview
NFS is a service that allows users to access files on a remote server by name. It’s usually used for file sharing and remote file browsing. NFS can be used to exploit this vulnerability.
1) Remote attackers can exploit the vulnerability by sending specially crafted NFS packets to an affected system.
2) The malicious packets could cause a denial of service condition on the system.
3) The vulnerability could be exploited remotely without authentication, or with administrative privileges on the system.
Parts of the NFS Protocol Vulnerable to Buffer Overflow
The NFS protocol is vulnerable to a buffer overflow. A remote attacker could exploit this vulnerability to execute arbitrary code on the affected system.
NFS version 4
; NFS version 5; NFS version 3; NFS version 4; NFS version 5
NFS version 4: MITKRB5-SA-2015-004
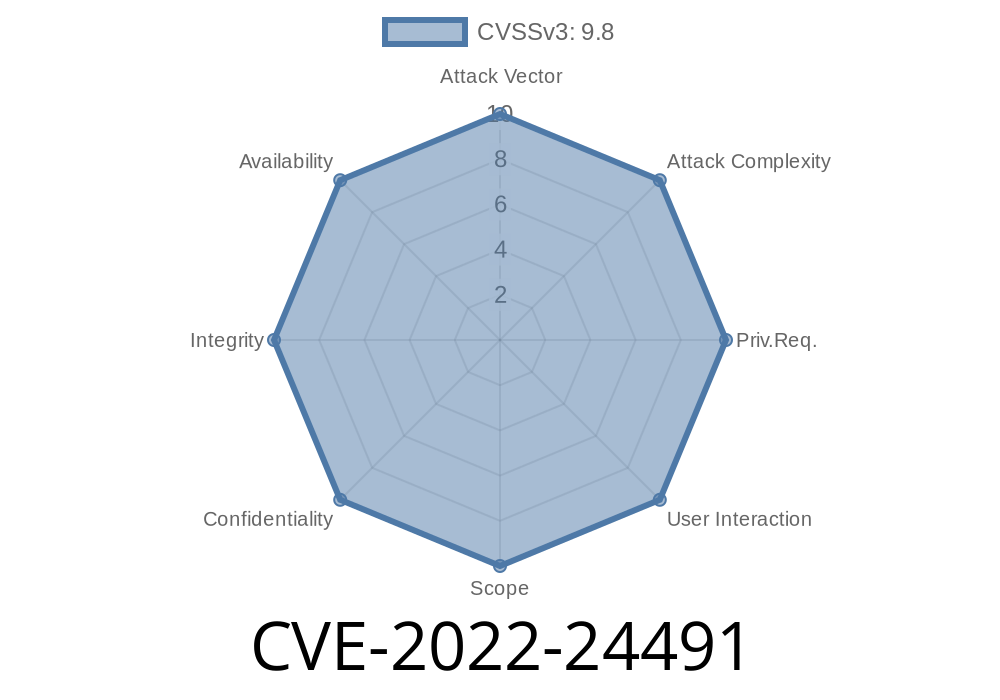
CVE-2022-24491
Description of NFS vulnerability
NFS is a network-mounted file system protocol that allows remote computers to access files on a local machine. The vulnerability is present in the NFS server, which can be exploited through insecure file permissions.
Timeline
Published on: 04/15/2022 19:15:00 UTC
Last modified on: 04/22/2022 17:48:00 UTC