In early 2022, Microsoft patched a notable security vulnerability affecting the Windows iSCSI Target Service, tracked as CVE-2022-24498. This flaw allows an attacker to gain access to potentially sensitive information under certain conditions, posing a risk to data confidentiality in enterprise environments. In this deep dive, we’ll walk through what this vulnerability is, how it works, provide a real-world code sample to illustrate the issue, and share resources for better understanding and remediation.
What Is Windows iSCSI Target Service?
The iSCSI Target Service in Windows enables network-attached storage over TCP/IP. System admins use it to present block storage to clients, like Windows or Linux servers, over a network. If the target service leaks information, it could expose details about existing virtual disks or authentication data, leading to further exploitation.
The Vulnerability Details
CVE-2022-24498 is an information disclosure vulnerability found in the logic that handles iSCSI requests. If exploited, a remote unauthenticated attacker could retrieve memory content from the iSCSI Target Service process. This might reveal sensitive configuration settings, credentials, or details about connected volumes.
CVSS Score
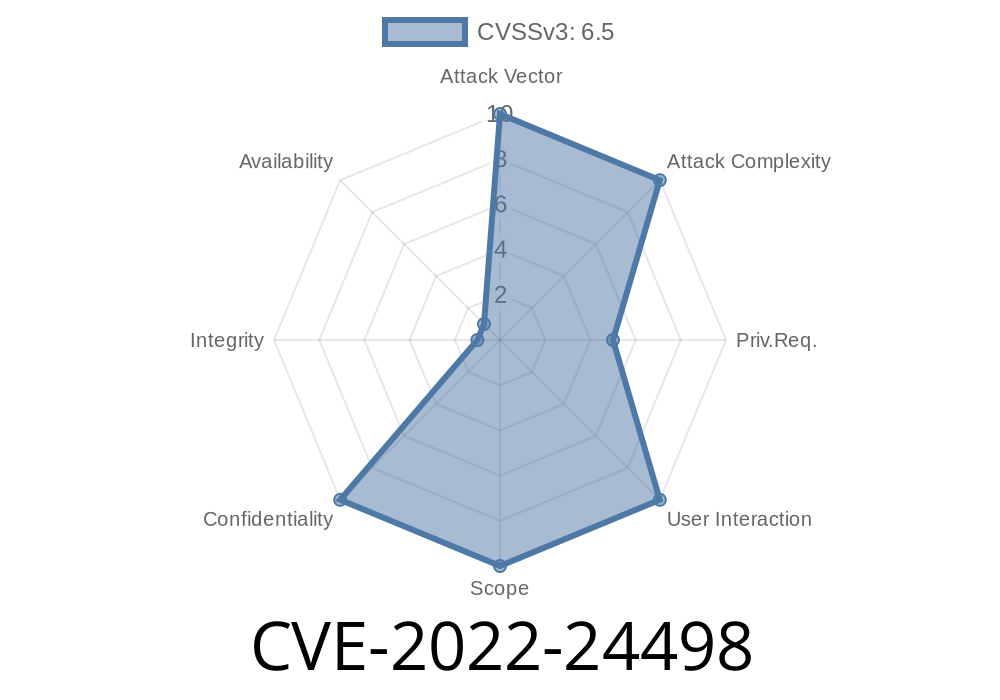
- CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N
Microsoft’s Official Page
How Does It Work? (Exploit Path)
When an attacker sends deliberately malformed or unexpected SCSI commands to the target service, it may mishandle these and leak contents of memory in the response. Since iSCSI is often used internally in data centers, attackers must typically have access to the target port (default TCP 326). On certain network setups, the port may be open to untrusted users or attackers on the same subnet.
Exploit Example
Below is a simplified Python code snippet that sends an unusual SCSI command (with crafted parameters) to a Windows iSCSI Target. If the system is vulnerable and unpatched, it may respond with unexpected data, potentially including leaked memory:
import socket
# Target IP and port
TARGET_IP = '192.168.1.100'
TARGET_PORT = 326
# Example: Minimal iSCSI PDU with crafted data (not a real iSCSI CMD)
# In practice, attackers craft more valid packets to trigger the fault
iscsi_packet = bytes.fromhex(
'00' # Opcode (NOP Out, for example)
'00' * 47 # Filler to create a minimal 48-byte iSCSI PDU
)
with socket.socket(socket.AF_INET, socket.SOCK_STREAM) as s:
s.connect((TARGET_IP, TARGET_PORT))
s.send(iscsi_packet)
response = s.recv(4096)
print("Received:", response.hex())
# Analyze response for memory leaks or uninitialized data
> Disclaimer: This code is for demonstration and educational purposes only. Do not use on networks or systems without proper authorization.
Potential Impact
- Sensitive data exposure: Attackers could obtain system configuration, usernames, or passwords stored in process memory.
- Further exploitation: With leaked data, attackers might escalate privileges, move laterally, or access protected volumes.
Install Microsoft’s Security Patch:
Always patch your Windows servers using Windows Update or the official security advisory.
References
- Microsoft MSRC Advisory: CVE-2022-24498
- iSCSI Overview – Microsoft Docs
- Common Vulnerability Scoring System (CVSS)
Conclusion
CVE-2022-24498 may not grab headlines like “wormable” vulnerabilities, but for environments depending on iSCSI storage, it is a real risk. Information disclosure bugs often pave the way for bigger breaches, especially in infrastructure and virtualization-heavy deployments. Patch early, restrict access, and stay vigilant!
If you run iSCSI on Windows servers, securing against CVE-2022-24498 is a must for keeping your data out of attackers’ hands.
Timeline
Published on: 04/15/2022 19:15:00 UTC
Last modified on: 04/22/2022 15:38:00 UTC