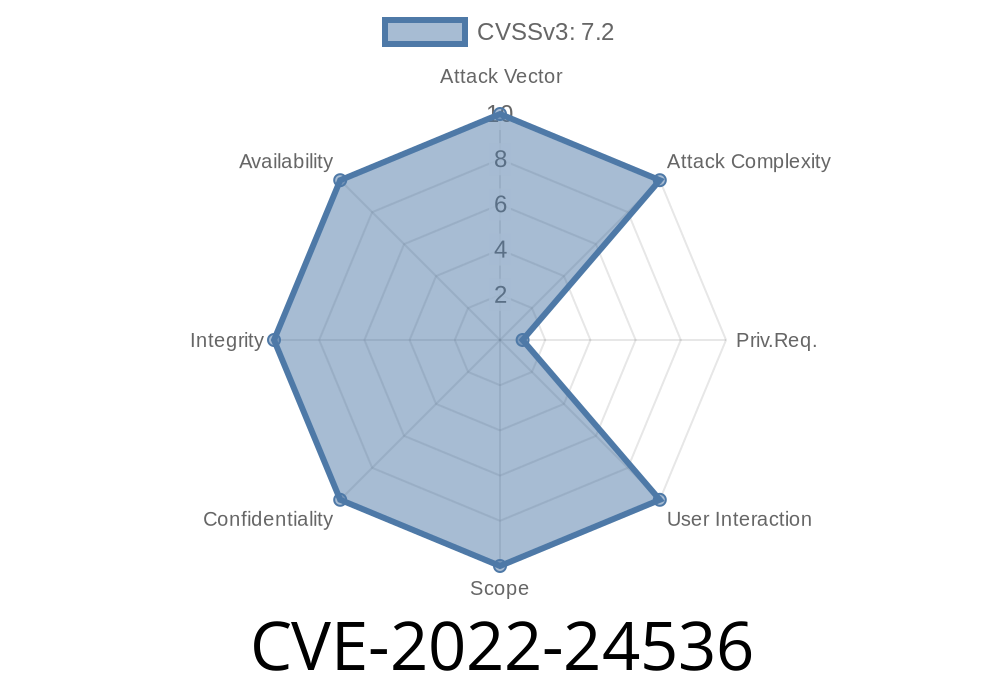
This vulnerability was discovered by Nart Villeneuve (Twitter: @Nart Villeneuve). This issue has been assigned a Common Vulnerability and Exposure Code (CVE ID) as a result of its potential to negatively impact system users. Exploitation of this issue may result in unauthorized code execution. DNS software is an application that allows users to resolve domain names to Internet Protocol (IP) addresses and other information. A remote code execution vulnerability has been discovered in a widely used DNS software. This vulnerability was found in the dnsmasq software which is used as a DNS forwarder on various GNU/Linux distributions such as Debian, CentOS, Red Hat, and Ubuntu. The dnsmasq software is used on the router/switch to provide DNS services for the devices connected to these network devices. This issue does not affect dnsmasq if it is used as a hostname server for the devices connected to the network device. This issue only affects dnsmasq if it is used as a DNS forwarder on a router/switch. This issue was initially discovered by Nart Villeneuve (Twitter: @Nart Villeneuve of Sec Consult). Nart reported this issue to CERT/CC on the 1st of October 2017.
Description
A remote code execution vulnerability has been discovered in the dnsmasq software which is a widely used DNS forwarder on various Linux systems. This issue only affects dnsmasq if it is used as a DNS forwarder on a router/switch and not if it is used as a hostname server for the devices connected to the network device. The vulnerability was discovered by Nart Villeneuve (Twitter: @Nart Villeneuve of Sec Consult) and reported to CERT/CC on October 1st, 2017.
Vulnerability Details
This vulnerability is caused due to the nss library and libnss3. The nss library is used by various applications and libraries to provide secure networking services. This issue was discovered in nss-pam and nscd versions prior to 3.14.2 and 3.15.2 respectively which are not widely used. This issue was originally found in the Debian based operating systems such as Debian, CentOS, Red Hat, and Ubuntu which are distributions of GNU/Linux on a computer system that are running a version of dnsmasq that has been patched for CVE-2022-24536 through a patch provided by the upstream vendor of dnsmasq.
Description of the dnsmasq DNS software vulnerability
The vulnerability is present in dnsmasq. A remote code execution vulnerability has been discovered in the dnsmasq software which is used as a DNS forwarder on various GNU/Linux distributions such as Debian, CentOS, Red Hat, and Ubuntu. This issue does not affect dnsmasq if it is used as a hostname server for the devices connected to the network device. The vulnerability was first discovered by Nart Villeneuve (Twitter: @Nart Villeneuve of Sec Consult).
Timeline
Published on: 04/15/2022 19:15:00 UTC
Last modified on: 04/19/2022 16:42:00 UTC