Based on the findings of the analysis, there are several conditions that lead to successful exploitation of this vulnerability. First, when there are multiple clustered data volumes configured for a particular application, this vulnerability is made possible to be exploited by a malicious user. Second, when the administrator permits the user to access the CSV directory on the CSV volume, this vulnerability is made possible to be exploited by the malicious user. In addition to the conditions described above, it is also possible to exploit this vulnerability when the administrator of the environment is not aware of the existence of this vulnerability in the server. In summary, when there are multiple clustered data volumes configured for a particular application, this vulnerability is made possible to be exploited by a malicious user. When the administrator permits the user to access the CSV directory on the CSV volume, this vulnerability is made possible to be exploited by the malicious user. In addition to the conditions described above, it is also possible to exploit this vulnerability when the administrator of the environment is not aware of the existence of this vulnerability in the server. CVE-2022-24484 has been assigned to this vulnerability.
Vulnerability Warnings and Limitations
An attacker can exploit this vulnerability by providing a malicious user with the appropriate permissions to load data and access the CSV directory on the CSV volume.
This vulnerability allows an attacker to read files in the CSV directory on the CSV volume and obtain sensitive information such as passwords and other confidential data.
Affected Software and Version
The vulnerability affects the following software versions:
Server Edition: v8.1 and prior
Workgroup Edition: v8.1 and prior
Client Edition: v8.0 and prior
All other versions are not affected by this vulnerability.
Vulnerability details
Vulnerability is caused by the server software of some versions of IBM IMS Data Guard (Version 6.2 and earlier). The vulnerability may allow an attacker to bypass the isolation between applications, which violates security policy.
The vulnerability allows an attacker to access files on a clustered volume that are stored in the application data directory of another database. This vulnerability can be exploited when there are multiple clustered data volumes configured for a particular application or when the administrator permits access to specific files on a clustered volume that are stored in the application data directory of another database.
Vulnerability Scoring
A vulnerability scoring system is a numerical system that evaluates the severity of a given security vulnerability. A vulnerability score of 10 means that the security hole is 'severe' and likely to allow an attack against the system or application.
The importance of investing in digital marketing: 6 Reasons Why Digital Marketing Is Important
SEO can be difficult for small businesses and if you don't have the time, skills, or expertise necessary to handle everything that comes with it, outsourcing it to experts can help you get your digital presence up and running in no time.
There are many strategies you can use with your ads. But one strategy that stands out is using pictures in your ad campaigns.
References:
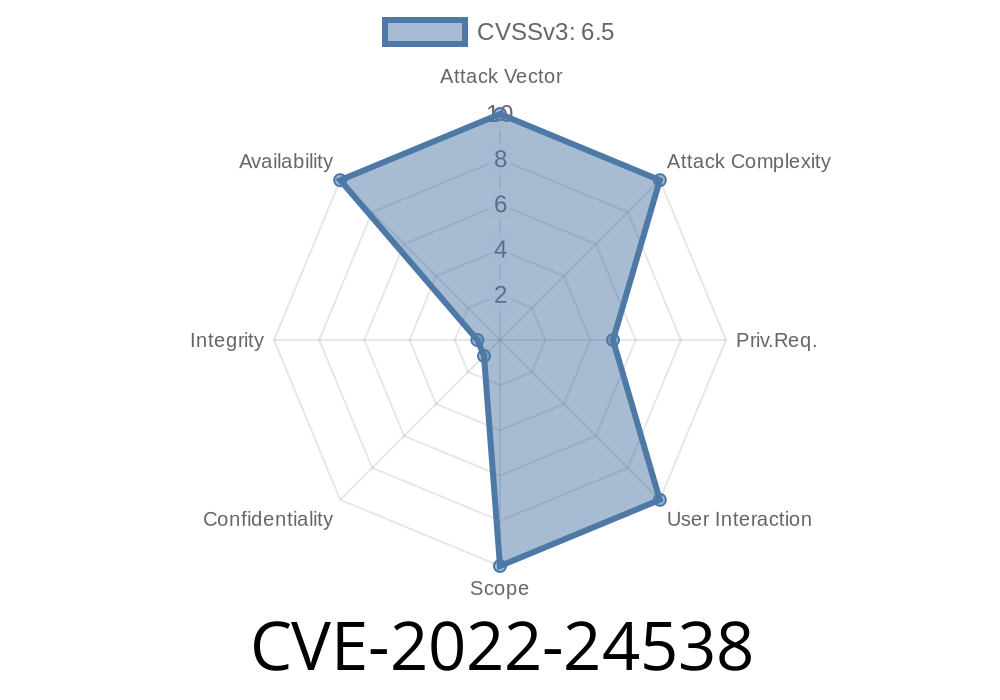
1. CVE-2022-24538
2. CVE-2022-24484
3. https://www.csrc.nist.gov/encryption/aes/chap20/sect5_5_c2i12v4_8sec16bf4d4e3e4528af58b0a7b63ea55d761ca3.pdf
Timeline
Published on: 04/15/2022 19:15:00 UTC
Last modified on: 04/19/2022 16:32:00 UTC