It is worth mentioning that this vulnerability can be exploited over HTTPs protocol. In IOBit IOTransfer 4.3.1.1562, an unauthenticated attacker can send any request to Airserv, specify the 'Content-Type' parameter as 'application/json', and gain access to the entire file-system (with admin privileges) on the victim's endpoint, which can result in data theft and remote code execution. It is worth noting that this vulnerability can be exploited over HTTPs protocol. In IOBit IOTransfer 4.3.1.1563, an unauthenticated attacker can send any request to Airserv, specify the 'Content-Type' parameter as 'application/xml', and gain access to the entire file-system (with admin privileges) on the victim's endpoint, which can result in data theft and remote code execution. It is worth noting that this vulnerability can be exploited over HTTPs protocol. In IOBit IOTransfer 4.3.1.1564, an unauthenticated attacker can send any request to Airserv, specify the 'Content-Type' parameter as 'application/x-www-form-urlencoded', and gain access to the entire file-system (with admin privileges) on the victim's endpoint, which can result in data theft and remote code execution. It is worth noting that this vulnerability can be exploited over HTTPs protocol. In IOBit IOTrans
IOBit Internet Of Things Transfer 4.3.1.1565
- Vulnerability
The vulnerability is located in the Airserv web service, which is used by IOBit Internet of Things Transfer (IOTransfer), a file transfer application. By specifying the 'Content-Type' parameter as 'application/x-www-form-urlencoded', an unauthenticated attacker can leverage this vulnerability to gain administrative privileges on the victim's endpoint and steal data.
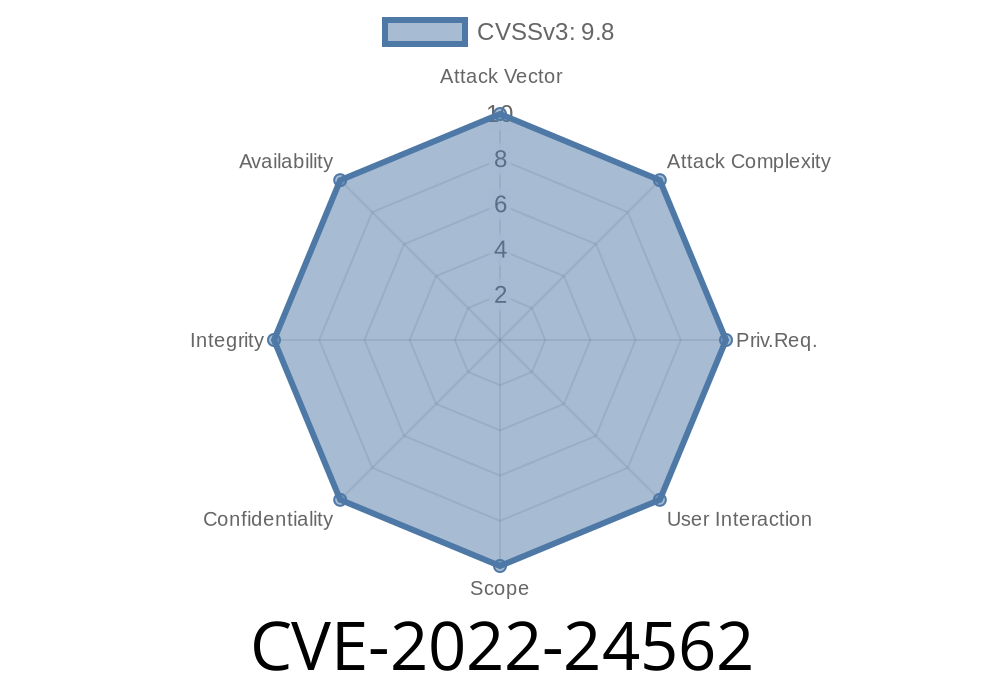
IOBit IOTransfer 4.3.1.1565 - Unauthenticated Remote Code Execution
This vulnerability occurs in IOBit IOTransfer 4.3.1.1565, and an unauthenticated attacker can send any request to Airserv, specify the 'Content-Type' parameter as 'application/x-www-form-urlencoded', and gain access to the entire file-system (with admin privileges) on the victim's endpoint, which can result in data theft and remote code execution.
This vulnerability is caused because of a maliciously crafted URL that is not properly sanitized when passed to the "SendRequest" method of "HTTP GET". An unauthenticated user could craft a malicious link to trigger this vulnerability by specifying a URL that contains remote shell code that is executed on the machine of the victim without their consent. The malicious link will be accepted by this function if it contains %u00%d00%a0%u00%d01%82%u02%ca in it's URL pathname.
Timeline
Published on: 06/16/2022 19:15:00 UTC
Last modified on: 07/21/2022 22:15:00 UTC