These devices are no longer supported and the QNX Software Security Incident Response Team (SSIRT) recommends disabling the ssh daemon and removing hardcoded credentials from all systems in a network.
The following versions of these devices are vulnerable: - BBox Nova436Q v1.0 Bbbox Neutrino 430 v1.0 Bbbox Nova460 v1.0 Bbbox Nova460 v1.0 Pro - Bbx X10 v1.0 Bbx X20 v1.0 Bbx X30 v1.0 Bbx X60 v1.0 Bbx X60 v1.0 Pro - Cb10 X10 v1.0 Cb10 X20 v1.0 Cb10 X30 v1.0 Cb10 X60 v1.0 Cb10 X60 v1.0 Pro - Cb12 X10 v1.0 Cb12 X20 v1.0 Cb12 X30 v1.0 Cb12 X60 v1.0 Cb12 X60 v1.0 Pro - Cb16 X10 v1.0 Cb16 X20 v1.0 Cb16 X30 v1.0 Cb16 X60 v1.0 Cb16 X60 v1.0 Pro - Cb32 X10 v1.0 Cb32 X20 v1.0 Cb32 X30
Description of Vulnerability##
Vulnerability: Remote Code Execution by SSH Access
Remote Code Execution by SSH Access
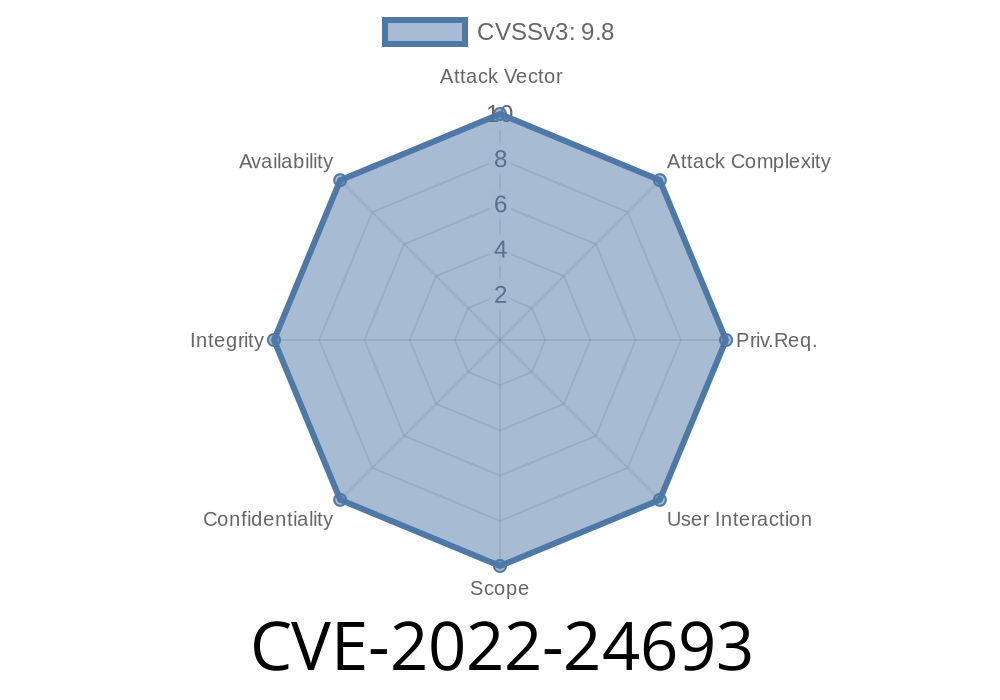
CVE-2022-24693
These devices are no longer supported and the QNX Software Security Incident Response Team (SSIRT) recommends disabling the ssh daemon and removing hardcoded credentials from all systems in a network.
The following versions of these devices are vulnerable: - BBox Nova436Q v1.0 Bbbox Neutrino 430 v1.0 Bbbox Nova460 v1.0 Bbbox Nova460 v1.0 Pro - Bbx X10 v1.0 Bbx X20 v1.0 Bbx X30 v1.0 Bbx X60 v1.0 Bbx X60 v1.0 Pro - Cb10 X10 v1.0 Cb10 X20 v1.0 Cb10 X30 v1.0 Cb10 X60 v1.0 Cb10 X60 v1.0 Pro - Cb12 X10 v1.0 Cb12 X20 v1.0 Cb12 X30 v1.0 Cb12 X60 v1.0 Cb12 X60 v1.0 Pro - Cb16 X10 v1.0 Cb16 X20
Timeline
Published on: 03/30/2022 02:15:00 UTC
Last modified on: 04/07/2022 16:08:00 UTC