A cross site request forgery (CSRF) vulnerability has been discovered in the web interface of the VNC server. The web interface allows an attacker to perform actions that affect the logged in user. If an attacker is able to access the VNC server via an exploit, they can access the localhost interface on a vulnerable system. It is recommended that users upgrade their VNC server to 1.4.4 to confirm this vulnerability has been patched. It is also recommended to create a scheduled task on a low privilege account to launch VNC instead. There are no known workarounds if VNC needs to be run as a service.
A privilege escalation vulnerability has been discovered in the web interface of the VNC server. The web interface allows an attacker to perform actions that affect the logged in user. If an attacker is able to access the VNC server via an exploit, they can access the localhost interface on a vulnerable system. It is recommended that users upgrade their VNC server to 1.4.4 to confirm this vulnerability has been patched. It is also recommended to create a scheduled task on a low privilege account to launch VNC instead. There are no known workarounds if VNC needs to be run as a service.
An information disclosure vulnerability has been discovered in the web interface of the VNC server. The web interface allows an attacker to perform actions that affect the logged in user. If an attacker is able to access the VNC server via
CSRF vulnerability
VNC server via an exploit, they can access the localhost interface on a vulnerable system. It is recommended that users upgrade their VNC server to 1.4.4 to confirm this vulnerability has been patched. It is also recommended to create a scheduled task on a low privilege account to launch VNC instead. There are no known workarounds if VNC needs to be run as a service.
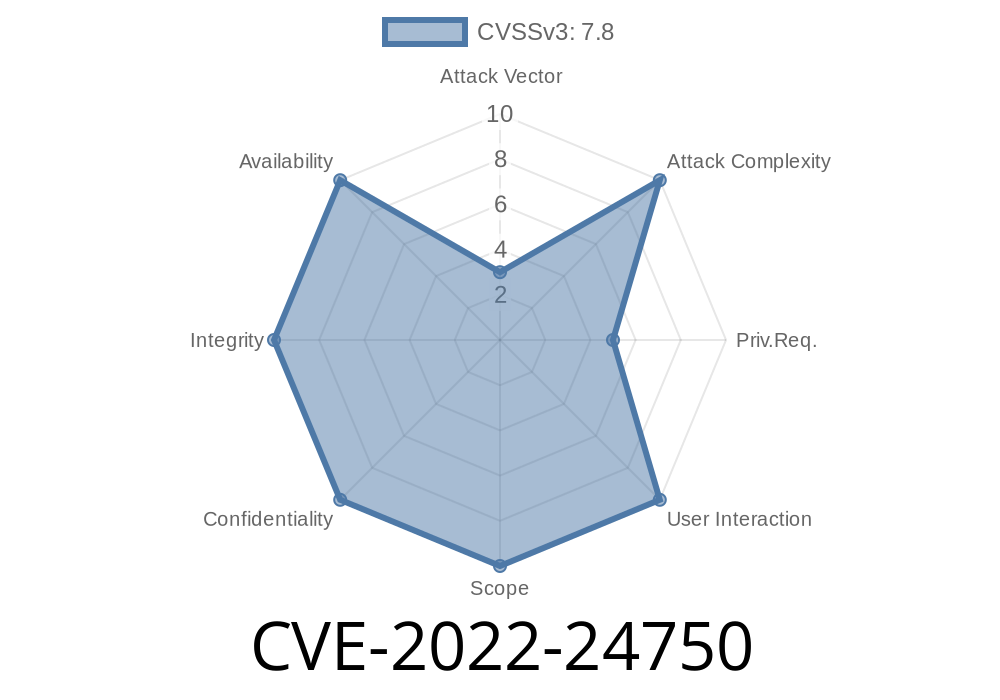
An information disclosure vulnerability has been discovered in the web interface of the VNC server. The web interface allows an attacker to perform actions that affect the logged in user. If an attacker is able to access the VNC server via an exploit, they can access the localhost interface on a vulnerable system. It is recommended that users upgrade their VNC server to 1.4.4 to confirm this vulnerability has been patched. It is also recommended to create a scheduled task on a low privilege account to launch VNC instead. There are no known workarounds if VNC needs to be run as a service.
Timeline
Published on: 03/10/2022 21:15:00 UTC
Last modified on: 03/18/2022 20:06:00 UTC