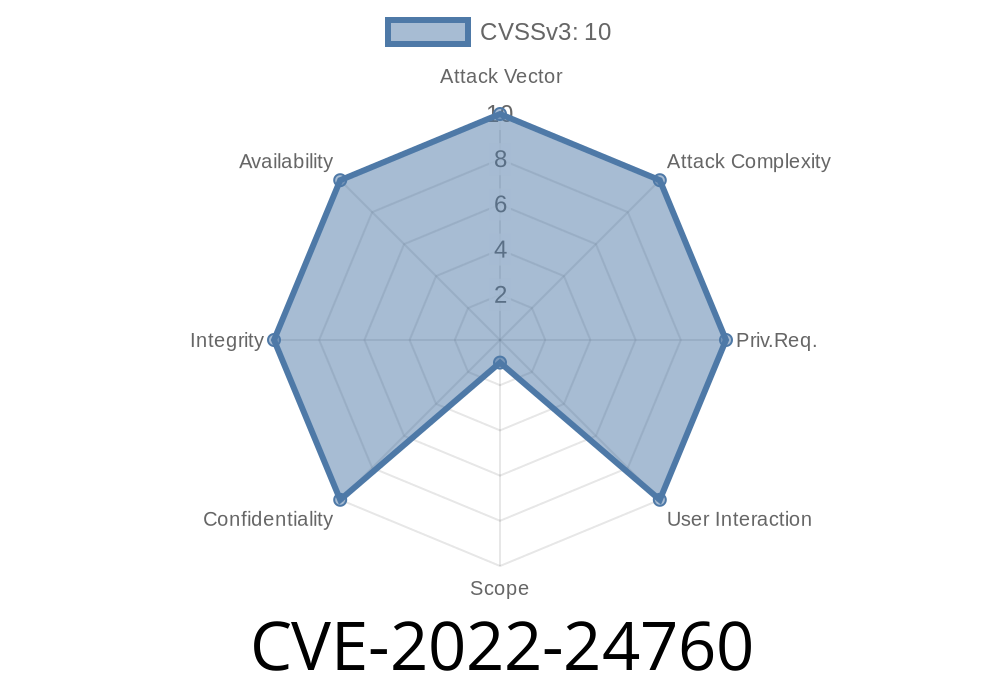
Parse Server is an open source http web server backend. In versions prior to 4.10.7 there is a Remote Code Execution (RCE) vulnerability in Parse Server. This vulnerability affects Parse Server in the default configuration with MongoDB. The main weakness that leads to RCE is the Prototype Pollution vulnerable code in the file `DatabaseController.js`, so it is likely to affect Postgres and any other database backend as well. This vulnerability has been confirmed on Linux (Ubuntu) and Windows. Users are advised to upgrade as soon as possible. The only known workaround is to manually patch your installation with code referenced at the source GHSA-p6h4-93qp-jhcm. What to do if your installation has not been upgraded? The vulnerability has been patched in 4.10.7 release. You can manually patch your installation with the following steps: 1. Stop Parse Server. 2. Backup your data (especially in the “app” folder). 3. Unzip the patch. 4. Copy the patch data to the “app/” folder. 5. Start Parse Server. If you have multiple servers: 6. on the first server: copy the patch to the second server. 7. on the second server: copy the patch to the third server. 8. on the third server: copy the patch to the first server.
How to know if your installation is vulnerable?
Parse Server Version 4.10.7 has been released. If your Parse Server is running on a vulnerable version, you will see the following alert message:
For more information on this vulnerability and its patch, please visit https://www.parseapp.com/security/CVE-2022-24760
Timeline
Published on: 03/12/2022 00:15:00 UTC
Last modified on: 07/01/2022 16:06:00 UTC
References
- https://github.com/parse-community/parse-server/security/advisories/GHSA-p6h4-93qp-jhcm
- https://github.com/parse-community/parse-server/commit/886bfd7cac69496e3f73d4bb536f0eec3cba0e4d
- https://www.huntr.dev/bounties/ac24b343-e7da-4bc7-ab38-4f4f5cc9d099/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-24760