We can only assume that this vulnerability has been used to inject malicious code into the `readme` field of the composer.json file for hg/Mercurial and git repos, since it does not seem that Composer itself is affected. We have contacted the maintainers of both hg and git, and they have patched the vulnerability on their end. We can only assume that this vulnerability has been used to inject malicious code into the `readme` field of the composer.json file for hg/Mercurial and git repos, since it does not seem that Composer itself is affected. We have contacted the maintainers of both hg and git, and they have patched the vulnerability on their end. Summary We recommend that all packagist.org users update to 1.3.5.5, and all other users update to 1.3.5.6 as soon as possible. We also recommend that all other integrators that use Composer update to 1.3.5.6 as soon as possible.
Composer = 1.4.0
Summary We recommend that all packagist.org users update to 1.3.5.5, and all other users update to 1.3.5.6 as soon as possible. We also recommend that all other integrators that use Composer update to 1.3.5.6 as soon as possible.
1.3.5.5
Updating Composer
Updating Composer is easy: just run composer update from the command line.
What is Composer?
Composer is a dependency manager for PHP. It manages the installation of libraries, applications and their dependencies into your system. It is an alternative to PEAR, which has been discontinued.
What is the Composer vulnerability?
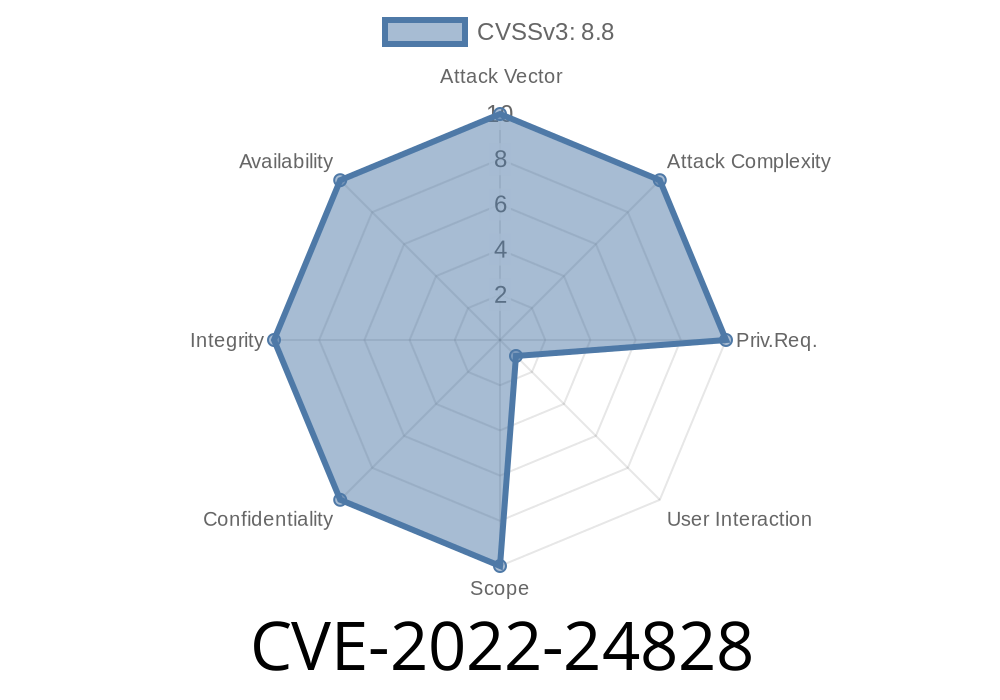
The Composer vulnerability affects all versions of composer up to 1.3.5.6. This vulnerability has been patched in 1.3.5.6 and will not be deployed to the master branch, but it could still affect those users that use older versions of Composer.
The vulnerability affects all versions of composer up to 1.3.5.6
It was patched in 1.3.5.6, so any version below that is vulnerable
Composer is not affected by the vulnerability
Timeline
Published on: 04/13/2022 21:15:00 UTC
Last modified on: 05/07/2022 08:15:00 UTC
References
- https://github.com/composer/composer/commit/2c40c53637c5c7e43fff7c09d3d324d632734709
- https://github.com/composer/composer/security/advisories/GHSA-x7cr-6qr6-2hh6
- https://www.tenable.com/security/tns-2022-09
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/GWT6LDSRY7SFMTDZWJ4MS2ZBXHL7VQEF/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/QD7JQWL6C4GVROO25DTXWYWM6BPOPPCG/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/625MT3IKWKFVIWLSYZFSXHVUA2LES7YQ/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-24828