When using octet-counting, the receiving module will read the maximum number of digits from the log message and save it in a heap buffer. That buffer is then passed to the next function, where the message is logged. If the receiving function reads more data than it is expecting, it will segfault. A fix for this issue is already available in Debian and Ubuntu. As of now, there is no known vulnerable version of Rsyslog. We’ve created a workaround for the Rsyslog team to make the fix available in their next version. You can also disable octet-counting in your Rsyslog installation.
Other Rsyslog Vulnerabilities
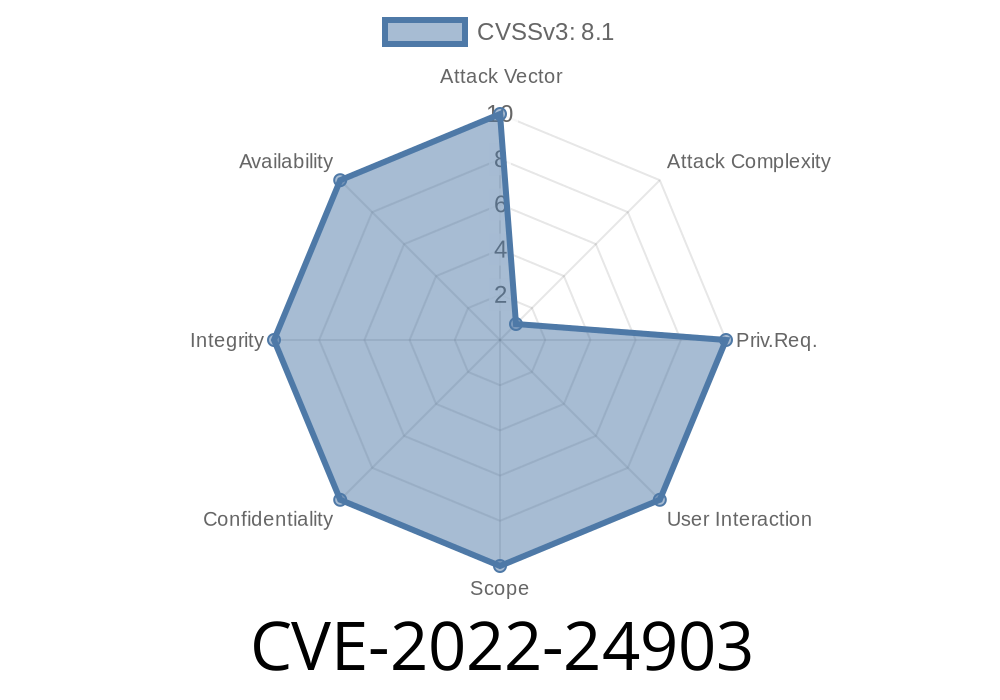
Rsyslog has been identified with a number of vulnerabilities, including CVE-2022-24903. This vulnerability is due to the way Rsyslog handles octet-counting.
The first step in fixing this issue is to ensure that you have upgraded your system to at least version 4.6.8. As of now, there is no known vulnerable version of Rsyslog. We’ve created a workaround for the Rsyslog team to make the fix available in their next version. You can also disable octet-counting in your Rsyslog installation if it's not needed.
Rsyslog: Dependency Finders
Earlier this year, a security researcher found a vulnerability in Rsyslog that could allow an attacker to crash the system. Until now, there has been no known patch for this issue.
Rsyslog: Detecting Sensitive Data in Log Output
One of the most effective methods of keeping your data secure is to use a program called Rsyslog. This program was originally designed to be used as a logging and security platform, but it also has customizable settings that allow you to filter logs by different criteria. One of these settings is called octet-counting.
Octet-counting is a method where Rsyslog will count the number of digits in each log message and save those numbers in a buffer before passing them on to the next function. If the receiving module reads more data than it was expecting, it will segfault. The fix for this issue is already available in Debian and Ubuntu, and there are no known vulnerable versions at this time. There is also a workaround for Rsyslog users if you don’t want to disable octet-counting in your installation.
Timeline
Published on: 05/06/2022 00:15:00 UTC
Last modified on: 06/02/2022 14:15:00 UTC
References
- https://github.com/rsyslog/rsyslog/security/advisories/GHSA-ggw7-xr6h-mmr8
- https://github.com/rsyslog/rsyslog/commit/f211042ecbb472f9d8beb4678a65d272b6f07705
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/GMNNXLCU2UORRVSZO24HL4KMVPK5PHVW/
- https://lists.debian.org/debian-lts-announce/2022/05/msg00028.html
- https://www.debian.org/security/2022/dsa-5150
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-24903