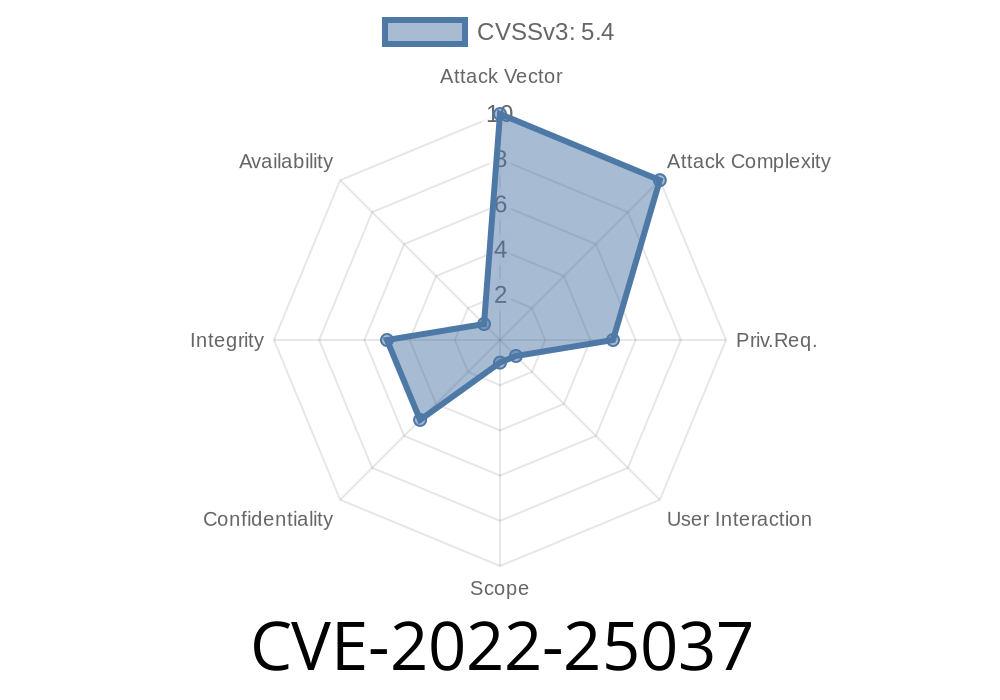
If you use wanEditor — a popular rich text editor for web applications — it’s important to know about CVE-2022-25037, a vulnerability discovered in version 4.7.11. This flaw was patched in versions 4.7.12 and 5., but many websites might still run the outdated version.
This long read unpacks the vulnerability, explains how an attacker could exploit it, and how to protect your applications. We'll see some basic code, proof-of-concept (PoC) exploit details, and reference original sources for deeper dives.
What is wanEditor?
wanEditor is a WYSIWYG (What You See Is What You Get) editor built in JavaScript. Developers use it to give users a friendly interface for writing posts, articles, and comments — much like the text editor found on blogs or forums.
Description of the Vulnerability
CVE-2022-25037 affects wanEditor v4.7.11. It’s a Cross-Site Scripting (XSS) bug rooted in how the editor handles image uploads. When you upload an image, the editor fails to properly sanitize filenames and associated content, letting attackers inject malicious JavaScript.
With XSS, an attacker can run scripts in the user's browser, which might steal cookies, hijack sessions, deface pages, or perform actions as the user.
Original References
- NVD/CVE Record
- wanEditor v4.7.12 Release Notes
- GitHub Advisory Database
How Does the Exploit Work?
To exploit this vulnerability, an attacker could upload an image with a specially crafted filename or payload. The unsanitized filename or payload would then be embedded in the page’s DOM, and the browser would execute the JavaScript.
Let’s say an attacker uploads an image named
<img src=x onerror=alert('XSS')>
If the editor does not sanitize the <img> tag or its attributes, this payload will become active on viewing.
Suppose the upload handler doesn't remove HTML tags or JavaScript event handlers in the filename
<img src="uploads/<img src=x onerror=alert('XSS')>.png">
This would break out of the image context and run JavaScript.
Proof-of-Concept Code
Suppose the vulnerable upload handler accepts any file name and renders markup like this (JavaScript simplified):
// Simulated vulnerable image processing
function insertImage(fileName) {
// Raw, unsanitized image tag insertion!
let imgTag = <img src="uploads/${fileName}">;
document.getElementById('editor').innerHTML += imgTag;
}
If an attacker uploads a file called <img src=x onerror=alert('Hacked!')>.png, the function builds
<img src="uploads/<img src=x onerror=alert('Hacked!')>.png">
Rendering this in the browser immediately fires the onerror event, running the attacker's code.
Responsible Mitigation
wanEditor developers addressed this in v4.7.12 and later (including v5) by sanitizing input and filenames:
Upgrade to at least wanEditor v4.7.12, preferably v5.
- Filter/escape filenames on both server and client sides.
Safe Code Example
function escapeHTML(str) {
return str.replace(/[&<>"']/g, function(match) {
return ({
'&': '&',
'<': '<',
'>': '>',
'"': '"',
"'": '''
})[match];
});
}
function insertImageSecure(fileName) {
let safeFileName = escapeHTML(fileName);
let imgTag = <img src="uploads/${safeFileName}">;
document.getElementById('editor').innerHTML += imgTag;
}
Further Reading & Links
- CVE-2022-25037 at NVD
- wanEditor Changelog with v4.7.12 Fix
- DOMPurify: Fast & Secure HTML Sanitizer
- XSS Prevention Cheat Sheet – OWASP
Final Advice
Always keep dependencies updated and sanitize everything users can upload or submit. Security is about layers — don’t let that one outdated widget ruin your app's reputation!
If you suspect your site might be vulnerable, update now and review your file upload and HTML rendering logic.
Timeline
Published on: 05/31/2024 16:15:09 UTC
Last modified on: 08/19/2024 19:35:02 UTC