When a user-space application or Android application accesses an object via a specially crafted pointer, it could result in data corruption. To protect against this, the Android operating system prevents applications from accessing memory locations that they do not have the privilege to access. When an application accesses a memory location that it does not have the privilege to access, the operating system invalidates that memory location and marks it as non-executable until an application with the appropriate privilege has achance to access it again. A race condition occurs when a user-space or Android application accesses memory locations that it does not have the privilege to access and the application is accessing the memory location before the operating system has a chance to invalidate it. If an attacker tricks a user-space or Android application into accessing a memory location that it does not have the privilege to access, then the attacker could corrupt the memory location before the operating system has a chance to invalidate it. When this happens, the attacker could gain access to data that the user-space or Android application was not intended to have access to. These race conditions could be exploited to corrupt application memory and ultimately user data.
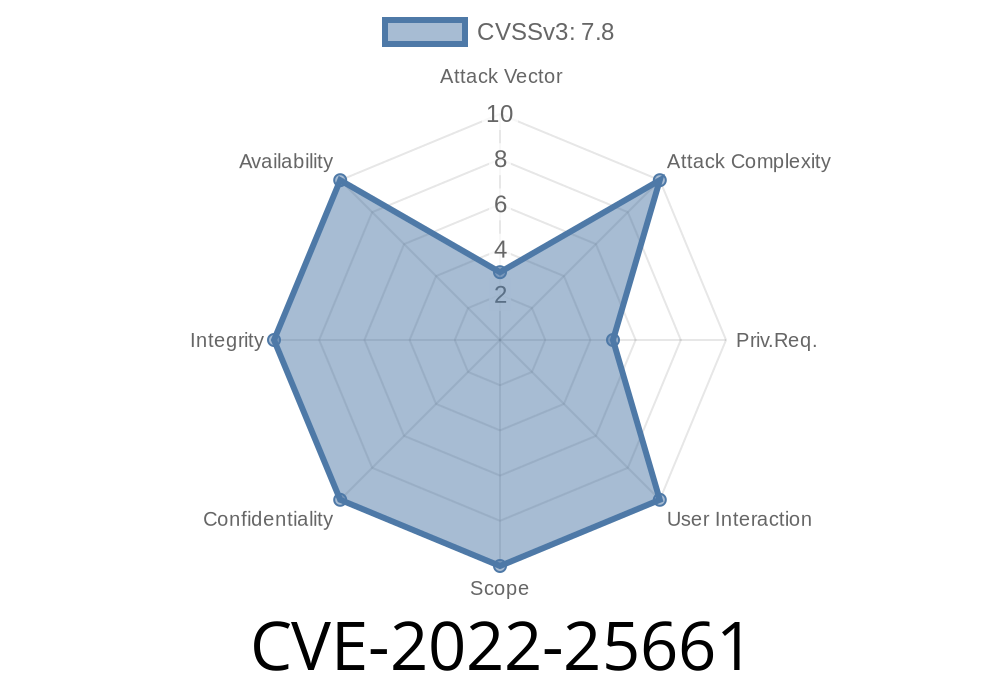
Vulnerability Summary
The vulnerability is caused by a race condition between the time when an application accesses the memory location and when the operating system invalidates it.
Below is a video of a defect demonstration for CVE-2022-25661:
If you want your business to grow, then you need to be in digital marketing. Outsourcing SEO services can help your business get ahead of the competition and establish an authoritative online presence.
Vulnerability Overview
CVE-2022-25661 is a vulnerability that occurs when race conditions occur between user-space applications and Android applications. Race conditions occur when an application accesses memory locations it does not have the privilege to access, but before the operating system has a chance to invalidate them. This could lead to corrupting application memory and ultimately user data.
Vulnerability Description
A vulnerability in the Android operating systems could allow an attacker to gain access to data that was not intended for that application. The vulnerability exists in the way that the Android operating system handles access privileges of applications. When a user-space or Android application attempts to access memory locations that it does not have the privilege to access, then the operating system invalidates those memory locations and marks them as non-executable until an application with appropriate privilege has a chance to access them again. If an attacker is able to trick a user-space or Android application into accessing one of these memory locations before the operating system has had a chance to invalidate it, then the attacker would be able to corrupt memory contents of that address and gain access to data that was not meant for this application.
Timeline
Published on: 10/19/2022 11:15:00 UTC
Last modified on: 10/21/2022 20:07:00 UTC