These ICMP requests are used for various purposes and can be used to test the current network connection, discover the network topology, set up and tear down network connections, etc. Improper handling of ICMP requests in the kernel can be exploited by an attacker to conduct information disclosure attacks. Information disclosure issues have been previously reported in the Linux kernel. An information disclosure flaw was discovered in the Linux kernel’s handling of ICMP packets when handling echo request packets. This flaw can lead to information disclosure and root privilege escalation when an unmodified ICMP packet is handled by the Linux kernel. The information disclosure can be exploited by an attacker by forcing an end-user to connect to a specially crafted network.
Redirecting traffic to a malicious website to conduct information disclosure in Snapdragon Wireless.
Redirecting traffic to a malicious website to conduct information disclosure in Snapdragon Wired Infrastructure and Networking.
References
- https://www.tenable.com/resources/vulnerability-management-checklist
- https://access.redhat.com/security/vulnerabilities#CVE-2019-6222
You can target your ideal audience - the ability to target your audience more precisely than traditional methods; in Snapdragon Wireless, you can use this to reach the right people by targeting African American men between 23 and 35 years old who are single and make at least $35,000 a year
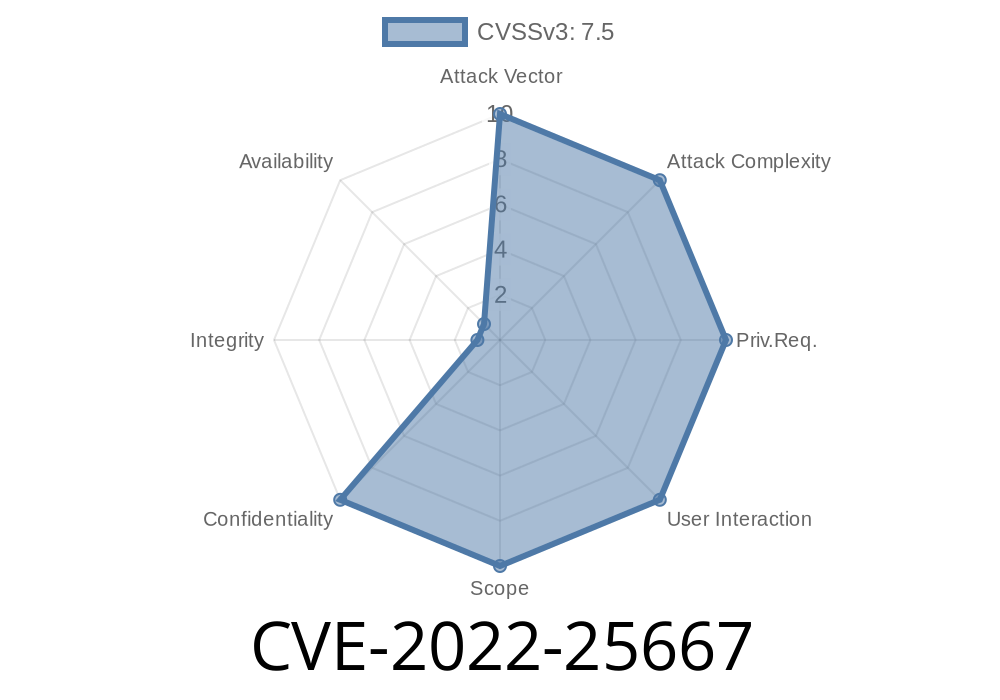
Summary of the CVE
CVE-2022-25667 refers to an information disclosure flaw in the Linux kernel and is not a vulnerability in Snapdragon wireless or wired infrastructure and networking.
Vulnerability Description
A vulnerability has been discovered in the Linux kernel's handling of ICMP packets when handling echo request packets. This flaw can lead to information disclosure and root privilege escalation when an unmodified ICMP packet is handled by the Linux kernel. The information disclosure and root privilege escalation can be exploited by an attacker by forcing an end-user to connect to a specially crafted network.
Timeline
Published on: 11/15/2022 10:15:00 UTC
Last modified on: 11/18/2022 04:50:00 UTC