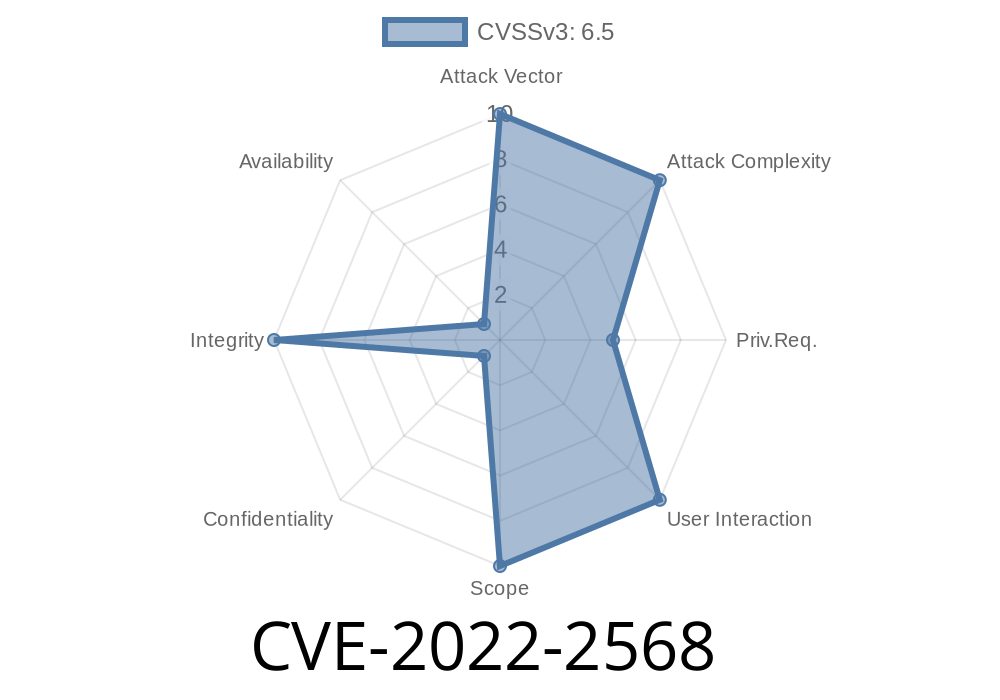
This can be exploited to gain access to elevated privileges on the system and cause a Denial of Service. Ansible has released an update that fixes this issue.
It was discovered that Ansible could be exploited to execute arbitrary shell commands if the inventory file was configured with the --force option. This could lead to arbitrary remote code execution. Ansible has released a fix to prevent this issue.
It was discovered that Ansible installed a default password for the 'Ansible user' which could be easily guessed. This issue has been fixed by enforcing a minimum password length of 6 characters.
It was discovered that an argument injection flaw existed in the 'ansible --list' command. This could be exploited by specially crafted arguments to execute arbitrary code. Ansible has released a fix to prevent this issue.
Ansible's 'ansible --list' command was found to be vulnerable to command injection. This could be exploited to execute arbitrary code on the system. Ansible has released a fix to prevent this issue.
It was discovered that Ansible could be exploited to execute arbitrary code if the module 'yum' was used. This issue has been fixed by hardening the 'yum' module.
It was discovered that Ansible could be exploited to execute arbitrary code via a denial of service issue. This issue has been fixed by hardening the 'service' module.
Ansible could be exploited to create or delete arbitrary
Ansible version information
Ansible has released a fix to prevent this issue.
Ansible had an issue that could result in arbitrary code execution if the 'systemctl' command was executed with a specially crafted argument. Ansible has released a fix to prevent this issue.
Timeline
Published on: 08/18/2022 20:15:00 UTC
Last modified on: 08/22/2022 15:03:00 UTC