multimedia applications on devices with Snapdragon chips is possible. It can be exploited to cause a device crash, obtain sensitive information, or to otherwise disrupt the user experience. A vulnerable application on a device with a Snapdragon chipset may trigger a kernel crash with a Rogue Stack Segment (SSS) that may lead to a compromised device. In particular, the SSS is a section of code in a process’s address space that is not part of the regular stack. SSSs can be used to corrupt system memory and to gain unauthorized access to data. A SSS is a potential threat to any operating system. They can be exploited to cause arbitrary code execution. To mitigate SSS exploitation, maintain code integrity, and detect SSS exploitation, it is essential to maintain code maintainability and test the integrity of your code.
Overview
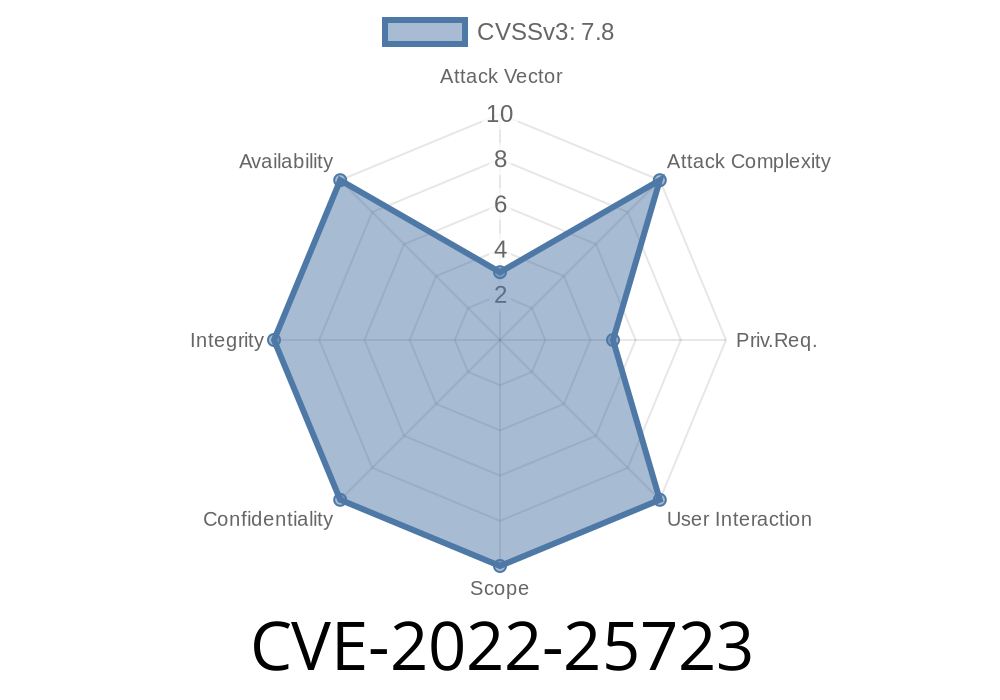
The vulnerability is known as CVE-2022-25723 and affects devices with Snapdragon chips. The vulnerability is a privilege escalation bug that, when exploited, can lead to the device crashing or sensitive information being disclosed. Although the vulnerability is in Qualcomm’s code and not in the operating system, it may be triggered through an application on the device with Snapdragon chips.
What’s a rogue stack segment?
A stack segment is a piece of memory in the process’s address space that is not part of the regular stack. A SSS is a section of code in a process’s address space that could be used to corrupt system memory and to gain unauthorized access to data. They can be exploited to cause arbitrary code execution. In particular, the SSS is a section of code in a process’s address space that is not part of the regular stack.
How does a rogue stack segment cause a kernel panic?
A kernel panic occurs when a process is unable to run smoothly. A rogue stack segment (SSS) may cause a kernel panic when it corrupts system memory and causes the device to crash. The SSS may be inserted into the address space of a process by an attacker. In order to exploit this vulnerability, the attacker must have access to the system service used to load the application that contains the SSS or must have access to an application that has been compromised with a SSS in its code space.
Exploitation and Mitigation Strategies:
Code Integrity and Detecting SSSs
Code integrity is the process of ensuring that the compiled code, or object code, has not been modified. Code maintainability is a measure of how difficult it is to modify an application's source code. A code maintainability test attempts to determine whether there are any changes to the source code which would break compilation or execution. An exploitability test verifies that an executable file does not contain any errors which would be exploited by a malicious user. These tests can help detect vulnerabilities such as stack segment overruns.
To mitigate SSS exploitation, maintain code integrity, and detect SSS exploitation, it is essential to maintain code maintainability and test the integrity of your code.
Timeline
Published on: 10/19/2022 11:15:00 UTC
Last modified on: 10/20/2022 21:21:00 UTC