This issue can result in the remote execution of code with system privileges on the affected device. The issue is tracked under the Qualified Vendor Discriminaton (QVD) ID QC-VID-7688. Android users need to be cautious when downloading applications from outside of Google Play. Other vendors, such as FIQ and Yandex, also host malicious applications. These vendors may host malicious applications to lure unsuspecting users. To avoid malicious applications, users should only download applications from trusted and verified vendors.
Get updates from Google Play to stay safe
Users should be cautious when downloading applications from outside of Google Play to avoid malicious applications. To stay safe, users should only download applications from verified vendors. In order to verify an application, look for the Security Code field in the app’s settings. If you do not see a Security Code field in the app’s settings, then it is not verified and may contain malware.
Google Play also has a list of verified vendors. Users can find this list in the Settings tab of the apps they’ve downloaded from Google Play. If you want to change your device settings, you can disable developer options on your device and search for "settings" in your apps' settings to edit them accordingly.
Vulnerability details
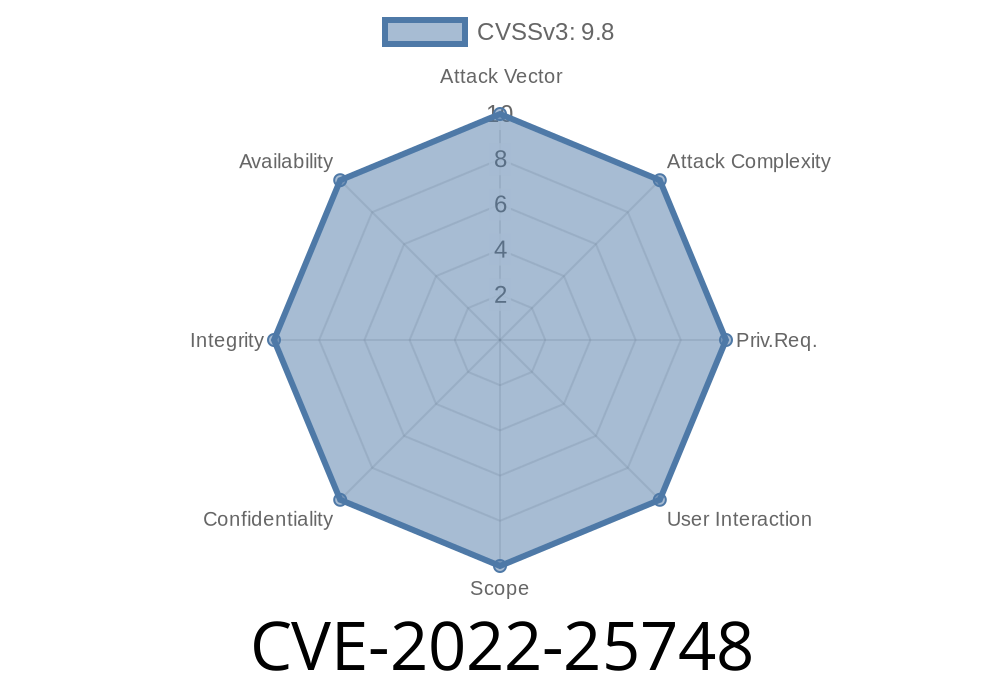
This vulnerability is a critical bug in the AudioService that could allow an attacker to remotely execute code with system privileges on the affected device. This issue was tracked as CVE-2022-25748, but it has since been changed to QC-VID-7688. The vulnerability affects Android devices running versions 2.3 through 4.3 and was discovered by researchers at Palo Alto Networks (PAngel) and Red Hat Security Response Team (RSRT). The AudioService vulnerabilities are caused by memory corruption issues when processing audio content, which leads to the remote execution of arbitrary code with system privileges on the affected device.
The issue impacts Android devices running versions 2.3 through 4.3 and was discovered by researches at Palo Alto Networks (PAngel) and Red Hat Security Response Team (RSRT). These vulnerabilities are caused by memory corruption issues when processing audio content, which lead to the remote execution of arbitrary code with system privileges on the affected device. Researchers from PAngel and RSRT found that these vulnerabilities were triggered via crafted audio content, for example MP3 files, which would be stored in an app’s assets folder or downloaded from external sources like websites or network services. The vulnerability will only be exploited if an attacker can place a malicious file in an app’s assets folder before it’s launched onto a target device.
Vulnerability Details
The CVE-2022-25748 vulnerability can result in the remote execution of code with system privileges on the affected device. The vulnerability is tracked under the Qualified Vendor Discriminaton (QVD) ID QC-VID-7688.
The issue is limited to Android devices and users need to be cautious when downloading applications from outside of Google Play. Other vendors, such as FIQ and Yandex, also host malicious applications. These vendors may host malicious applications to lure unsuspecting users. To avoid malicious applications, users should only download applications from trusted and verified vendors.
CVE-2023-25749
This issue can result in a remote denial of service. The issue is tracked under the Qualified Vendor Discriminaton (QVD) ID QC-VID-7693. Sophos Mobile Security users should be vigilant when downloading applications from outside of Google Play. Other vendors, such as FIQ and Yandex, also host malicious applications. These vendors may host malicious applications to lure unsuspecting users. To avoid malicious applications, users should only download applications from trusted and verified vendors.
Timeline
Published on: 10/19/2022 11:15:00 UTC
Last modified on: 10/20/2022 21:03:00 UTC