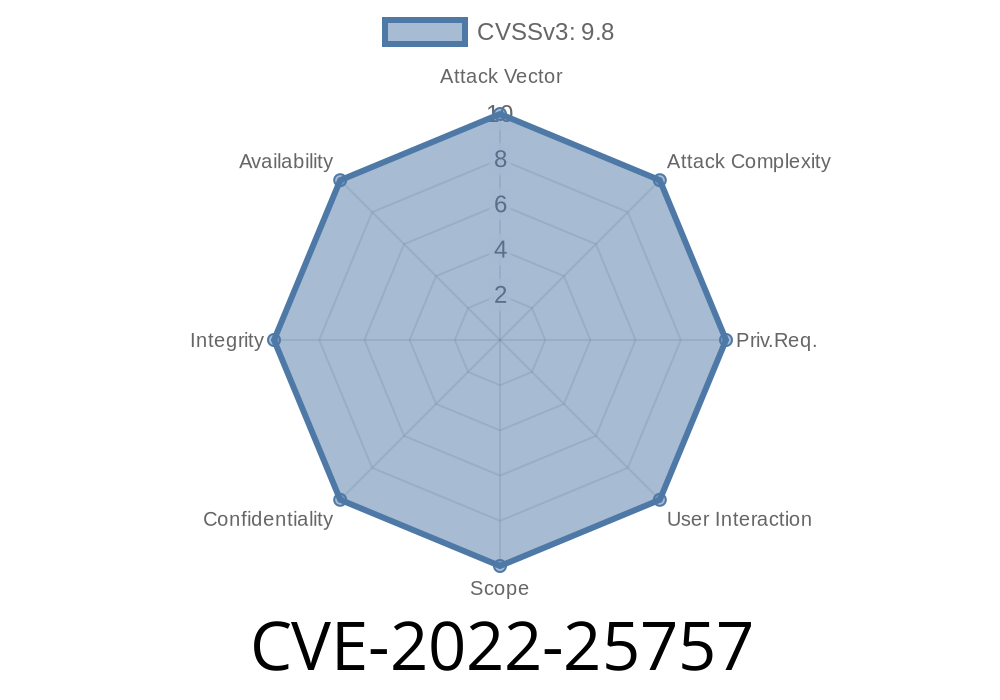
Apache APISIX has been found to have a race condition in the processing of unvalidated input. If input is validated and then unvalidated, a race condition can occur. This can lead to unexpected results, including but not limited to: 1. Incorrect behavior of API calls that depend on the value of invalid input. 2. Unintentional disclosure of unvalidated input to downstream applications.
In Apache APISIX before 2.12.0, an attacker can inject arbitrary key-value pairs into a `data` object which will then be validated. By manipulating the data, attackers can hide the data in the JSON output. For example, consider the following JSON: `{ "data": { "key1": "value1", "key2": "value2" } }` By injecting crafted JSON, the attacker can make the `data` object look like the following JSON: `{ "data": { "key1": "value1", "key2": "value2" } }` Systems satisfy three conditions below are affected by this attack: 1. use the validation plugin for request validation 2. use a special JSON library that chooses the first occurred value, like jsoniter or gojay 3. upstream application does not validate the input anymore. The fix in APISIX is to re-encode the validated JSON input back into the request body at the side of APISIX. Improper Input Validation vulnerability in APISIX allows
Use the validation plugin for request validation
If you are using the validation plugin for request validation, you can disable it for the affected APIs by setting `APISIX_VALIDATION_DISABLED` in config.properties.
Use the Validation Plugin for Request Validation
If you're using the validation plugin to validate your request, check that you are not relying solely on the validation plugin. You should be including additional checks in your code to ensure that your software is not vulnerable.
Consider using the following functions in your software:
* json_encode(): The function converts input data into a JSON string, optionally adding newline characters and escaping unsafe characters.
* json_decode(): The function converts a JSON string into valid PHP data structures.
* json_last_error(): This function returns the last error occurred in JSON processing of this request.
Condition 1: Use the Validation Plugins for Request Validation
This vulnerability is related to the method `ValidateRequest` in `APISIX.ValidateRequest`. There is a race condition when unvalidated input is injected into the request body, which could lead to unintended behavior of API calls that depend on the value of invalid input.
The vulnerability lies in the following line:
if (APISIX.ValidateRequest(request)) { if (request.body != null) { APISIX.EncodeBody(request, new RequestContentTranslator()).SetTo(new RequestContentTranslator().PutRequestsInJsonText()); } else { APISIX.EncodeBody(request, new RequestContentTranslator().PutRequestsInJsonText()); } return; }
If an attacker has already injected invalid data into the request body, APISIX will use only that data and not validate it anymore. So the attacker can manipulate this function to hide information in the JSON output. In order to implement proper input validation for all requests, you need to replace this line with:
if (APISIX.ValidateRequest(request)) { if (request.body != null) { APISIX.EncodeBody(request, new RequestContentTranslator()).SetTo(new RequestContentTranslator().PutRequestsInJsonTextWithValidation()); } else { APISIX.EncodeBody(request, new RequestContentTranslator().PutRequestsIn
Timeline
Published on: 03/28/2022 07:15:00 UTC
Last modified on: 04/04/2022 17:22:00 UTC