HDF5 is a high performance data storage format used in a wide-range of fields such as scientific research, genomics, and big data analytics. HDF5 is open-source software, licensed under the HDF license. HDF5 has been widely used in Linux, OS X, and Microsoft Windows systems. An attacker can exploit this vulnerability by supplying a specially-crafted GIF file to an unsuspecting user. If a user clicks on the attack vector, it will lead to code execution in the context of the user. This can be done by emailing a malicious GIF file to the target. Exploiting this issue is fairly easy, as an attacker just needs to supply a malicious GIF file. An attacker can exploit this issue by sending a malicious GIF file to the user. When a user opens the malicious file, it will lead to code execution in the context of the user. This can be done by emailing a malicious GIF file to the target. Exploiting this issue is fairly easy, as an attacker just needs to supply a malicious GIF file. An attacker can exploit this issue by sending a malicious GIF file to the user. When a user opens the malicious file, it will lead to code execution in the context of the user. This can be done by emailing a malicious GIF file to the target. Exploiting this issue is fairly easy, as an attacker just needs to supply a malicious GIF file. An attacker can exploit this issue by sending a malicious GIF file
Vulnerability overview
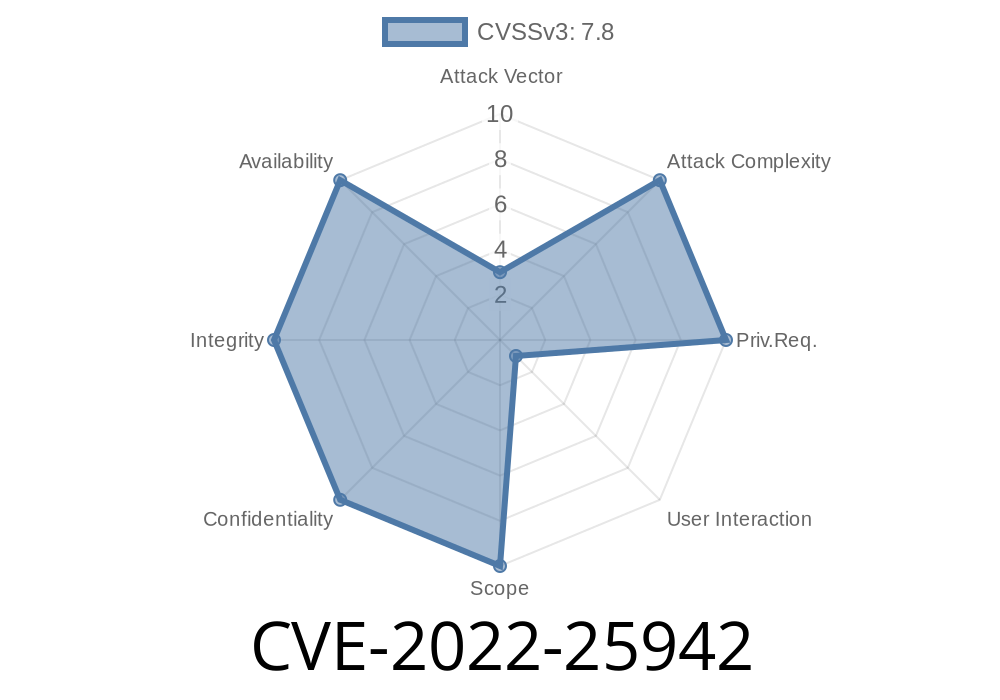
The vulnerability allows attackers to execute arbitrary code on the target's machine.
Bug Bounty Program
It is a good idea to subscribe to the Bug Bounty Program. The bug bounty program will give you the tools you need to protect your business as well as the valuable information you need in order to identify vulnerabilities in your software.
When you join the Bug Bounty Program, by participating in a security audit, you allow Google and other members of the program to review your site's code and its software. This will give them an opportunity to verify the integrity of your website.
Timeline
Published on: 08/22/2022 19:15:00 UTC
Last modified on: 08/23/2022 17:11:00 UTC