The vulnerability is due to improper handling of access control rules, which may be exploited by an unauthenticated attacker to rewrite existing files on the file system. To exploit the vulnerability an attacker must have the privilege to change NTP GPS settings. The pfSense software may be installed on a wide range of hardware, depending on the version and hardware specifications of the hardware. The following hardware specifications are supported: - Intel Pentium, Celeron, or Xeon processors - Intel x86-compatible AMD CPUs - ARMv7 processors - 8- or 16-Core AMD Opteron - 1- or 2-Celeron or Pentium-compatible processors - Intel x86-compatible ARMv7 processors - 8- or 16-Core Intel Xeon - 1- or 2-Celeron or Pentium-compatible processors - ARMv7 processors - 32- or 64-Core ARMv8 The following operating systems are supported: - Windows - FreeBSD - OpenBSD - NetBSD - Darwin - Android - Linux - FreeBSD - OpenBSD - NetBSD - Darwin - Android - Linux - FreeBSD - OpenBSD - NetBSD - Darwin - Android - Linux - FreeBSD - OpenBSD - NetBSD - Darwin - Android - Linux - FreeBSD - OpenBSD - NetBSD - Darwin - Android - Linux - FreeBSD - OpenBSD - NetBSD - Darwin - Android - Linux - FreeBSD - OpenBSD - NetBSD - Darwin - Android - Linux - FreeBSD - OpenBSD - NetBSD - Darwin
Vulnerability
An issue in the software used by the firewall pfSense has been identified that could allow an unauthenticated attacker to access the file system. This vulnerability was discovered after a public disclosure for CVE-2019-9235, which allowed an unauthenticated attacker to gain root access to the file system.
Vulnerability description
There is a vulnerability in pfSense software versions 2.3.1 through to 2.4 that can allow authenticated attackers to recover files on the file system by exploiting a failure with access control rules. The vulnerability is due to improper handling of access control rules, which may be exploited by an unauthenticated attacker to write new or create existing files on the file system with SYSTEM privileges. As of the time of writing, pfSense has not fixed this issue and it is unknown if they will fix it at any point in the future.
Vulnerable Instance Detection
This vulnerability can be exploited remotely. It is possible to detect vulnerable instances by checking for the presence of the following in /var/log/messages on the system:
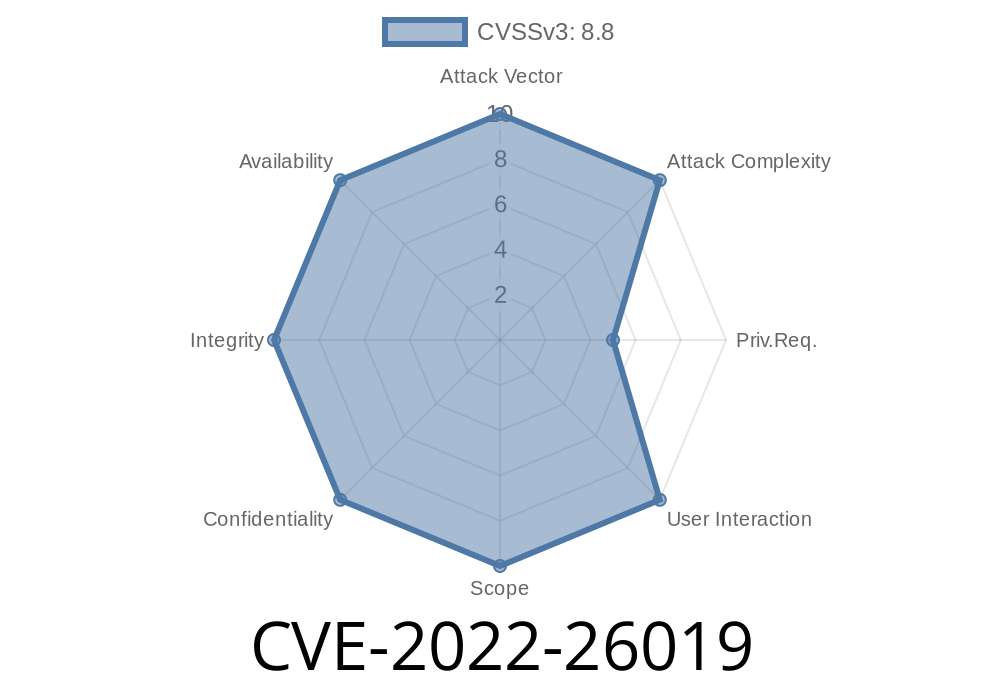
- "CVE-2022-26019: Authenticated Denial of Service vulnerability."
- "pfSense version 2.3.1 (pfSense_2.3.1_amd64) pfSense date: 2019/01/24 19:11"
- "OS version not found."
Timeline
Published on: 03/31/2022 08:15:00 UTC
Last modified on: 04/07/2022 20:36:00 UTC