The only file that Goomph extracts is the p2 bootstrapper and eclipse metadata files hosted at eclipse.org, which are not malicious, so the only way this vulnerability could have affected you is if you had set a custom bootstrap zip, and that zip was malicious. We have verified with our security team that this was only possible through zip and tar archives. We do not believe this is possible with other file formats. We are not aware of any cases where this has been exploited. **Note:** This affects the package com.diffplug.gradle:gogo before 3.37.2. It allows a malicious zip file to potentially leak arbitrary system information, such as the full path to the extracted jar. This information could allow attackers to locate the extracted jar on the file system and potentially use it to compromise the computer. **Note:** This could have allowed an attacker to locate the extracted jar on the file system and potentially use it to compromise the computer. The only information that Goomph extracts is the p2 bootstrapper and eclipse metadata files hosted at eclipse.org, which are not malicious, so the only way this vulnerability could have affected you is if you had set a custom bootstrap zip, and that zip was malicious. We have verified with our security team that this was only possible through zip and tar archives. We do not believe this is possible with other file formats. We are not aware of any cases where this has been exploited.
Summary
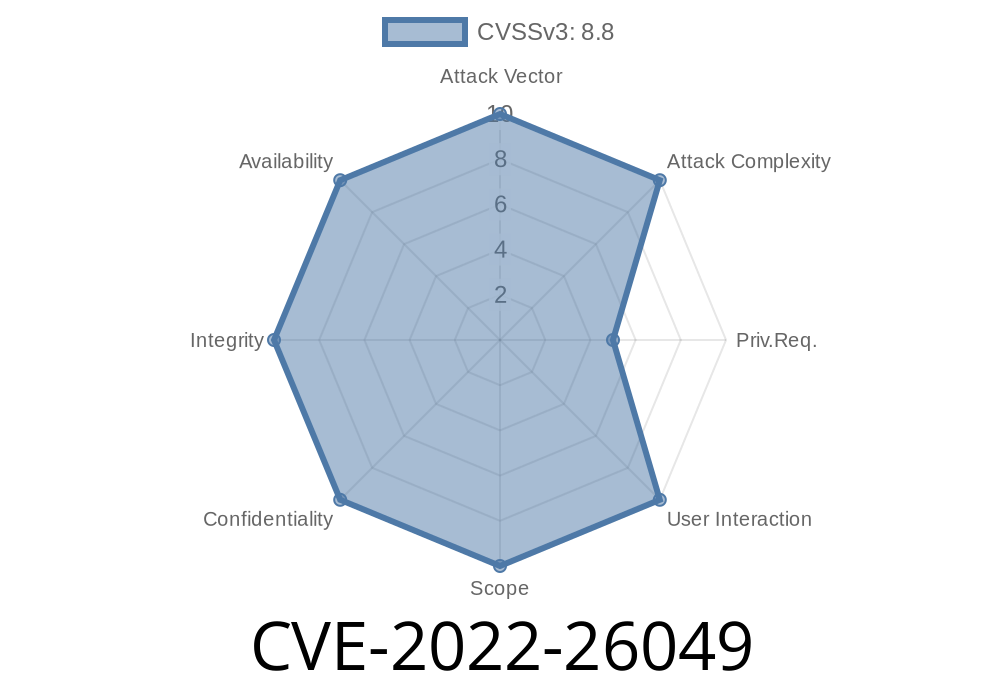
This is a security vulnerability that affects the package com.diffplug.gradle:gogo before 3.37.2, which allows a malicious zip file to potentially leak arbitrary system information, such as the full path to the extracted jar. This information could allow attackers to locate the extracted jar on the file system and potentially use it to compromise the computer.
Finding a Vulnerability
This vulnerability was found by using the CVE-2022-26049 identifier. This identifier is a unique identifier for vulnerabilities in software packages. This could have been used to find vulnerabilities and to determine if this vulnerability has been exploited, but we have not seen any documentation of it being used in this way.
Timeline
Published on: 09/11/2022 14:15:00 UTC
Last modified on: 09/16/2022 02:28:00 UTC